Fake AnyDesk Drops a Myriad of Malicious Tools
Overview
This week, the Sonicwall Capture Labs threat research team analyzed a fake copy of AnyDesk. AnyDesk is a legitimate remote desktop application commonly used by tech support agents to troubleshoot computer problems remotely and provide remote assistance. Cybercriminals are known to use such tools by silently installing the application and then using it to remotely control a victim’s machine. However, in this scenario, an unsuspecting user is tricked into installing what seems to be a legitimate copy of AnyDesk. In reality, the download comes with an assortment of malicious software.
Infection Cycle
The malware is hosted on a website with a domain name “Anydesk.cyou” that closely resembles the real AnyDesk website.
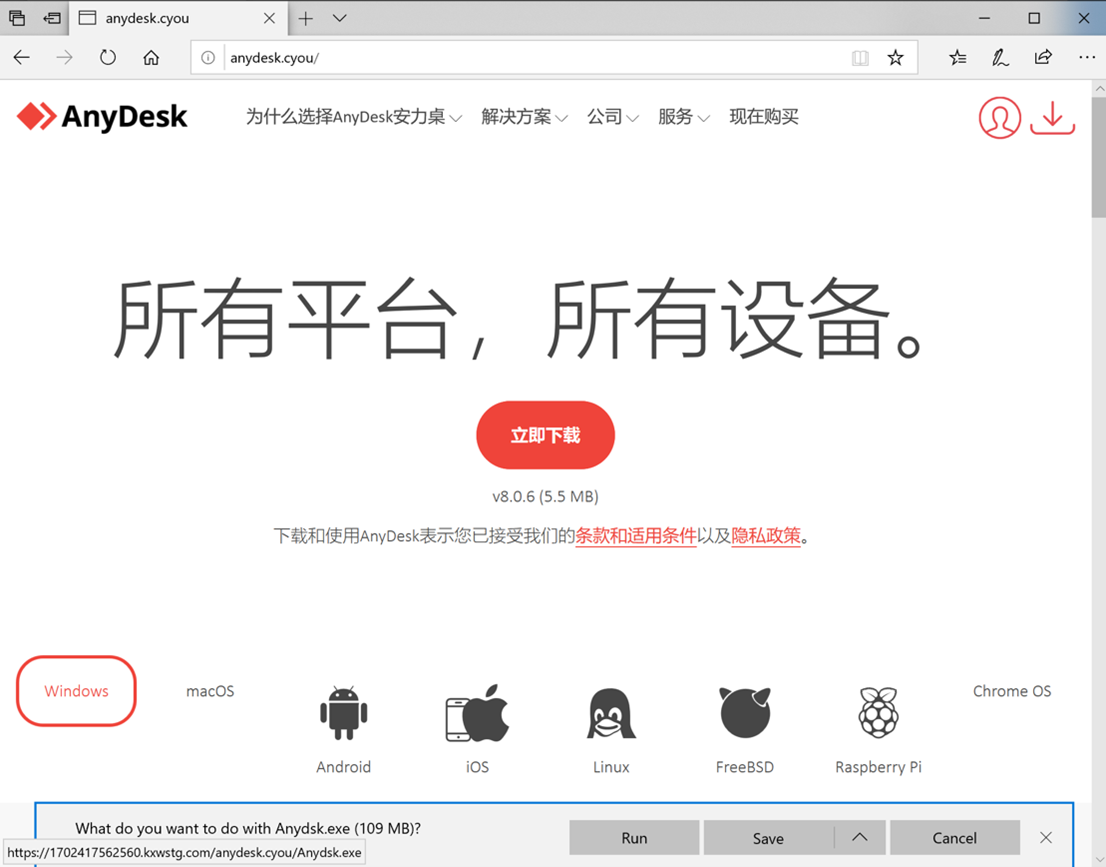
Figure 1: Fake AnyDesk website hosting a fake AnyDesk application
The website downloads a file named “Anydsk.exe” which uses the legitimate AnyDesk icon.

Figure 2: Fake application named Anydsk.exe next to a copy of the legitimate AnyDesk.exe using very similar icons
Upon execution, it opens up an installation window that guides you through the installation process.
