Spam campaign roundup: The Thanksgiving Day Edition (Nov 23, 2016)
Thanksgiving day is right around the corner. This marks the start of the holiday shopping season with Black Friday being the busiest shopping day of the year. Consumers are expecting great deals and looking out for incredible promotions. More shoppers are expected to shop online for gifts this holiday season and cyber criminals are also leveraging on this opportunity to take advantage of unsuspecting shoppers.
And true enough, the SonicWALL threat research team has observed a steady increase in Black Friday and Thanksgiving related spam emails over the past week.

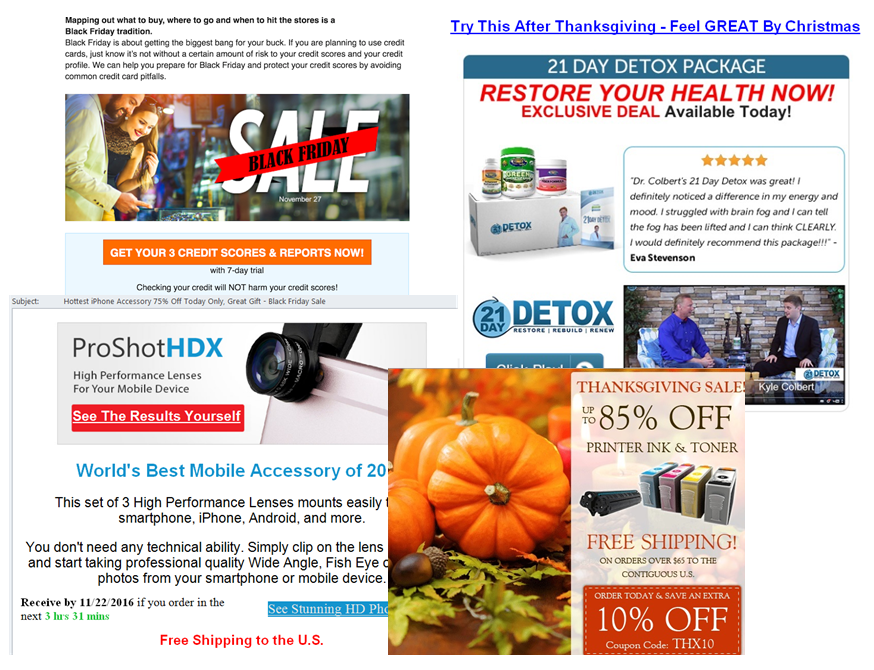
As Thanksgiving weekend approaches, we have been receiving an increasing amount of spam emails as shown in the figure above and this number is expected to increase all throughout the weekend and through Cyber Monday. Because consumers are spending more time shopping online, cybrecriminals are preying on shoppers who might not be aware of the risks. As usual, these emails have a common theme of trying to lure consumers to click on the links and provide personal information purporting to be from popular retailers and promising amazing deals and deep discounts. The following are some of the common email subjects to watch out for:
- Score Smart on Blackfriday
- The Hottest gift this Holiday Season…(75% off Black Friday Sale)
- *ALERT* Black Friday Sale Starts! All 80% Off & Free Shipping Now.
- Government Overrun: “Super Flashlight” – Black Friday 75% off
- Thanksgiving Sale – SAVE up to 85% on everything.
- Feeling Tired? Try This After Thanksgiving – Feel GREAT By Christmas.
Below is an example of an email purporting to be from a popular shoe brand. The link will take you to a URL different from the real merchant’s website. This fake website even copied the layout of the actual brand’s website to be even more convincing.

We urge our users to always be vigilant and cautious with any unsolicited email and to avoid providing any personal information, particularly if you are not certain of the source.
SonicWALL Gateway Antivirus and Email Security service constantly monitor and provide protection against such malicious spam and phishing threats.