History is full of people who’ve labored over missed opportunities. Like all other non-bitcoin-owning people, I am one of them.
I first heard of cryptocurrency in early 2013 and scoffed at the idea that something with no intrinsic or collectable value would trade for $20. The concept of owning a portion of a cryptographic code — and it having actual value — is still hard for many to swallow.
Now that an available bitcoin (BTC) is valued at over $19,000 (USD), I languish the fact that an investment of $1,000 in 2013 would have net me half of a million dollars today. Furthermore, had I been tuned into the movement in 2010, I would be a billionaire today. You too. Stings a little, doesn’t it?
At no point in history has it been so easy to become extremely wealthy out of thin air. And it is not just people like you and me who think about this, but criminals as well. This is not only causing major shifts in financial markets, but also in malware development.
What is Cryptocurrency?
With all of the noise about cryptocurrency, here is what we know as we near 2018:
- There are, or have been, over 1,300 other cryptocurrencies on the market. These are called altcoins.
- Most people have never owned a single “coin” from any blockchain.
- Most have no basis for value, which means it’s subjective and speculative (e.g., like a baseball card or an artistic sketch). The community dictates the value.
- Some are tied to a real currency (e.g., 1 Tether coin = $1 USD).
- Governments struggle with regulation and don’t want to encourage the use of decentralized currencies.
- They often function like startups. Founders get an early crack at the supply chain and hold an equitable stake in the algorithm. Instead of a stock IPO they release them as part of an Initial Coin Offering (ICO).
- Most of the popular coins cannot be mined by your computer anymore. Today, it’s only achieved through professional-grade mining operations.
- No one knows how high or low bitcoins and cryptocurrency will go; either they will die or become the basis for our future economy.
- The popular coins today are desired by cybercriminals and are the main form of payment within ransomware.
- Like a TLS digital certificate, cracking the actual encryption is nearly impossible. Bitcoins are, however, fairly easy to steal and even easier to lose or destroy.
- Malware is used to steal coins and to also turn infected endpoints into mining bots.
Bitcoin Is the Great Ransomware Enabler
Because cryptocurrency is virtually un-trackable, holds great value and is easily traded online, they are the preferred way to get paid on the black market. Without the value of bitcoin, you wouldn’t have heard about ransomware.
Ransomware is responsible for causing billions of dollars (USD) in damage across the world. Furthermore, the actual cost of the problem isn’t the cost of bitcoin to return your files (if you ever get them back), but the fallout from an attack.
Ransomware is fun for the media because you can easily quantify the ransoms and take photos of the demand screens, but not so fun for hackers. Through the development, updates and propagation of the malware, only between five and 10 percent of people pay the demands. But there is another way.
Bitcoin Mining
Instead of having your victims pay you once, what about having your victims unknowingly work for you? Well, that is what a lot of malware is doing today. By leveraging a portion of your compute power to form a bitcoin mining pool, hackers don’t have to kill the goose that lays the golden egg.
The result? The home computer has less power to run normal processing and incurs higher energy costs. When this approach works its way into a corporate network, it could cause major productivity and service issues.
For some hackers, these two attack vectors are small-time thinking. Instead of counting on a distributed attack vector across a global landscape of endpoints with mixed vulnerabilities, what about a single targeted attack?
Hackers don’t attack the algorithm behind the coins, they attack where they are stored. Cryptocurrency banks and exchanges are ripe targets for attacks. If you factor in the price of a bitcoin (at the time of I started writing it was $8,160 and after editing its $16,000) — the second Mt. Gox attack emptied bitcoin wallets to the tune of over $11 billion USD. Wow! At the time, the bitcoin haul was nearly 744,000 coins worth $436 million USD and caused the value of bitcoin to fall to a three-month low.
Cryptocurrency: Is it the Future?
Like most dual-sided arguments, those inside a social ecosystem are bullishly optimistic. Those outside remain pessimistic. I’m in between. I see the opportunity to capitalize on the attention, but recognize the many limitations behind cryptocurrencies that cap their viability into the future.
I’ve never owned a bitcoin coin but have entered into a few key platforms for the short-term. As mentioned, the value is purely subjective, much like an arbitrary piece of art, which can be a good investment as long as there is a large pool of people with the financial ability to support and bloat its value.
What is the difference in value between this rare Honus Wagner T206 card ($3.12 million USD) and the common Dusty Baker’s 1987 Topps card ($0.70 USD)? The answer lies in the availability of the item and the demand from the consumer.
Bitcoin, Ethereum and Monero all have value because a community of people feels it does. The more people who enter this pool, the greater the potential value. Some are investors and others are victims buying a ransom. But what truly drives the cost of bitcoin is attention — just like a piece of sports memorabilia. When you mirror Google’s search trend data to the historical price of BTC, you see a direct correlation.

What does this tell me? Once the attention fades, people will lose interest. At that point, the price will come down, similar to a Derek Jeter autographed baseball. Additionally, as ransomware becomes less effective, fewer people will buy bitcoin for the sake of digital freedom. And that freedom is the primary thing cryptocurrency can buy.
In the past year, every time the price of bitcoin dropped the Chicken Littles of the world wanted to be the first to cry out, “The sky is falling!” I do believe there will come a time when bitcoins will have the value the 1986 Topps Traded Pete Ladd sitting in the back of your closet (less than $1), but its value won’t crumble in a day.
With the remaining 1,000-odd altcoin cryptocurrencies (that currently hold value) out there with a collective market cap of over $400 billion (at the time of writing), it would take a lot for crypto-investors to create the needed fire sale that would cause the market’s topple. Instead, I see it like the Ice Age; built in stages and then a slow recession.
