Oracle WebLogic insecure deserialization vulnerability actively being exploited in the wild
An insecure deserialization vulnerability has been reported in Oracle Weblogic. This vulnerability is due to
insufficient validation of user requests. A remote, unauthenticated attacker can exploit this vulnerability by sending a crafted request to a vulnerable server. Successful exploitation can result in arbitrary code execution under the security context of the affected server.
Oracle WebLogic is one of the widely used Java application servers. It helps to build and deploy large enterprise Java applications.
Serialization is the process of translating application data such as objects into a binary format that can be stored and reused by the same application or transmitted over the network to be used by another application.
Deserialization is the reverse of that process that takes data structured from some format, and rebuilding it into an object. By running deserialization, we should be able to fully reconstruct the serialized object.
Insecure Deserialization is a vulnerability that occurs when user input data is not sanitized or validated properly. This untrusted user data can be used to abuse the logic of an application, inflict a denial of service (DoS) attack, or even execute arbitrary remote code execution upon it being deserialized. Hence attackers craft the serialized data and the attack depends on what the application code does with the data.
CVE-2020-2883:
The vulnerable class is ReflectionExtractor in the Coherence library coherence.jar.
This vulnerability is due to a lack of filtering on deserialization of the ReflectionExtractor class from the Coherence library bundled with WebLogic. It ensures that dangerous classes are not deserialized by checking against the blacklisted ones implemented by WebLogic. However, if a class is not in the blacklist, it allows deserialization. In this case, the Coherence library ReflectionExtractor class includes a potentially dangerous method, extract() which accepts an arbitrary object as a parameter and calls the method, allowing the invocation of an arbitrary method. A remote, unauthenticated attacker can exploit this vulnerability by sending a serialized request which contains a ReflectionExtractor Java object.
A quick search on Shodan reveals a little over 4,600 Oracle WebLogic servers available online. These servers are mostly present in U.S, China, Iran, Germany, and India. The majority of these servers use unpatched versions that can be exploited by unauthenticated attackers.
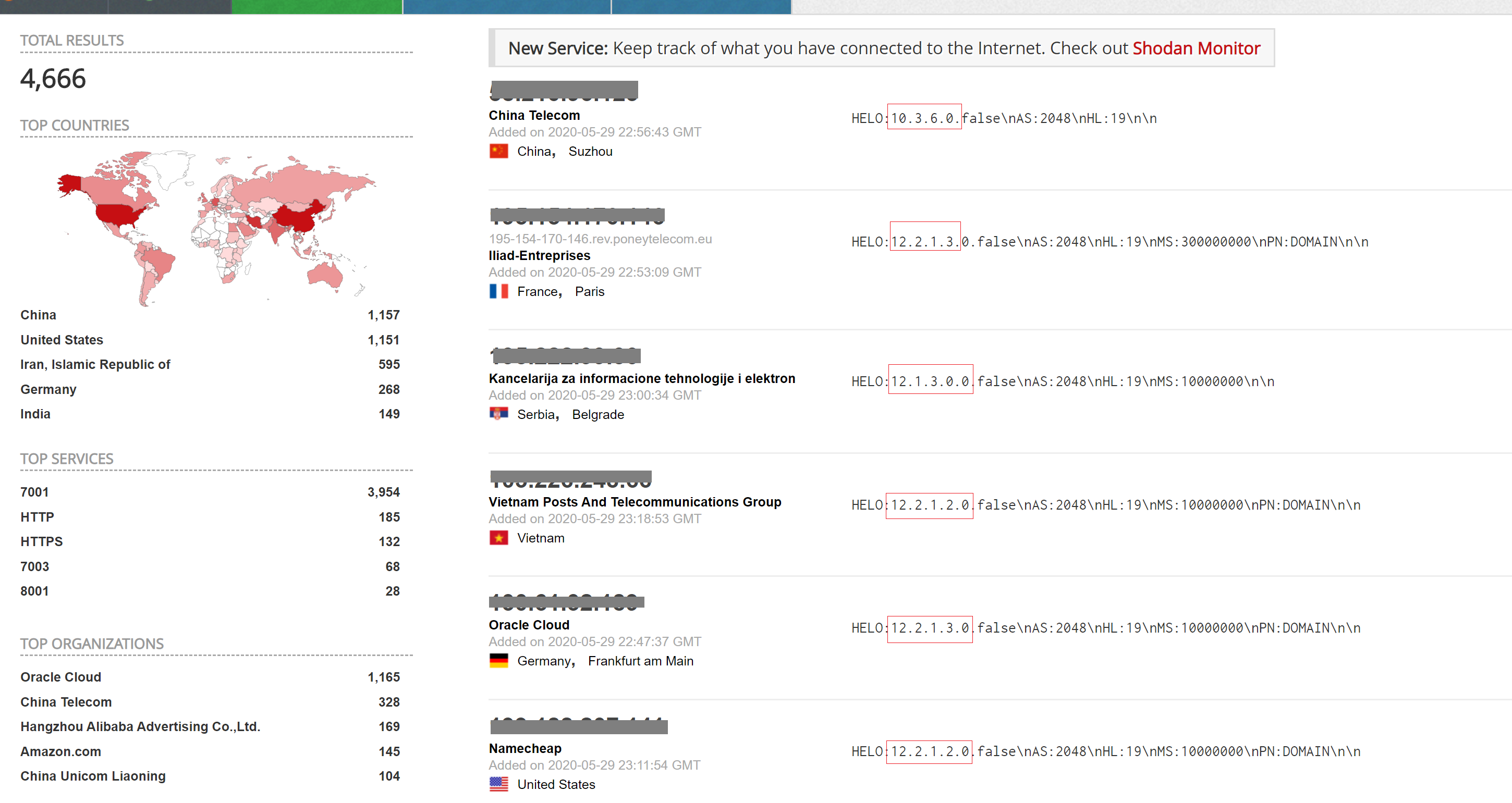
Oracle WebLogic Server versions 10.3.6, 12.1.3, 12.2.1.3, and 12.2.1.4 are affected by this vulnerability.
Fix:
This issue is addressed in the Oracle’s April 2020 critical patch update.
SonicWall Capture Labs Threat Research team provides protection against this exploit with the following signatures:
IPS: 15000 Oracle WebLogic Server Insecure Deserialization 19
IPS: 15025 Oracle WebLogic Server Insecure Deserialization 20
