Cybersecurity News & Trends – 06-08-18
Each week, SonicWall collects the cyber security industry’s most compelling, trending and important interviews, media and news stories — just for you.
SonicWall Spotlight
Galix Becomes SonicWall’s First Ever Platinum Partner in Africa — IT News Africa
- Galix, an IT services, infrastructure management and compliance company, has become the first ever African partner to receive SonicWall’s Platinum Partner status.
SonicWall Looks Beyond Firewalls to Bolster Cyber-Security — eWeek
- eWeek sits down with SonicWall CEO Bill Conner at RSA to discuss the company’s progress toward becoming a financially and operationally independent company in a written article and accompanying video interview.
Cyber Security News
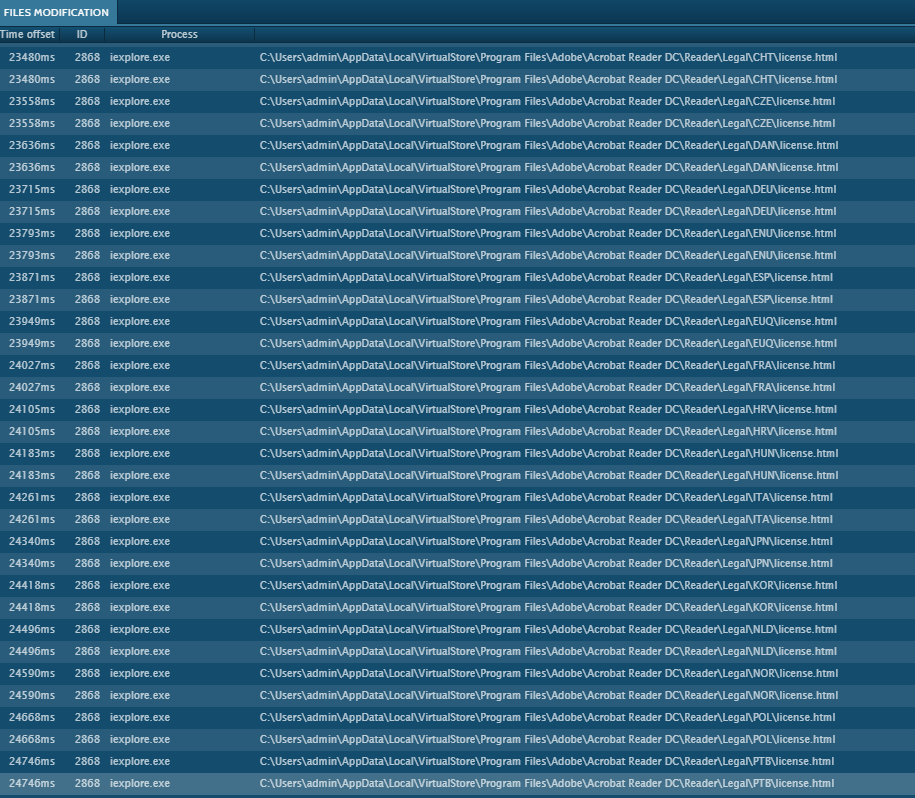
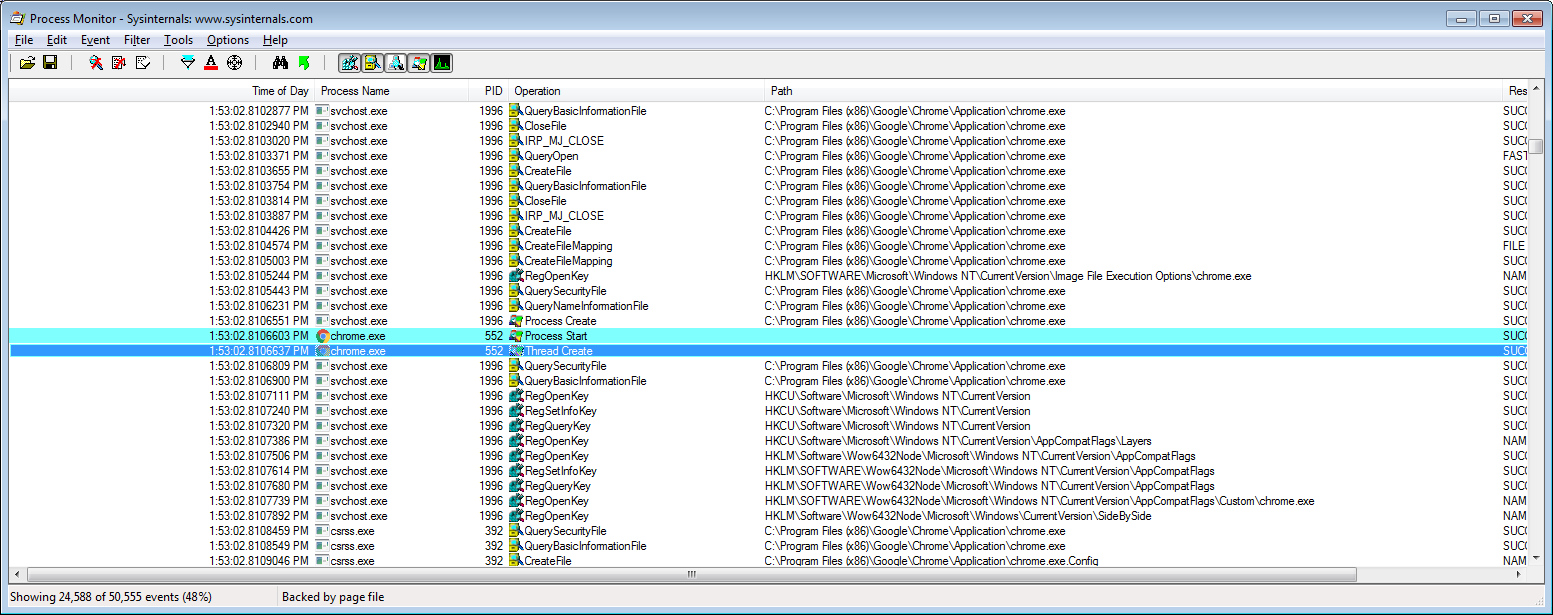
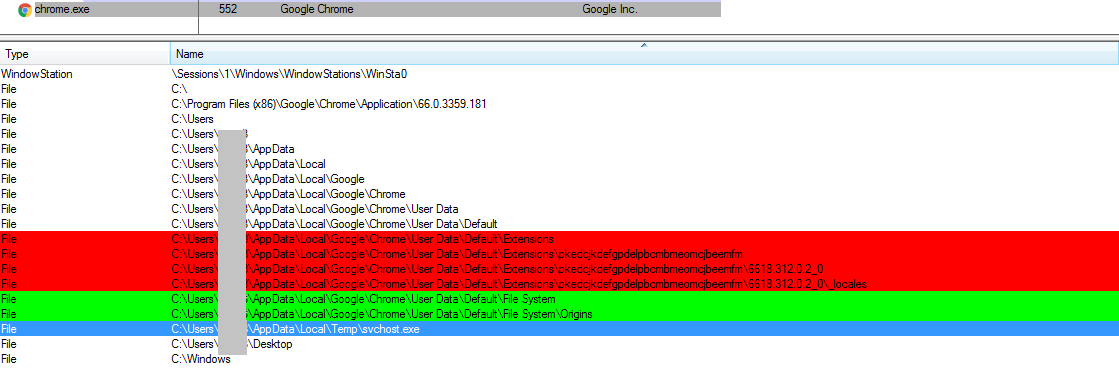
US-North Korea Summit News Used as Lure in New Malware Campaign — Dark Reading
- North Korea’s Group 123, an advanced persistent threat actor responsible for several major malicious campaigns in recent years, is believed to be behind new malware activity targeting users in South Korea.
Researcher Finds Login Info for 92 Million MyHeritage Users on Private Server — SC Magazine
