Egregor Ransomware
Overview:
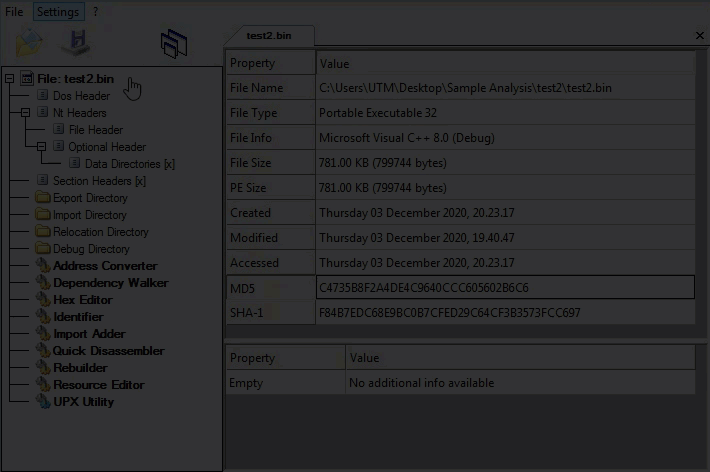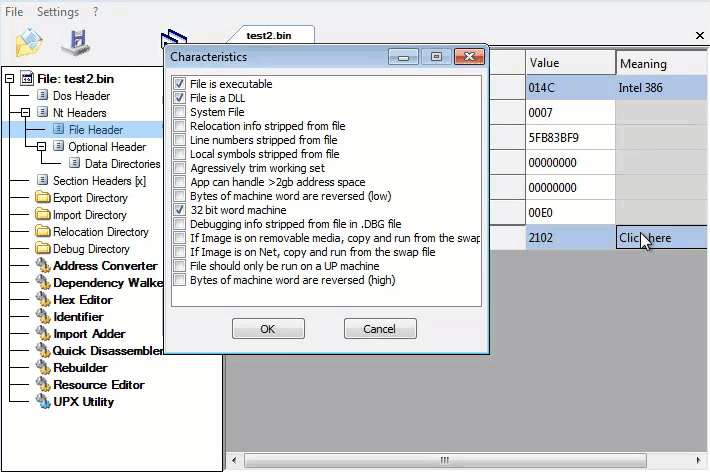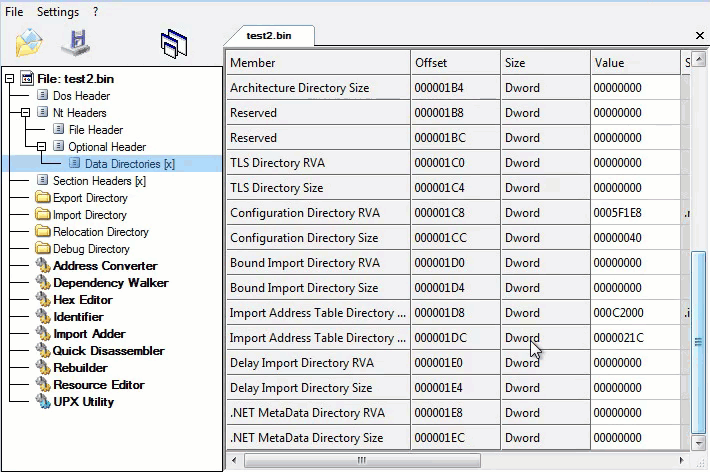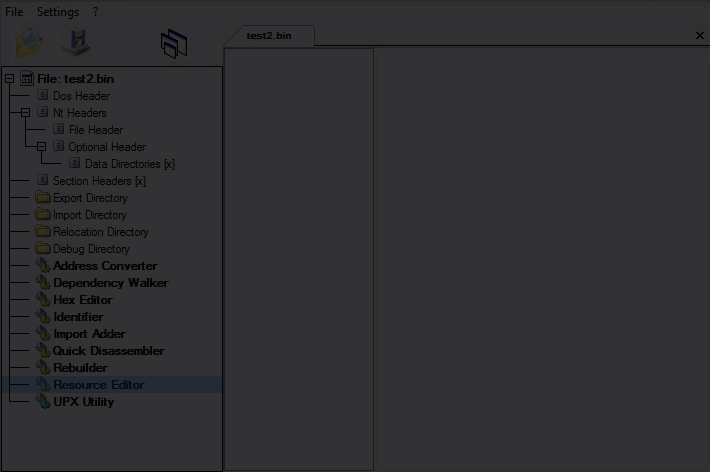
SonicWall Capture Labs Threat Research Team recently found a new sample and activity for Egregor Ransomware. The Egregor sample below is a library (DLL) that contains code and data that can be used by more than one program at the same time. The library is highly obfuscated and encrypted using Salsa20, ChaCha Stream Cipher and RSA encryption. This makes analysis difficult to bypass from the reverse engineering and debugging point of view.
The library contains export functions that are required to be called from other stages of the infection chain. The export function parameters usually accept the key or password to unlock, deobfuscated, and decrypt the code sections. Once the sample is done unwinding, it will release the payload hidden inside. The key and/or password is normally unique or specific to each sample. This key and/or password is always located somewhere inside the sample. It’s up to the researcher to locate the desired information inside.
The command we can use to bypass the distribution methods below for debugging:
regsrv32.exe path_to_dll DllRegisterServer param1 param2
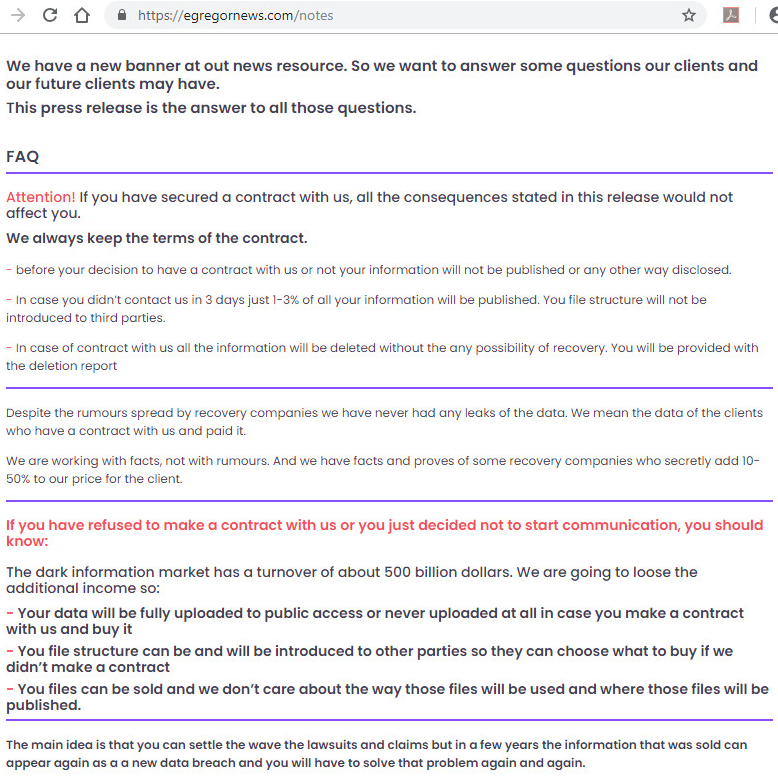
Egregor, releases stolen data on their website egregornews to increase pressure on the victim to pay the ransom. Egregor News, is used to post the names and domains, along with data sets of Egregor victims.