The altcoins wouldn’t exist today if bitcoin wasn’t popular and a goldmine for the early investors. The creators of these algorithms are like the leaders of pyramid scams. They created the rules and the ecosystem to make money and only exist if their supporters exist, much like an Amway Double-Dutch Triple-Black Platinum Diamond Founder’s Crown Elite Wizard. These will be the first to die. The beginning of their end is when bitcoin hits a plateau lasting more than two months.
In the Ice Age analogy, bitcoin is much like a large glacier that icicles attach to. As the sun shines, they will melt, leaving only the strongest cryptocurrencies to linger. I see bitcoin and Ethereum lasting for years, but only at a small price point. The coins in active circulation will be mostly in the possession of cyber criminals (if they aren’t already) and will be sold to the victims of cybercrimes to pay ransoms until the practice to buy cryptocurrency is outlawed country by country.
And, with that, the official death of ransomware.
Death in a Cathedral
Thirty years from now when we look back at cryptocurrency, we will reminisce about the second coming of the roaring ‘20s. Without the presence of Babe Ruth and the Charleston, we’ll have great unregulated wealth that comes to a crash.
In my conservative outsider-ish advice, I recommend minor, short-term cryptocurrency investments that you are not afraid to lose. Watch the price of bitcoin. When you see a plateau lasting a month, sell. (However, I’m not a financial advisor and I have no fiduciary duties to you. Please do your own research.)
Remember the old adage: movements are built in caves and die in cathedrals. Bitcoin is in the cathedral phase of its life. And if you understand the politics and history of cathedrals, you would be wary of entry. If not, read The Gothic Enterprise: A Guide to Understanding the Medieval Cathedral. Pay attention to fallout surrounding the bankrupt Bishop Milo de Nanteuil.
The Marriage Between Malware & Cryptocurrency
Another adage I was raised with, “make hay when the sun shines,” is what hackers are doing today. As the flames of bitcoin flare, more moths will be drawn to its light. The illicit creation, extortion and theft of digital coins will drive the price to an all-time high.
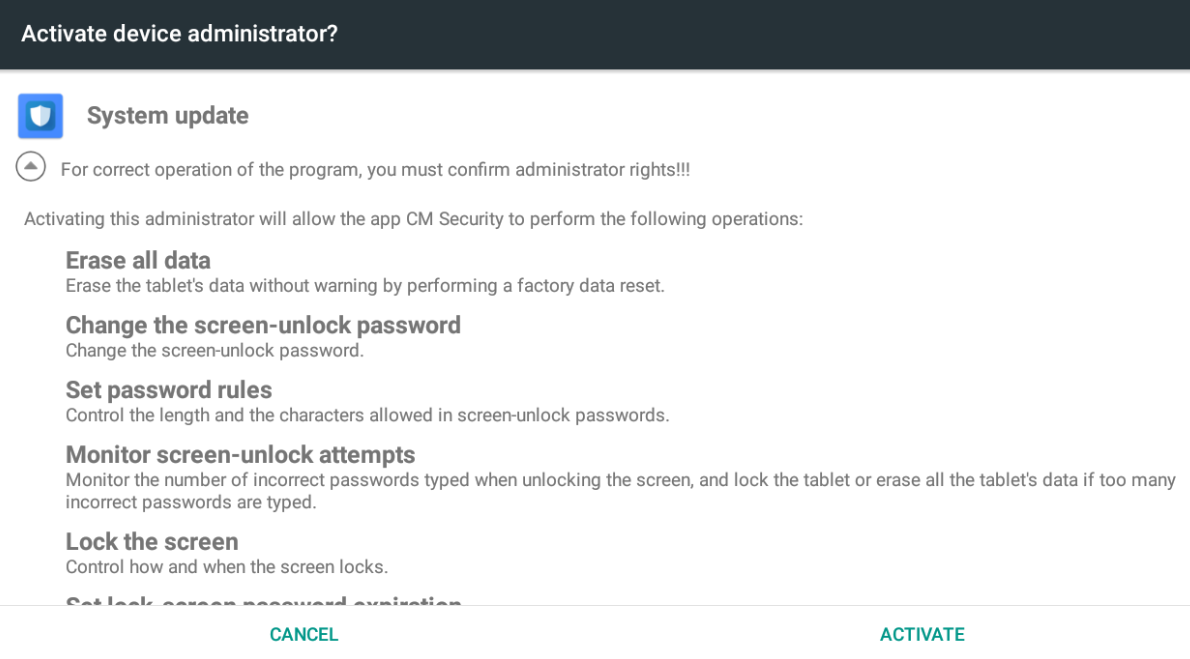
Because of the outrageous volume of ransomware infections of 2016, and the infamous attacks in 2017, malware defense is at an all-time high too, but it is not enough. Network and end-point security needs to be a serious topic of discussion.
At SonicWall, we’ve made great strides to get ahead of the cryptocurrency attacks; far before a hunk of digital code was valued at dollar volumes higher than what your grandfather paid for his first home.
Before the public release of Zcash, we released the SonicWall Capture Advanced Threat Protection service, which is a cloud-based network sandbox that works in line with SonicWall next-gen firewalls to run and test suspicious code in an isolated environment to prevent newly developed ransomware attacks (and other forms of malware too).
To bolster endpoint protection, we created an alliance with SentinelOne to provide an enhanced endpoint security client framework to provide next-generation anti-virus capabilities to our current endpoint offerings.
To learn more on how SonicWall can prevent malicious attacks, please read our solution brief, Five Best Practices for Advanced Threat Protection. If you’d like to discuss this blog, the marriage between malware and cryptocurrency, and to send your potentially future-worthless digital collectibles, reach out to me on Twitter.




![]()