SonicWALL UTM Research continues to observe the same social engineering tactic being used to spam new variants of Bredolab.
This new variant uses a similar DHL undelivered parcel email spam campaign that we have covered in SonicAlert – Multiple Spam Waves – Bredolab.X This new DHL undelivered parcel spam campaign which started since December 7, 2009 involves a fake e-mail message pretending to have come from DHL Delivery Services. The email informs the user that DHL was not able to deliver their parcel due to error in shipping address. It further instructs the user to pickup the parcel at their post office and print the attached shipping label. This attachment however, is an executable file which is this new variant of Bredolab Trojan.
Another campaign that the authors of this Trojan use is the Facebook password reset spam campaign as it still continues its wave since we covered it in SonicAlert – New social engineering tactics by Bredolab and ZBot. It still involves a fake e-mail message pretending to arrive from Facebook. It informs the users that Facebook have taken measures to provide safety to their clients that include resetting their password. It instructed the users to retrieve their new password from the attached document which is the new variant of Bredolab Trojan.
Campaign #1 – DHL parcel service
Subject:
- DHL Express Services. You need to get a parcel NR.[4-digit numeric number]
- DHL Office. Please get your parcel NR.[4-digit numeric number]
- DHL services. Please get your parcel NR.[5-digit numeric number]
- DHL International. Get your parcel NR.[4-digit numeric number]
- DHL Customer Services. Please get your parcel NR.[4-digit numeric number]
Attachment: DHL_Print_label_12454.zip (contains DHL_Print_label_12454.exe)
Email Body:
————————
Dear customer!
The courier company was not able to deliver your parcel by your address.
Cause: Error in shipping address.
You may pickup the parcel at our post office personaly.
Please attention!
The shipping label is attached to this e-mail.
Print this label to get this package at our post office.
Please do not reply to this e-mail, it is an unmonitored mailbox!
Thank you,
DHL Delivery Services.
————————
The e-mail message looks like below:

Campaign #2 – Facebook Password Reset spam
Subject:
- Facebook Password Reset Confirmation! Customer Message
- Facebook Password Reset Confirmation! Your Support
- Facebook Password Reset Confirmation! Important Message
- Facebook Password Reset Confirmation! Customer Support
Attachment: Facebook_Password_10493.zip (contains Facebook_Password_10493.exe)
Email Body:
————————
Hey [Facebook User]!
Because of the measures taken to provide safety to our clients, your password has been changed
You can find your new password in attached document.
Thank,
Your facebook.
————————
The e-mail message looks like below:

The executable file inside the zip attachment has an icon disguised as a Microsoft Excel sheet file:


The Trojan when executed performs the following host level activity:
- Drops a copy of itself as (Windows System Folder)Startuprarype32.exe (~36KB)
- Deletes the original file
- Injects its code to winlogon.exe process in the memory where it tries to connect to dollardream.ru domain and downloads an encrypted configuration file.
The Trojan is also known as trojan Mal/Bredo-A [Sophos] and TrojanDownloader:Win32/Bredolab.AB [Microsoft].
SonicWALL Gateway AntiVirus provides protection against this malware via GAV: Bredolab.AA_6 (Trojan) signature. [13,428,256 hits recorded starting December 10, 2009].



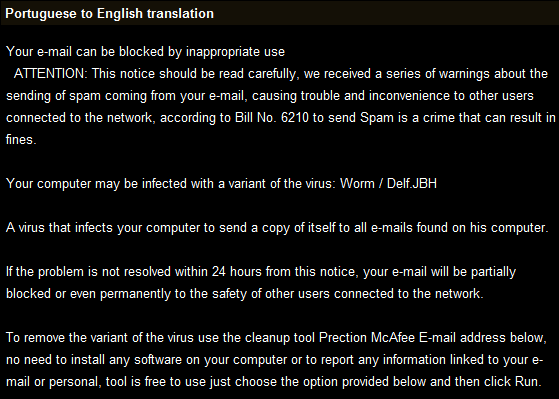








 Using social engineering techniques, the author replaced the warning message to this:
Using social engineering techniques, the author replaced the warning message to this:  Once the targeted user clicks the “Open” button, the cmd.exe will be launched. At this point it is up to the PDF author’s creativity to perform additional malicious actions, as cmd.exe can be used to run embedded executables in the PDF file. SonicWALL has released an IPS signature to detect and block PDF files utilizing launch action. The signature is listed below:
Once the targeted user clicks the “Open” button, the cmd.exe will be launched. At this point it is up to the PDF author’s creativity to perform additional malicious actions, as cmd.exe can be used to run embedded executables in the PDF file. SonicWALL has released an IPS signature to detect and block PDF files utilizing launch action. The signature is listed below:

