WiKID Enterprise 2FA Server SQL Injection Vulnerability
WiKID Enterprise 2FA (two factor authentication) Enterprise Server through 4.2.0-b2047 is vulnerable to SQL injection through the searchDevices.jsp endpoint (CVE-2019-16917)
WiKID Enterprise 2FA
WiKID 2FA (Two-factor Authentication) Enterprise Server is an authentication system which can work with services like RADIUS server, LDAP directory, and AD Domain server to provide two-factor authentication solutions for enterprise environment. It offers several features such as handling two-factor authentication requests and validation, passcode request, user management, certificate management, and administrative preferences.
Sql injection
A SQL injection attack consists of insertion or “injection” of a SQL query via the input data from the client to the application. A successful SQL injection exploit can read sensitive data from the database, modify database data (Insert/Update/Delete)
The Vulnerability(CVE-2019-16917)
Sql Injection vulnerability exists in WiKID Enterprise 2FA.It fails to sanitize the uid and domain parameters. The SQL query constructed in the buildSearchWhereClause function.The WiKID Enterprise server provides a graphical user interface to manage administrative monitoring via “https://<server>/WiKIDAdmin/”
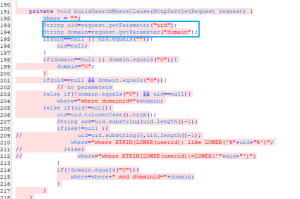
If we look at the buildSearchWhereClause function of searchDevices.jsp , we see that the id and domain are used directly to construct the sql queries. The id and domain parameters are not sanitized and used directly which makes this function vulnerable to sql injection attacks.
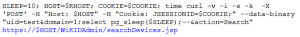
The backend database is postgres which accepts stacked queries.One example of an attack could look like which will cause the database to sleep for 10 seconds.
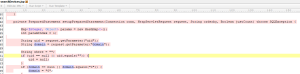
This Vulnerability is patched. If we compare the patched code vs the vulnerable code we see that the patched version of searchDevices.jsp uses PreparedStatement to sanitize the uid and domain parameters before forming a sql query . Prepared statements ensure that an attacker is not able to change the intent of a query, even if SQL commands are inserted by an attacker.
SonicWall Capture Labs Threat Research team provides protection against this threat with the following signature:
IPS 14569 : WiKID Enterprise 2FA SQL Injection
IPS : SQL Injection Attack
SonicWall WAF has been designed to provide protection against this exploit by default.
