Microsoft Windows Privilege escalation vulnerability (CVE-2013-5065) attacks (Dec 4, 2013)
The Dell SonicWALL Threats Research team observed reports of a new Windows privilege escalation vulnerability being exploited in the wild. Microsoft has released a security advisory for this vulnerability identified by CVE-2013-5065, and this vulnerability only affects users on Windows XP and Windows Server 2003 operating systems.
The exploit code is being distributed in a specially crafted PDF file. The PDF file contains malicious JavaScript with shellcode, obfuscated using JJEncode, that checks for specific versions of Adobe Reader and performs heapspray. If the Adobe Reader exploit attempt is successful, it will crash the application and pass the control to the shellcode. The shellcode further attempts to exploit a local Windows privilege escalation vulnerability on the target machine. It then decrypts a malicious executable embedded inside the original PDF file and installs it on the victim machine with kernel mode privilege.
The following chart illustrates the complete infection cycle:

Below is the deobfuscated JavaScript code checking for Adobe Reader version prior to exploitation attempt:

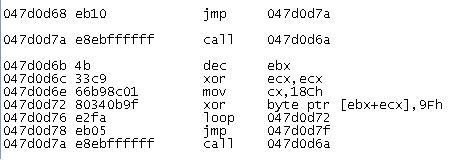
Upon successful Adobe Reader exploitation, the shellcode opens \.NDProxy and issues a specially crafted DeviceIOControlCode API call that triggers a local privilege escalation vulnerability mentioned here.

The shellcode then decrypts and executes embedded malware executable with elevated privileges on the target machine. The malware executable was found to inject code into system explorer.exe process. It also creates the following registry key to persist infection upon system reboot.
- HKCUSoftwareMicrosoftWindows NTCurrentVersionWinlogon “Shell” = explorer.exe,(path to malware)
Dell SonicWALL Gateway AntiVirus provides protection against this threat with the following signature:
- GAV: Inject.DKI (Trojan)
- GAV: Pidief.SKD (Exploit)