Internet Explorer Vulnerability CVE-2014-1776 Exploit Analysis(May 23, 2014)
Dell Sonicwall Threat research team has analyzed the Internet Explorer Vulnerability CVE-2014-1776.
Earlier, we had addressed this vulnerability when Microsoft had released an out of band Security Advisory(2963983).
Following, shows an Analysis of how this attack is carried out.
The attack gets to the victim’s system via a webpage containing crafted malicious HTML document that exploits a use-after-free condition to achieve memory corruption.

The HTML contains reference to SWF which also does bulk of work.
Following shows the decompiled ActionScript that shows how Vector object is used along with the reference to eim which is an external javascript function.

The eim function contains code to trigger vulnerability point.

SWF is also tasked to check the browser version and act accordingly.
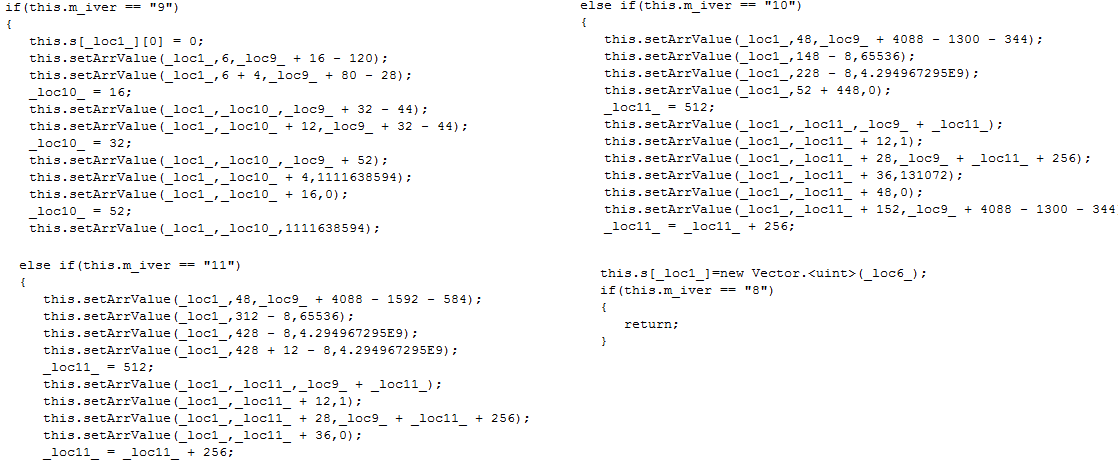
It also checks and sets the cookie to monitor the number of runs.

This is how ActionScript looks up the ZwprotectVirtualmemory utilized to create a reliable executable shellcode using ROP Chain.

We have implemented following signatures to detect the attack.
- IPS:3787 Internet Explorer Memory Corruption Vulnerability (CVE-2014-1776)
- SPY:3367 Malformed-File swf.OT.9
- SPY:2290 Malformed-File swf.OT.8
