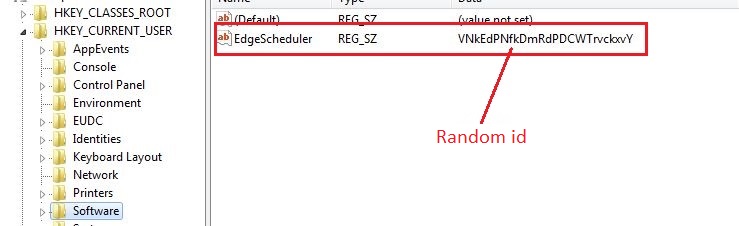
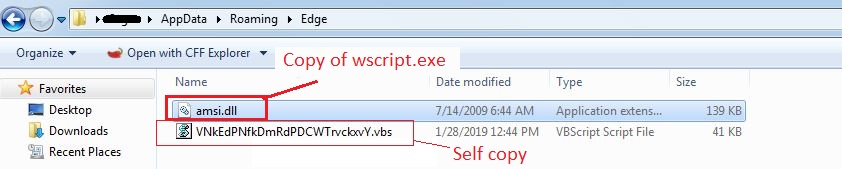
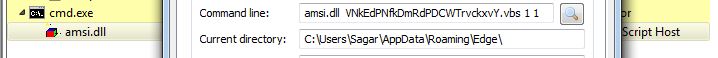
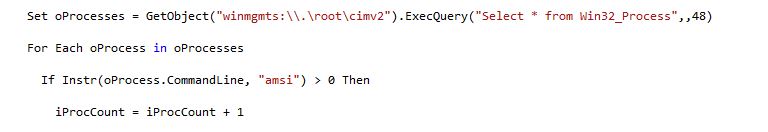
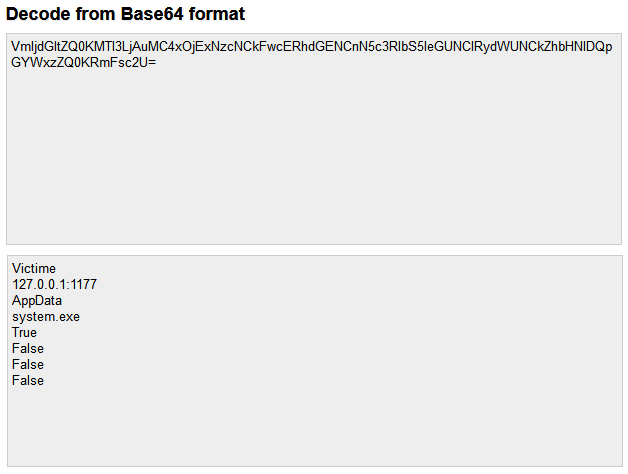
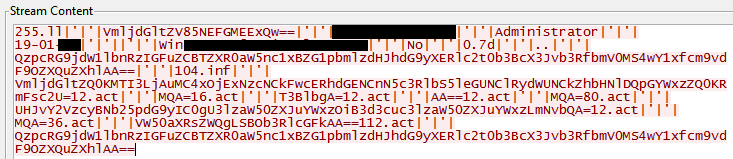
Effectively marketing and selling managed service provider (MSP) services can be a real uphill battle for many organizations. The competition is fierce and positioning your organization’s services or competitive advantages isn’t easy.
For many MSPs and MSSPs, the responsibility of envisioning, designing, developing and maintaining effective marketing materials falls on the shoulders of the sales team or the senior leadership team. But they don’t always have the time or skill to execute what’s needed to cut through the cacophony of marketing noise.
Fortunately, SonicWall has alleviated much of this burden.
SonicWall Overdrive 2.0 is a remarkable resource stocked with modern, appealing and relevant content to help MSPs and MSSPs generate demand and close more business.
If you haven’t spent time in Overdrive 2.0, you’re missing out; there is an incredibly diverse set of resources to assist and even automate things like email blasts, social media, thought-leadership content and promotional material.
In my experience, there are three foundational best practices you should implement as an MSP or MSSP, especially when you’re scratching and clawing for sales in the competitive cybersecurity landscape.
Set Your Goals
Let me take you back a few years. As SonicWall’s FY2016 drew to a close, ProviNET scheduled a meeting with our SonicWall territory account manager (TAM). He really challenged us to set a goal for FY2017 to move up a level in our SonicWall SecureFirst partnership.
He was right. We had been a SonicWall ‘Silver’ partner for several years and with our FY2016 sales, we weren’t too far away from being eligible for ‘gold’ if we also achieved some additional sales and technical certifications. But we weren’t quite sure how to push ourselves across that next threshold.
