Microsoft Security Bulletins Coverage (Feb 08, 2011)
SonicWALL has analyzed and addressed Microsoft’s security advisories for the month of February, 2011. A list of issues reported, along with SonicWALL coverage information follows:
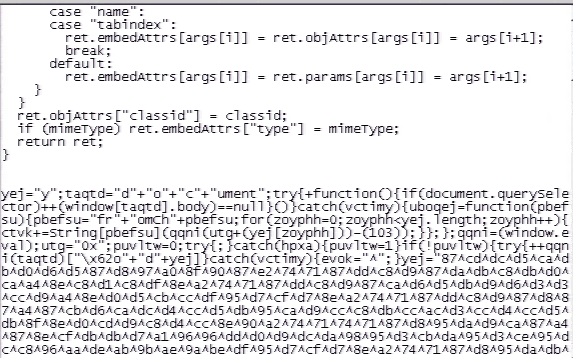
MS11-003 Cumulative Security Update for Internet Explorer (2482017)- CVE-2010-3971 – CSS Memory Corruption Vulnerability
IPS 6094 MS IE CSS Import Use-After-Free Code Execution Exploit 1
IPS 6095 MS IE CSS Import Use-After-Free Code Execution Exploit 2
IPS 6096 MS IE CSS Import Use-After-Free Code Execution Exploit 3
IPS 6098 MS IE CSS Import Use-After-Free Attempt - CVE-2011-0035 – Uninitialized Memory Corruption Vulnerability
This is a logical vulnerability. No IPS detection solution is available. - CVE-2011-0036 – Uninitialized Memory Corruption Vulnerability
IPS 6223 MS IE DHTML Object Memory Corruption (MS11-003) - CVE-2011-0038 – Internet Explorer Insecure Library Loading Vulnerability
IPS 5726 Possible Binary Planting Attempt
- CVE-2010-3972 – IIS FTP Service Heap Buffer Overrun Vulnerability
IPS 6101 MS IIS FTP Server DoS Vulnerability
MS11-005 Vulnerability in Active Directory Could Allow Denial of Service (2478953)
- CVE-2011-0040 – Active Directory SPN Validation Vulnerability
This is a local vulnerability. No IPS detection solution is available.
- CVE-2010-3970 – Windows Shell Graphics Processing Overrun Vulnerability
IPS 6119 MS Graphics Rendering Thumbnail Stack BO Exploit
- CVE-2011-0033 – OpenType Font Encoded Character Vulnerability
GAV 39973 OpenType.MS11-007
MS11-008 Vulnerabilities in Microsoft Visio Could Allow Remote Code Execution (2451879)
- CVE-2011-0092 – Visio Object Memory Corruption Vulnerability
This is a logical vulnerability. No IPS detection solution is available. - CVE-2011-0093 – Visio Data Type Memory Corruption Vulnerability
This is a logical vulnerability. No IPS detection solution is available.
- CVE-2011-0031 – Scripting Engines Information Disclosure Vulnerability
IPS 6224 Possible Scripting Engine Memory Corruption Attack
- CVE-2011-0030 – CSRSS Elevation of Privilege Vulnerability
This is a local vulnerability. No IPS detection solution is available.
MS11-011 Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2393802)
- CVE-2010-4398 – Driver Improper Interaction with Windows Kernel Vulnerability
This is a local vulnerability. No IPS detection solution is available. - CVE-2011-0045 – Windows Kernel Integer Truncation Vulnerability
This is a local vulnerability. No IPS detection solution is available.
MS11-012 Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (2479628)
- CVE-2011-0086 – Win32k Improper User Input Validation Vulnerability
This is a local vulnerability. No IPS detection solution is available. - CVE-2011-0087 – Win32k Insufficient User Input Validation Vulnerability
This is a local vulnerability. No IPS detection solution is available. - CVE-2011-0088 – Win32k Window Class Pointer Confusion Vulnerability
This is a local vulnerability. No IPS detection solution is available. - CVE-2011-0089 – Win32k Window Class Improper Pointer Validation Vulnerability
This is a local vulnerability. No IPS detection solution is available. - CVE-2011-0090 – Win32k Memory Corruption Vulnerability
This is a local vulnerability. No IPS detection solution is available.
MS11-013 Vulnerabilities in Kerberos Could Allow Elevation of Privilege (2496930)
- CVE-2011-0043 – Kerberos Unkeyed Checksum Vulnerability
This is a local vulnerability. No IPS detection solution is available. - CVE-2011-0091 – Kerberos Spoofing Vulnerability
This is a local vulnerability. No IPS detecti
on solution is available.
- CVE-2011-0039 – LSASS Length Validation Vulnerability
This is a local vulnerability. No IPS detection solution is available.