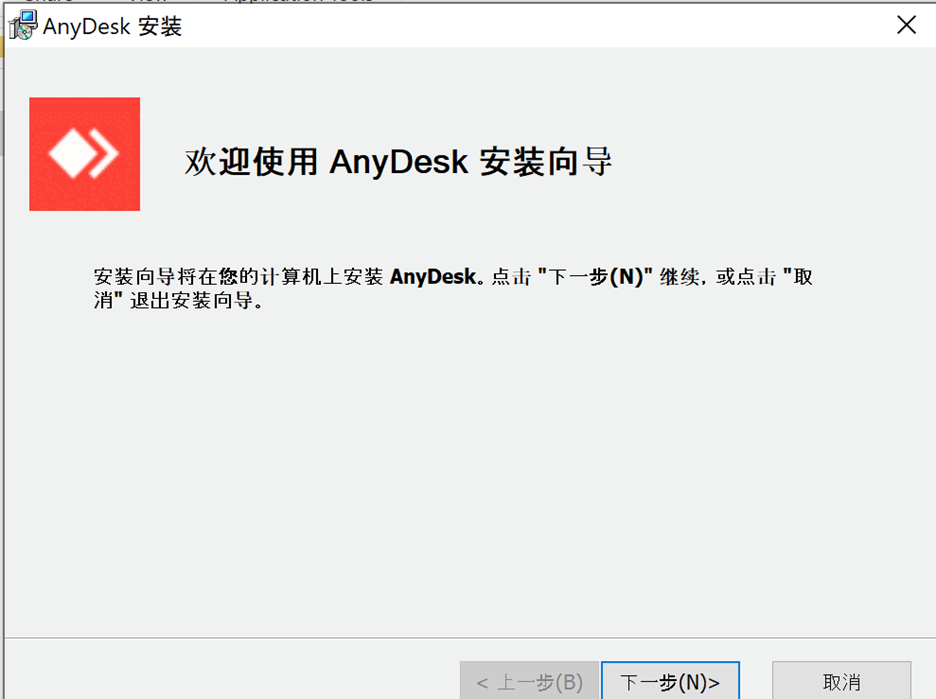
Figure 3: Fake AnyDesk installation window
This process in fact installs a legitimate copy of the software application in question, however it also installs other components.
The components of the legitimate AnyDesk software are installed in the following directory:
- %AppData%\Roaming\CAS_BYBAnyDesk\AnyDesk.exe
- %AppData%\Roaming\AnyDesk\ad.trace
- %AppData%\Roaming\AnyDesk\service.conf
- %AppData%\Roaming\AnyDesk \system.conf
- %AppData%\Roaming\AnyDesk user.conf