Our TAM had the answer. He turned us on to SonicWall Overdrive 2.0, the company’s fully automated partner marketing engine designed specifically around key go-to-market themes, campaigns and resources. He assured us that if we invested a little bit of time into marketing, we’d be able to elevate our partnership. With that, our goal was set: we were going to become a SonicWall gold partner in 2017.
SonicWall Overdrive offers turnkey campaigns SecureFirst partners can launch to build awareness, create pipeline and close deals.
Develop Your Strategy
Without a strategy, marketing is a lot like throwing bubble gum at the wall and seeing if it sticks. Spend some time intentionally thinking through four things:
- Who your organization will target
- What methods it will use to target
- How often you will target potential buyers
- How you will track and measure your efforts
If you have a dedicated marketing person, consider developing a multi-faceted campaign that the marketing team can execute. The campaign should include multiple touchpoints across a variety of channels. Overdrive is an easy-to-use tool, regardless of your resources, to reach your customers and prospects.
At a basic level, consider sending an email blast, posting on social media, sending a postcard, publishing whitepapers or case studies on the website, and using the Overdrive 2.0 content to educate customers and prospects.
SonicWall Overdrive 2.0 packages content and resources partners can leverage as part of one-off marketing efforts or fully integrated campaigns.
We had success using much of the Overdrive 2.0 content to point people to a dedicated SonicWall landing page within our own website where prospects could fill out a form and be contacted to learn more. And because these campaigns were launched by us, they were contacting us for more information (i.e., we received the lead and the opportunity to either nurture the prospect or close the deal).
Even sophisticated customers will not always be able to grasp the full advantages and capabilities of the Capture Cloud platform after just one touchpoint. It will be important to educate them on the advantages that the orchestration of these security products and services can provide to them.
But don’t forget about existing customers here, too. For us, the Overdrive 2.0 marketing content was a motivator to look across our existing SonicWall customer install base and look for opportunity to add additional services like the SonicWall Capture Advanced Threat Protection (ATP) sandbox service or secure email solutions.
Analyze Your Results
There is remarkably valuable information in marketing analytics reports. Whether you use a marketing automation tool, a website analytics engine or even just campaign reporting from Overdrive, it can help your sales staff be more efficient and effective in their sales efforts.
Our team uses a combination of HubSpot, Google Analytics, and the email reports from Overdrive 2.0 to glean insights into customers and prospects who may or may not have an interest in particular marketing campaigns.
We can track if an individual opened an email four times, clicked the link to our site, or engaged with us on social media on several occasions to gauge if there is a genuine interest. Our sales team then makes those prospects and customers the focus of contact for more direct conversations — and that often leads to close deals.
Bear in mind, the goal of marketing is not to sell. These are two very different activities. For ProviNET, we define marketing as a process where we:
Our sales team has a very different, yet complementary, function:
SonicWall Overdrive 2.0 has been an invaluable resource for our team to really accomplish all four of our marketing objectives. By using the assets available in Overdrive 2.0, we’re providing meaningful education about the necessity and value of security products and services. We can position those assets in a compelling and efficient manner to provide the most value to our prospects and customers.
Even better? All registered SonicWall SecureFirst Silver, Gold and Platinum partners in good standing are eligible to use the SonicWall Overdrive 2.0 platform, at no cost, through the SonicWall SecureFirst Partner Portal.
About ProviNET
ProviNET is a SonicWall SecureFirst Gold Partner. For nearly three decades, ProviNET has delivered trusted technology solutions for senior living and post-acute healthcare organizations. Whether it’s a single project or full-time onsite work, ProviNET designs and implements customized solutions so healthcare organizations can focus on core services.
ProviNET’s tight-knit group of experienced, industry-certified personnel are focused on customer satisfaction. They are a reputable organization, fulfilling immediate IT needs and helping plan for tomorrow. They are ready to put their extensive knowledge to work for healthcare, developing strategies and solving challenges with the latest technology.
To learn more about ProviNET, please visit www.provinet.com.
Explore SonicWall Overdrive 2.0
SonicWall empowers SecureFirst partners with online tools to run demand- generation campaigns, increase social media awareness, build pipeline and close deals.
TRY IT NOW Not a SonicWall SecureFirst Partner?
The SonicWall SecureFirst Partner Program accelerates our partners’ ability to be thought-leaders and game-changers in the ever-evolving security landscape. From superior products and technical expertise, to aggressive margins and partner loyalty, when you become SecureFirst partner with SonicWall, you partner to win.
BECOME A PARTNER