Super Mario Run received a stellar launch on Apple devices as it was downloaded 2.85 million times on its launch day – December 15 2016. Its popularity has been going strong since its launch as it continues to increase its user base. As of mid-January 2017 there is still no concrete confirmation about the availability of Mario for Android devices, but this has not stopped users from searching for Mario Run for Android.
Attackers have taken note of this popularity and created fake apps that pose as Mario Run but have malicious content hidden in them. These apps can be downloaded from third party app-stores as shown below:

The official placeholder for this app on Google Play says it’s open only for pre-registration (As of January 15, 2017):

Sonicwall Threats Research team observed few cases where Super Mario Run was being used as a medium to spread malicious apps, this blog highlights these cases.
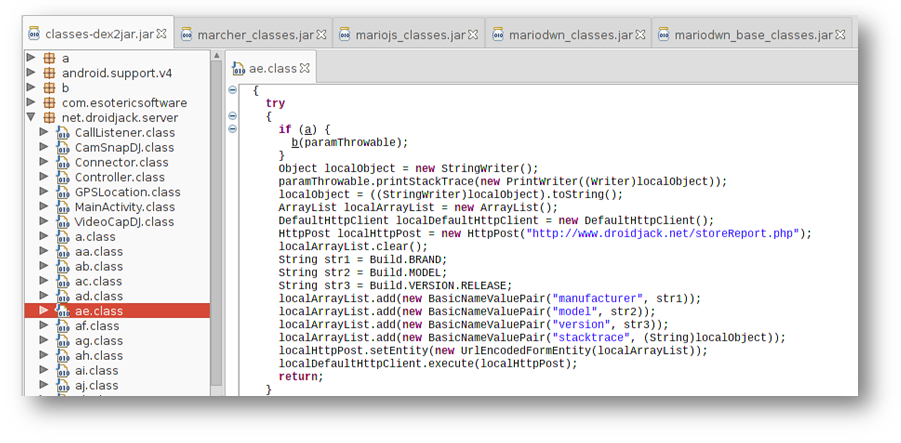
Mario Run with embedded DroidJack
We saw two instances where Droidjack was embedded as part of the app. Droidjack is an Android Remote Administration Tool (RAT) that has a plethora of features, few of them are as listed below:
- Read and delete call logs
- Make calls
- Read, write and delete SMS messages
- Read, create and delete contacts
- Take pictures from the front/back camera
- Record videos from front/back camera
The figure below shows DroidJack code in the apk:
Marcher banking malware hiding behind Mario Run
Marcher is a known banking malware for Android, it tries to steal sensitive banking and credit card information from the users after infecting a device. The Marcher variant for Mario is no different, it targets the presence of few Banking apps on the phone and shows a custom screen when these apps are executed on the device. This custom screen accepts data from the user and sends it directly to the attackers, meanwhile the user thinks he passed this data to the legitimate banking app. We have listed few banking apps below, the entire list can be seen in the appendix:
- Barclays Zambia – com.barclays.android.barclaysmobilebanking
- HSBC Mobile Banking – com.htsu.hsbcpersonalbanking
- Santander UK Personal Banking – uk.co.tsb.mobilebank
- Lloyds Bank Mobile Banking – com.grppl.android.shell.CMBlloydsTSB73
- Bank of Scotland Mobile Bank – com.grppl.android.shell.BOS
It also shows a custom screen which accepts Credit Card information when Google Play app is opened. Additionally this malware checks the presence of few apps which perform security checks on the device, it disables these apps upon finding them. Few apps that are targeted are listed below, the entire list can be found in the appendix:
- DU Antivirus – com.duapps.antivirus
- Eset Mobile Security & Antivirus – com.eset.ems.gp
- AVG AntiVirus FREE for Android – avg.antivirus
- 360 Security Lite Speed Boost – com.qihoo.security.lite
- IKARUS mobile.security – com.ikarus.mobile.security

Adware installer laden Mario Run
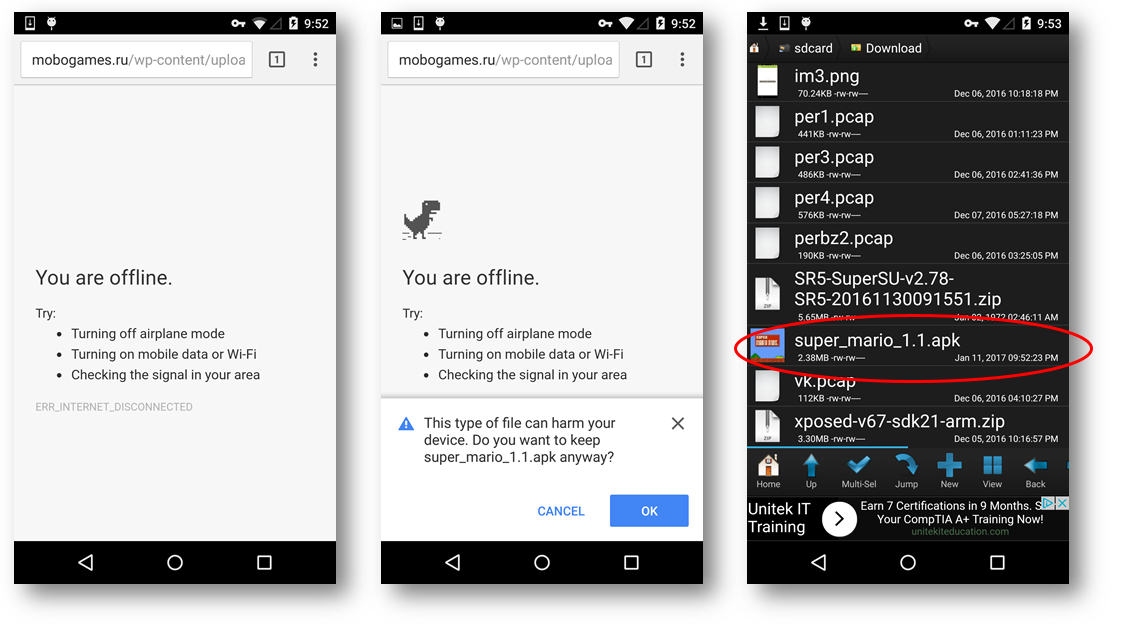
Adware on Android has been a nuisance for a while now, it’s no surprise to find adware try and use Mario’s popularity for its own gain. We got our hands on an adware installer that uses Mario Run as a guise. Upon installation this adware starts downloading secondary adware apps and stores them on the device as shown below:
Additionally it shows an overlay on the device which is essentially an advertisement that promotes more adware apps:

The adware has capabilities to capture sensitive details about the device like IMEI number:

During our analysis we observed the adware communicate with the following domains:
- xtra1.gpsonextra.net
- mobogames.ru
- show-app-ads.ru
SonicWALL provides protection against multiple versions of this threat via the following signatures:
- GAV: AndroidOS.DroidJack.MA (Trojan)
- GAV: AndroidOS.Marcher.AV (Trojan)
- GAV: AndroidOS.Downloader.BR (Trojan)
Appendix
The following samples were analyzed in this blog:
- Malware type: Embedded DroidJack component
- MD5: 69b4b32e4636f1981841cbbe3b927560
- Package Name: net.droidjack.server
- Malware type: Embedded Marcher component
- MD5: 03e459c685cd7320384af4cc938b1a69
- Package Name: jse.hjevdybdgjgmyosekskxdczwyqunha
- Malware type: Embedded Marcher component
- MD5: d332560f1fc3e6dc58d94d6fa0dab748
- Package Name: uiq.pizfbwzbvxmtkmtbhnijdsrhdixqwd
- Malware type: Embedded Adware downloader
- MD5: cab7c1ed86d87e1a174bae0557a09c0e
- Package Name: app.android_files_downloader_25311216
Complete list of Banking apps that are monitored by the analyzed Marcher embedded Mario Run app:
- Mes Comptes – LCL pour mobile – fr.lcl.android.customerarea
- L’Appli Societe Generale – mobi.societegenerale.mobile.lappli
- CIC Euro Information – com.cic_prod.bad
- Mes Comptes BNP Paribas – net.bnpparibas.mescomptes
- Royal Bank of Scotland – com.rbs.mobile.android.ubr
- Halifax Mobile Banking app – com.grppl.android.shell.halifax
- La Banque Postale – com.fullsix.android.labanquepostale.accountaccess
- Barclays Zambia – com.barclays.android.barclaysmobilebanking
- Banque Caisse d’Epargne – com.caisseepargne.android.mobilebanking
- Rbs Mobile Payment – com.rbs.mobile.android.rbs
- Cyberplus Banque Populaire – fr.banquepopulaire.cyberplus
- Ma Banque – fr.creditagricole.androidapp
- HSBC Mobile Banking – com.htsu.hsbcpersonalbanking
- Santander UK Personal Banking – uk.co.tsb.mobilebank
- Lloyds Bank Mobile Banking – com.grppl.android.shell.CMBlloydsTSB73
- Bank of Scotland Mobile Bank – com.grppl.android.shell.BOS
- Rbs Mobile Payment – com.rbs.mobile.android.natwest
- Santander UK plc Personal Banking – uk.co.santander.santanderUK
Complete list of Security apps that are monitored by the analyzed Marcher embedded Mario run app:
- DU Antivirus – com.duapps.antivirus
- Eset Mobile Security & Antivirus – com.eset.ems2.gp
- Eset Mobile Security & Antivirus – com.eset.ems.gp
- AntiVirus & Mobile Security – com.anhlt.antiviruspro
- AVG AntiVirus FREE for Android – avg.antivirus
- AVG AntiVirus FREE for Android – com.antivirus
- CM Speed Booster – com.cleanmaster.boost
- 360 Security Lite Speed Boost – com.qihoo.security.lite
- com.thegoldengoodapps.phone_cleaning_virus_free.cleaner.booster
- Anti-virus Dr.Web Light – com.drweb
- Clean Master (Boost&Antivirus) – com.cleanmaster.mguard
- IKARUS mobile.security – com.ikarus.mobile.security
- Antivirus Free – Virus Cleaner – com.zrgiu.antivirus
- CM Security AppLock AntiVirus – com.cleanmaster.security
- NQ Mobile Security & Antivirus – com.netqin.antivirus
- NQ Mobile Security & Antivirus – com.nqmobile.antivirus20
- CCleaner – com.piriform.ccleaner
- 360 Se
curity – Antivirus Boost – com.qihoo.security - Super Virus Detector – droiddudes.best.anitvirus
- NQ Mobile Security & Antivirus – com.nqmobile.antivirus20.clarobr
- Norton Security and Antivirus – com.symantec.mobilesecurity
- Mobile Security & Antivirus – com.avast.android.mobilesecurity
- Bitdefender Antivirus Free – com.bitdefender.antivirus
- Trustlook Free Antivirus & Security – com.trustlook.antivirus
- Kaspersky Antivirus & Security – com.kms.free
- DU Speed Booster & Cleaner – com.dianxinos.optimizer.duplay
- Cheetah Mobile CleanMaster SDK – com.cleanmaster.sdk
- AVD Tablet AntiVirus FREE 2017 – com.antivirus.tablet
- DFNDR: Antivirus & Booster – com.psafe.msuite
- Womboid Systems Antivirus – com.womboidsystems.antivirus.security.android