Upon completed installation, it adds a shortcut link to the user’s desktop which runs a legitimate copy of AnyDesk.
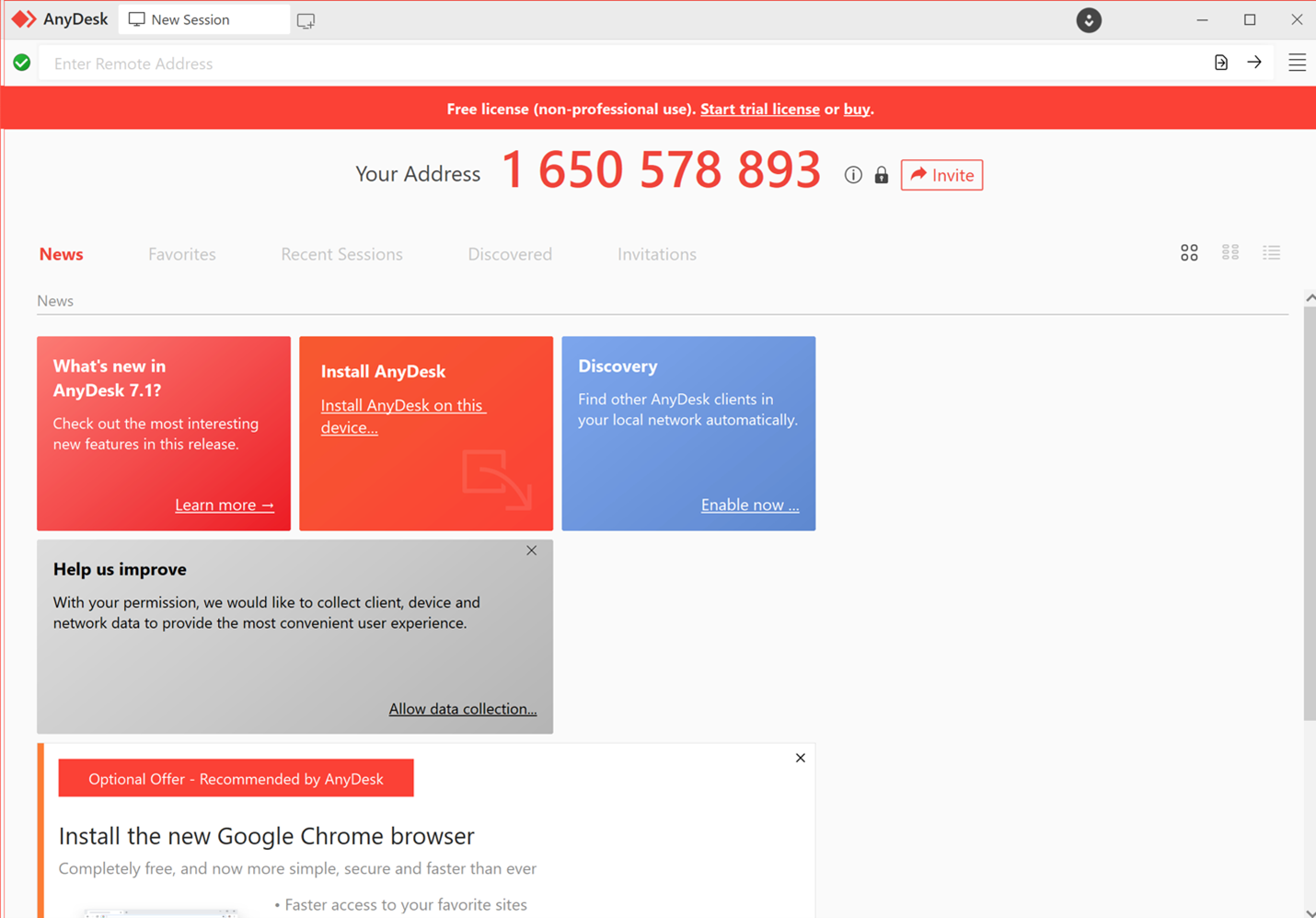
Figure 4: Running a legitimate copy of the AnyDesk software application
However, more component files have been installed along with AnyDesk in the %APPDATA% directory as seen in the figure below.
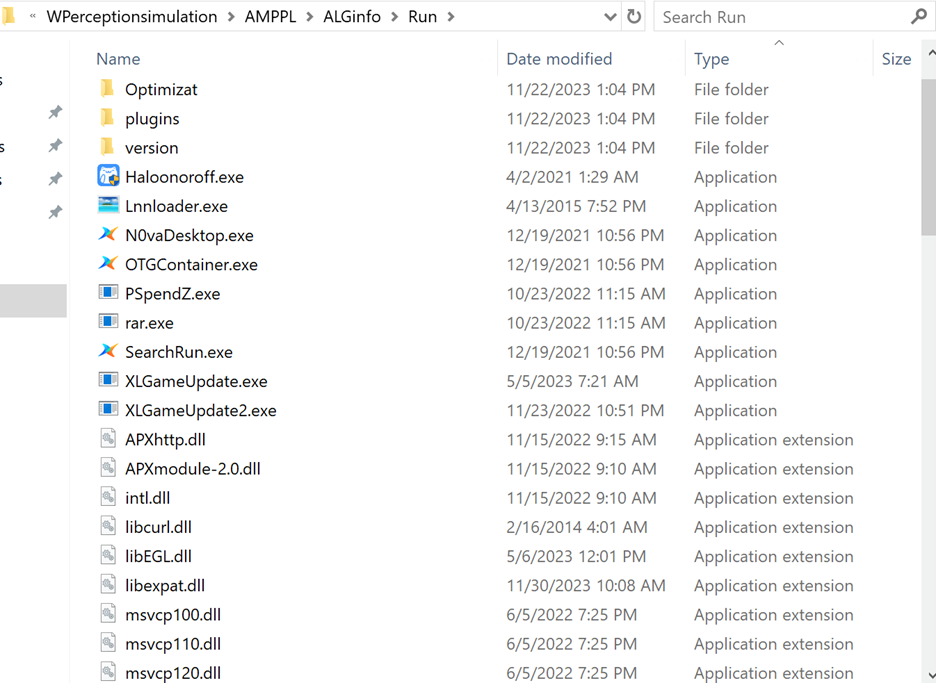
Figure 5: More files, both malicious and clean, were seen installed within a folder in the %APPDATA% directory.