Distribution Methods & Tactics:
- Cobalt Strike
- RDP Exploit
- Phishing
- CVE-2020-0688
- CVE-2018-8174
- CVE-2018-4878
- CVE-2018-15982
- QBot
- Ursnif
- icedID
RaaS News Website:
Stage 1, Static Information:
ChaCha / Salsa20 Initial State Information:
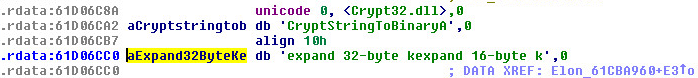
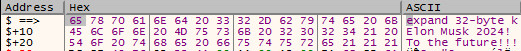
Stage 1: uses a implementation of ChaCha(2008)/Salsa20(2005) as the main encryption. The “nothing-up-my-sleeve number”, which is used to pinpoint ChaCha or Salsa20 is “expand 32-byte k” This is considered the algorithm constant and “nothing-up-my-sleeve number”. When you see this constant its considered a 256 bit implementation. The 32-byte constant can be seen below:
The key used for unlocking stage 1:
“Elon Musk 2024! To The Future!!!” and “SpaceX!!”
The words are filtered, parsed and rearranged for parts of the ChaCha decryption stage.
Stage 1, Dynamic Information:
Start of Encrypted Data
End of Encrypted Data
The size of the encrypted data: 0x4EAADh or 322,221d.
After Decryption:
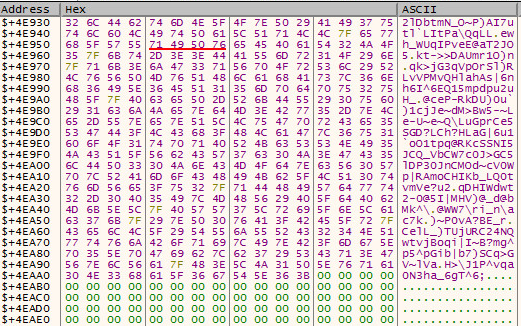
String Artifacts:
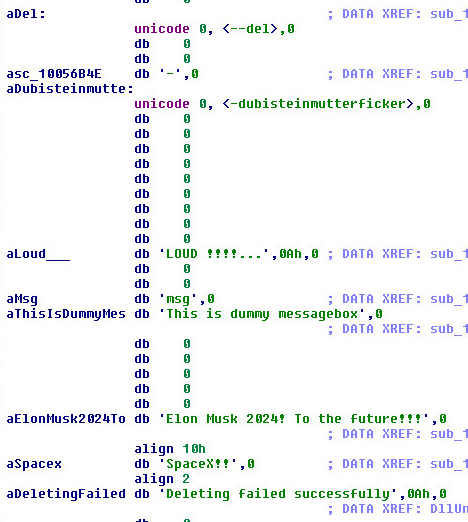
Two of the parameters shown in this picture above are (dash dash)del and (dash dash)dubisteinmutterficker.
dubisteinmutterficker is German for “you’re a mother fucker.”
We also see references to Elon Musk and SpaceX.
2nd Stage, Commands Payload Will Accept:
Egregor’s payload can accept several command line arguments, including:
- –fast: Is used to limit file size for encryption.
- –full: perform encryption of the full victim system (including local and network drives).
- –multiproc: multi-process support.
- –nomimikatz: Mimikatz is an open source toolkit.
- –nonet: does not encrypt network drives.
- –path: specific folder to encrypt.
- –target: target extension for encryption.
- –append: file extension to append to encrypted files.
- –norename: does not rename the files it encrypts.
- –greetings: prepends the name to the ransom note, presumably to directly address the victim.
- –samba: provide shared access to files, printers, and serial ports between nodes.
- –killrdp: remote desktop protocol
The most common command that is used is (-full).
Supported Systems:
- Windows 10
- Windows 8.1
- Windows 8.0
- Windows 7
- Windows Vista
SonicWall, (GAV) Gateway Anti-Virus, provides protection against this threat:
- GAV: Egregor.RSM (Trojan)
Appendix:
Sample SHA256 Hash: 38b155b6546db882189cc79bcac0b0284d3f858e0feb1e5dbc24b22f78cdfb68