- A file named myheritage discovered on an outside private server contained the email addresses and hashed passwords of more than 92 million MyHeritage customers, the genealogy and DNA testing company’s CISO said.
Here’s a Transaction Transamerica Regrets: Transgressors Swipe Retirees’ Personal Info — The Register
- Financial house Transamerica has admitted hackers swiped some of its customers’ sensitive personal information, including social security numbers.
Ukraine Says Prevented Cyber Attack on NATO Country Embassy — Reuters
- Ukraine’s state security service (SBU) prevented a cyber attack on the embassy of a NATO country in Kiev, it said in a statement on Tuesday, without specifying which one.
Mich. County Official Falls for Phishing Scam, Quits — The Detroit News
- An official in a small Michigan county has resigned after being tricked into wiring $50,000 to an overseas bank account.
In Case You Missed It
- eWeek Goes 1-on-1 with SonicWall CEO Bill Conner — Andrew Dean
- Report: Low Confidence in Stopping Business Email Compromise (BEC), CEO Fraud — Ganesh Umapathy
- Why I Joined SonicWall — Lawrence Pingree
- Frequently Asked Questions: The E-rate Program — Geoff Blaine
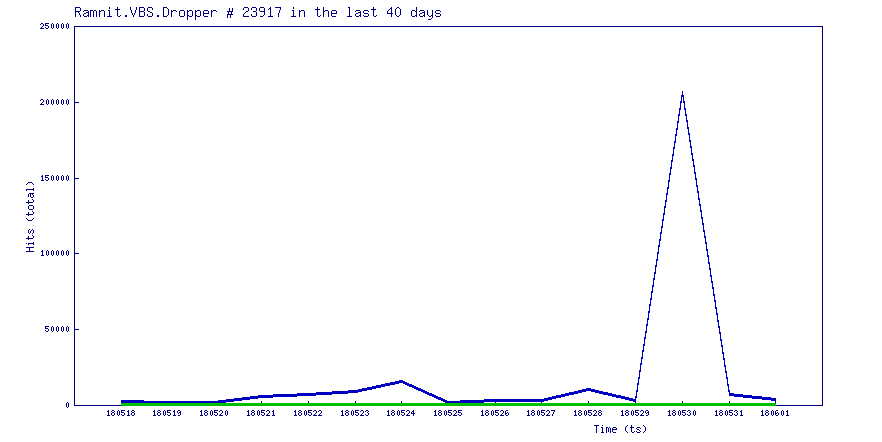
- New Cyber Threat Intelligence Shows Growing Malware Volume, Encrypted Attacks — Geoff Blaine