During runtime, we have observed that N0vaDesktop.exe was used to spawn the legitimate wscript executable to run a file named “try.vbs” which contains the following code.
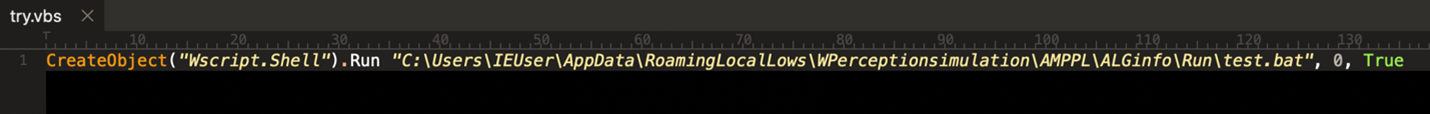
Figure 6: Contents of try.vbs
It executes a batch file named “test.bat” which then launches lnnloader.exe. Below are the contents of test.bat.
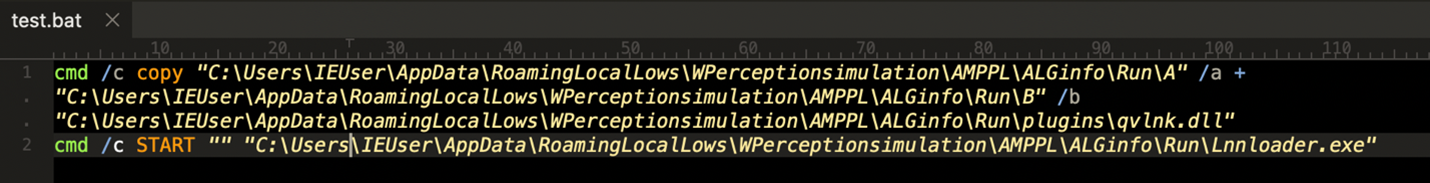
Figure 7: Contents of test.bat
Lnnloader.exe is used for reconnaissance and was seen perusing the file system and its registry.
