Cybersecurity News & Trends – 10-30-20
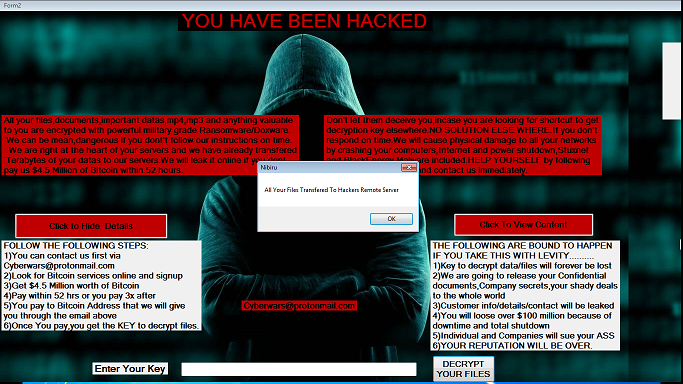
This week, Ryuk is on the rise, medical records are on display, and Maze is on its way out.
SonicWall in the News
Amid Pandemic, Hospitals Warned of ‘Credible’ and ‘Imminent’ Cyberthreat — ABC News
- SonicWall’s Q3 threat data detailing the increase of Ryuk ransomware is cited in this article, which centers around FBI’s warning of potential attacks against healthcare providers.
Review: The SonicWall SWS12-10FPOE Switch Simplifies Security — BizTech
- This article reviews the SWS12-10FPOE Switch and mentions the benefit the product will have on small businesses and branch offices.
FBI Warns of Imminent Wave of Ransomware Attacks Hitting Hospitals — CNET
- SonicWall’s Q3 Threat Data on the surge of ransomware is included in CNET’s article covering potential attacks on the healthcare industry.
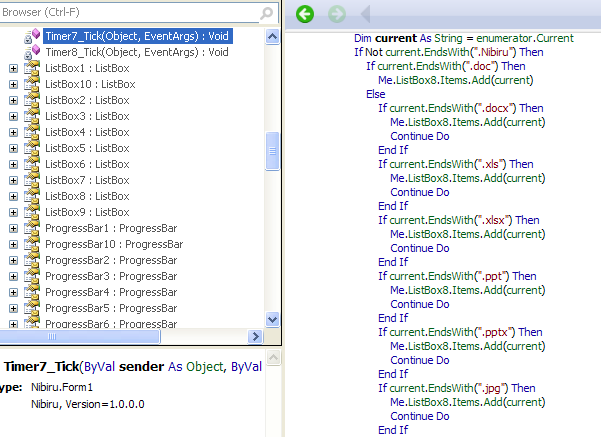
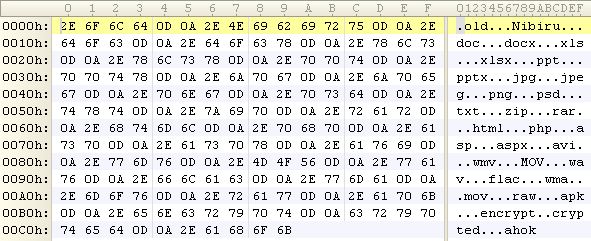
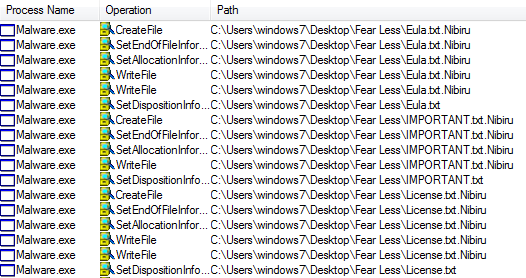
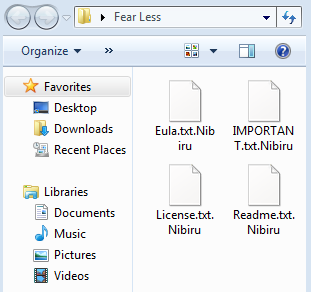
Ryuk Wakes From Hibernation; FBI, DHS Warn of Healthcare Attacks — Cybersecurity Dive
- Samantha Schwartz included SonicWall’s Q3 Threat data and a quote from CEO Bill Conner in an article on possible upcoming attacks on the healthcare industry.
Venomous Bear and Charming Kitten Are Mentioned In Dispatches. Ryuk Targets Hospitals. Maze Shutdown? — CyberWire
- CyberWire included a link to SonicWall’s Q3 Threat data press release in the “Cyber Trends” section of its daily newsletter.
Malware Levels Drop Attacks Become More Targeted — BetaNews
- BetaNews’ article cites SonicWall’s Q3 Threat data, highlighting the drop in malware and the rise in ransomware and IoT malware attacks so far in 2020.
Ryuk Ransomware Responsible for One Third of All Ransomware Attacks in 2020 — Security Magazine
- Security Magazine reports on SonicWall’s Q3 Threat Data, highlighting the surge in Ryuk ransomware that’s occurred in 2020.
Industry News
Maze ransomware is shutting down its cybercrime operation — Bleeping Computer
- The Maze cybercrime gang is shutting down its operations after becoming one of the most prominent ransomware groups.
Trump Campaign Website Is Defaced by Hackers — The New York Times
- The defacement lasted less than 30 minutes, and the hackers appeared to be looking to generate cryptocurrency.
Microsoft says Iranian hackers targeted conference attendees — The Washington Times
- Iranian hackers reportedly posed as conference organizers in an attempt to break into the email accounts of “high-profile” people.
EXCLUSIVE: Medical Records of 3.5 Million U.S. Patients Can be Accessed and Manipulated by Anyone — Security Week
- The results of 13 million medical examinations relating to around 3.5 million U.S. patients are unprotected and available to anyone on the internet, SecurityWeek has learned.
Spy agency ducks questions about ‘back doors’ in tech products — Reuters
- The U.S. National Security Agency is rebuffing efforts by a leading congressional critic to determine whether it is continuing to place so-called back doors into commercial technology products, a controversial practice that critics say damages both U.S. industry and national security.
FBI: Hackers stole government source code via SonarQube instances — Bleeping Computer
- The FBI issued a flash alert warning of hackers stealing data from U.S. government agencies and enterprise organizations via insecure and internet-exposed SonarQube instances.
Election Officials Warn of Widespread Suspicious Email Campaign — The Wall Street Journal
- Local election officials in the U.S. have been receiving suspicious emails that appear to be part of a widespread and potentially malicious campaign targeting several states.
Bitcoin Approaches Highest Level Since Post-Bubble Crash in 2018 — Bloomberg
- Bitcoin is approaching levels not seen in nearly three years.
US Treasury Sanctions Russian Institution Linked to Triton Malware — Dark Reading
- Triton, also known as TRISIS and HatMan, was developed to target and manipulate industrial control systems, the US Treasury reports.
REvil ransomware gang claims over $100 million profit in a year — Bleeping Computer
- REvil ransomware developers say that they made more than $100 million in one year of extorting large businesses.
Data breach at Finnish psychotherapy center takes a darker turn with extortion attempts — Cyberscoop
- Patients of a prominent Finnish psychotherapy practice reportedly had their information posted on the dark web after being told they could protect their data by directly paying a ransom.
In Case You Missed It
- Q3 Cyber Threat Intelligence Details a September to Remember — Amber Wolff
- 5G and the Security of Connected Devices — Amber Wolff
- Capture Client: Purpose-Built for the Distributed Workforce — Brook Chelmo
- Securing Internet-Connected Devices in Healthcare — Amber Wolff
- Another Reason to Not Pay the Ransom: Trouble with Uncle Sam — Amber Wolff