Sage 2.2 updated with audio alert and reduced ransom (March 29th, 2017)
The Sage Ransomware (covered in a previous SonicAlert) continues developement by cyber crimimals and has recently received a minor update. As usual this ransomware encrypts personal documents, images, databases, videos and other files rendering them unusable. As well as some refinements to its alert page it now uses the Windows built-in text-to-speech engine to play an audio alert. The audio alert informs the user of the infection and encryption of files. Additionally, the cost of decryption that had previously been $2000 USD has now been reduced to $800 USD.
Infection Cycle:
The Trojan uses the following icon:

The Trojan adds the following files to the filesystem:
- %SYSTEMROOT%!HELP_SOS.hta
- %ALLUSERSPROFILE%Desktop!HELP_SOS.hta
- %ALLUSERSPROFILE%Documents!HELP_SOS.hta
- %APPDATA%f1.hta
- %APPDATA%En3QVWV9.exe [Detected as GAV: Sage.A (Trojan)]
- %APPDATA%MicrosoftSpeechFilesUserLexiconsSP_029A022514CA4689BAFB15AF07CD496A.dat
- %USERPROFILE%Desktop!HELP_SOS.hta
- %USERPROFILE%Local SettingsTempaV2.bmp
- %USERPROFILE%My Documents!HELP_SOS.hta
- %SYSTEM32%CatRoot2tmp.edb
The Trojan adds the following keys to the registry:
- HKEY_CLASSES_ROOT.sage @ “sage.notice”
- HKEY_CLASSES_ROOTsage.noticeDefaultIcon @ “%WinDir%system32shell32.dll,47”
- HKEY_CLASSES_ROOTsage.noticeFriendlyTypeName @ “encrypted by SAGE”
- HKEY_CLASSES_ROOTsage.noticeshellopencommand @ “mshta.exe “%APPDATA%f1.hta” “%1″”
- HKEY_CURRENT_USERSoftwareMicrosoftSpeechVoices DefaultTokenId “HKEY_LOCAL_MACHINESOFTWAREMicrosoftSpeechVoicesTokensMSSam”
- HKEY_CURRENT_USERSoftwareClasses.sage @ “sage.notice”
- HKEY_CURRENT_USERSoftwareClasseshtafileDefaultIcon @ “%WinDir%system32shell32.dll,44”
- HKEY_CURRENT_USERSoftwareClassessage.noticeDefaultIcon @ “%WinDir%system32shell32.dll,47”
- HKEY_CURRENT_USERSoftwareClassessage.noticeFriendlyTypeName @ “encrypted by SAGE”
- HKEY_CURRENT_USERSoftwareClassessage.noticeshellopencommand @ “mshta.exe “%APPDATA%f1.hta” “%1″”
aV2.bmp contains the following image that is displayed on the desktop background after infection:

!HELP_SOS.hta contains the following image that is displayed in the foreground:


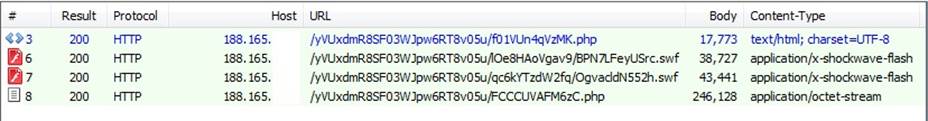
Sage encrypts files and renames them with a .sage file extension. During encryption a key is sent to a remote server:

If there is no response from the key server, Sage attempts to make contact via UDP. It broadcasts the key to a variety of predefined IP addresses in the hope that it will make it to the key server:

Sage 2.2 now contains an audio alert that is played when the alert images are displayed. It is repeated every 5 minutes. Below is a capture of the audio:
Transcript:
Attention... Attention... this is not a test. All you documents, databases and otherimportant files were encrypted and Windows cannot restore them without special software.User action is required as soon as possible to recover the files.All you documents, databases and other important files were encrypted and Windows cannotrestore them without special software. User action is required as soon as possible to recover the files.The links given in !HELP_SOS.hta lead to the following web pages:



SonicWALL Gateway AntiVirus provides protection against this threat via the following signatures:
- GAV: Sage.A (Trojan)
- GAV: Sage.B (Trojan)































 I am honored to highlight my esteemed colleague, Steve Pataky, Vice President of Worldwide Sales at SonicWall, who was just named
I am honored to highlight my esteemed colleague, Steve Pataky, Vice President of Worldwide Sales at SonicWall, who was just named 