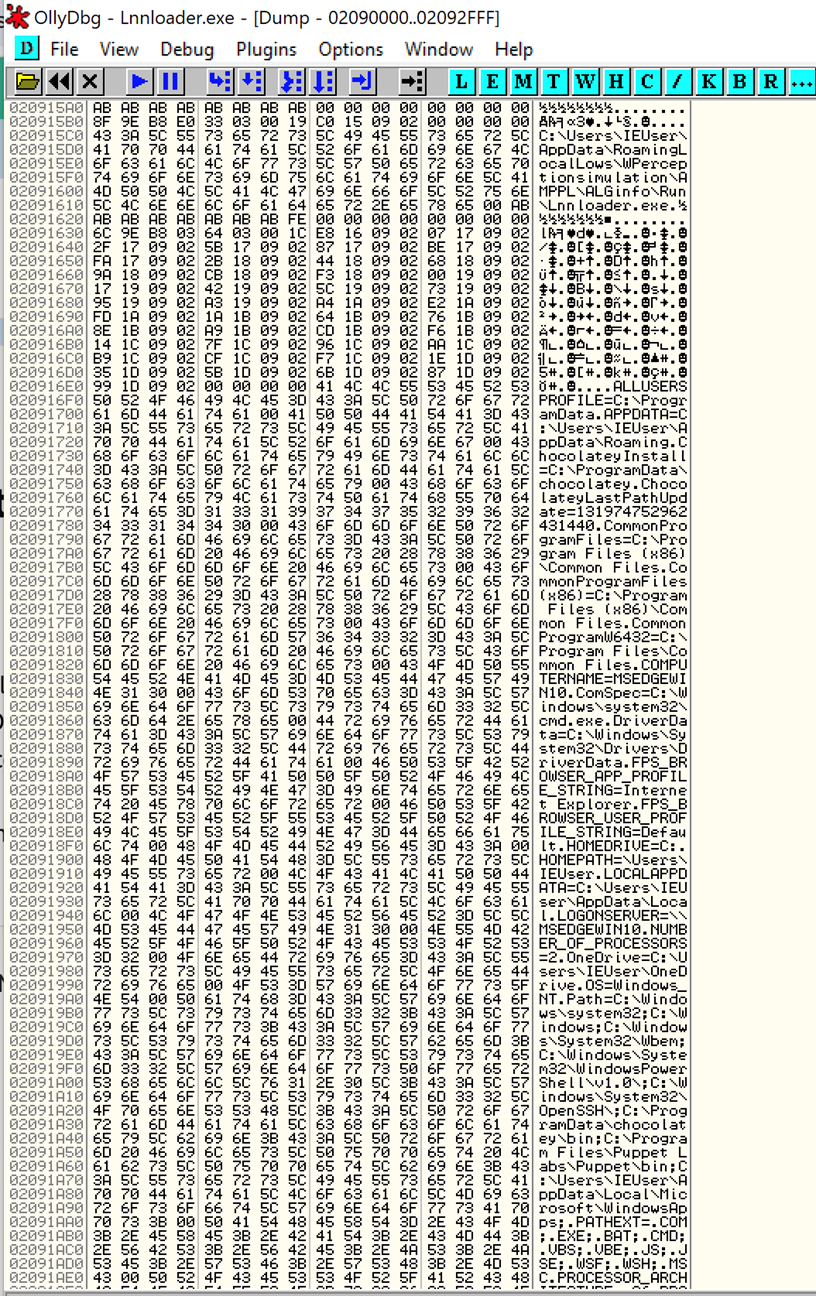
Figure 8: Memory dump of lnnloader.exe seen with the infected system’s information.
It then runs Haloonoroff.exe which was seen constantly connecting to a remote server.
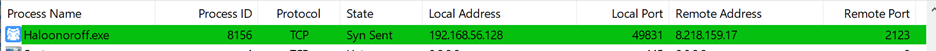
Figure 9: Haloonoroff.exe seen connecting to a remote server
A log file named “Haloonoroff_
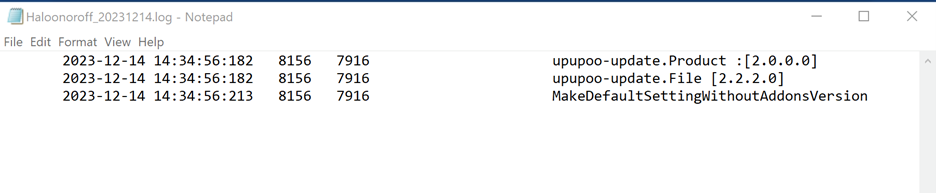
Figure 10: Event log for Haloonoroff.exe
OTGContainer.exe and SearchRun.exe were copies of N0vaDesktop.exe. PSpendZ.exe is a legitimate tool named PSSuspend, while rar.exe is the command line archiving tool. The rest are non-malicious files.
Interestingly, we also found traces of what seemed to be Tencent QQ -related files that were not seen used during our analysis.
Figure 11: Tencent QQ component files
SonicWall Protections
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Trojanspy.ANY (Trojan)
This threat is also detected by SonicWall Capture ATP with RTDMI™ and the Capture Client endpoint solutions.



