The first malicious Xposed Framework Module ( November 7, 2014 )
One of the key strengths of the Android ecosystem is the extensive degree of customization that is possible. Android by itself provides an immense array of options to customize the device to our liking but Rooting a device can add almost limitless possibilities to tailor the device as per our needs and style. There is a long list of custom Android variations from the one that comes by default on the device, these variations are referred to as custom ROMs. The custom ROMs available are each distinct from one another with each one having their own style and features.
Adding a custom ROM over the stock ROM on a device is one way of giving your old phone a complete makeover but the process can be tedious. There are a lot of parameters to consider when changing the stock ROM of a device, a single mis-step can render the phone useless. This is often referred to as bricking the phone. Due to the risks involved in this process, recently people have steered towards an alternate way to unlock the customization potential of their device and keeping the risks low at the same time. Enter The Xposed Framework.
There is a process responsible for running all Android apps called Zygote, this is launched by /system/bin/app_process executable. Xposed framework replaces this executable with a modified version that loads an additional Jar file called XposedBridge.jar. This file acts as a bridge into Zygote allowing us to run custom code as if it was originally part of Zygote. The custom code introduced into the system gives us the abilitiy to customize system features as if we are running a custom ROM but keeping the risk of bricking the device to a minimum. Xposed Framework does require the phone to be rooted as it needs root priviliges to add custom code into the system.
Xposed has a number of modules that add additional features to your device, some popular modules include:
- BootManager – Choose what apps you want to prevent running upon system startup
- Tinted Status Bar – Change status bar color based on what app is running
- Youtube AdAway – Disable ads from youtube app
The process of enabling these modules on the device is as follows:
- Download the required modules directly or via Xposed Framework
- Install and activate the module in Xposed
- Reboot the device for the change to take effect
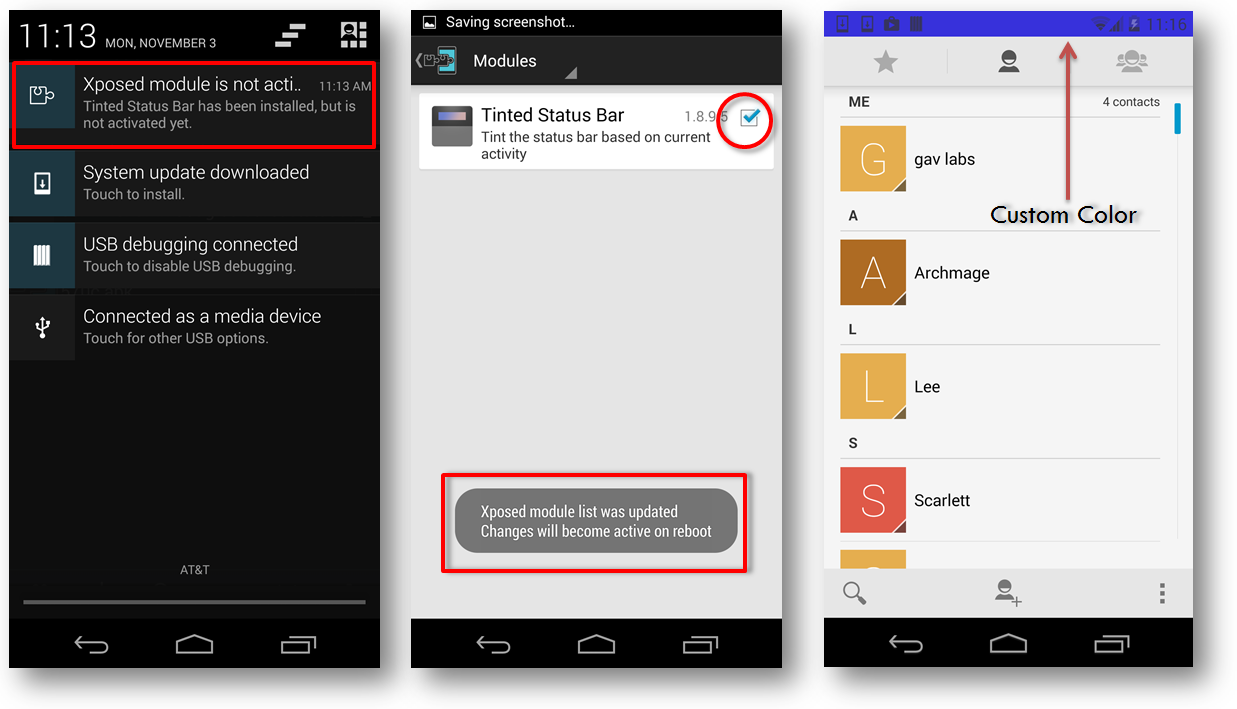
Giving Root privileges to Xposed and allowing it to add code to the system does pose a security risk, however a module will not be active unless the users enables it in Xposed and reboots the phone. This gives some degree of user intervention and prevents anonymous modules to automatically start using Xposed without seeking user permission. However if the user enables a module in Xposed then it has free reign over the system as it can hook onto other apps and extract sensitive information silently without the victim’s knowledge. Dell SonicWALL Threats Research team received one such sample that is actually the first malicious Xposed module.
The following screen is visible once this module has been installed and activated on the device:

We could not find any sort of advertisements for this app as to how it tries to lure the victims into installing it. Judging by the options presented it looks like this module can hide Root apps, hide Xposed Framework and hide itself. There are legitimate apps available like “Hide My Root” and even an Xposed module called “RootCloak” that hide the root apps. The malicious module thus tries to blend-in with such similar apps. During installation, it asks for a number of sensitive permissions which raises suspision about its possible true motive, the permissions requested are as follows:
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
This malicious module has a number of Receivers that are triggered when certain events occur. BootReceiver is activated each time the device boots up, this receiver checks and creates a database if its not created already for storing gathered information.

Service is an Android app component that runs in the background to carry out long term tasks. Even if an app is not active on-screen, its services can be constantly running in the background. After BootReceiver ensures that the database is created successfully it starts a service called GodService which starts another service called TeamService. TeamService keeps an eye on incoming SMS messages and scans them for commands coming from the server. The commands are present in the AirService class, this Trojan has a roster of over 40 commands. Some interesting commands are as follows:
|
|
|
|
|
|
|
Additionally it has few commands that are targeted towards specific messengers as well:
|
|
|
|
|
|
|

Additionally the Trojan places hooks and constantly checks if InputType value for EditText operation for an app is 129. Value 129 has been set by Android to correspond to Password textbox, it saves details about the app for which this information belongs. Using this component the malicious module can spy on passwords entered by a user on his infected device.

Overall this malicious Xposed module is aimed at gathering sensitive information from the victim’s device with in-built components as well as via commands received remotely from the attacker. But what ma
kes this Xposed module extremely dangerous is that it signifies a new evolutionary step for Android Malwares by targeting the Xposed Framework. Xposed has been gaining huge popularity owing to the remarkable customization options it gives to a user. Currently Google scans and monitors the apps on Google Play for malicious content, but Google is not responsible for any security risk that may stem from Xposed modules. The only way a user can get any information about the reliability of Xposed modules is by checking more information about it on the popular Android forum XDA Developers.
There has been a lot of discussion about the security issues that may be caused because of Xposed Framework. While we cannot deny the rich set of features that Xposed Framework introduces to someone who wants to customize their Android device, it is clear that the security risks introduced by it cannot be overlooked. Ultimately, the onus of security of an Android device in part rests on the user, not Rooting the device and downloading apps only from Google Play are potent ways to ensure a safe and secure Android experience.
Dell SonicWALL Gateway Antivirus provides protection against this threat via the following signature:
- GAV:AndroidOS.Malicious.Xposed (Trojan)




