Google script being abused for Cryptocurrency fraud
SonicWall Capture Labs Research team has discovered an ongoing instance of cryptocurrency fraud that utilizes legitimate Google services, specifically Google Script macros. Threat actors intentionally target these platforms because they are both convenient to use and malicious code can evade detection by anti-malware systems.
Google Script macros are primarily designed to enhance productivity and streamline workflows within Google services. However, threat actors are now exploiting them for fraudulent purposes, finding ways to execute malicious code within the context of legitimate Google applications.
In this case, a PDF file is being circulated, containing a malicious URL that was created using Google Script. Once the user interacts with this URL, they are redirected to the actual fraudulent website.
Fig: PDF File
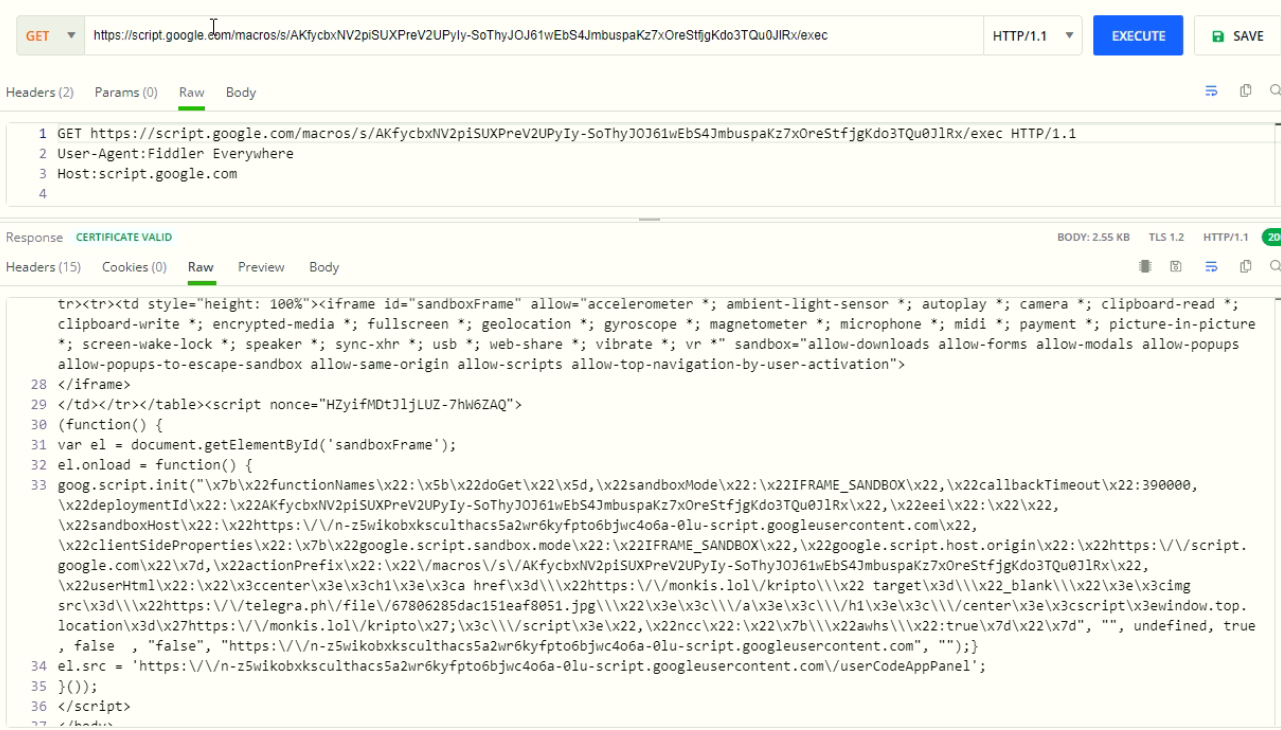
Below shown the response to the malicious URL using Google Script Macro.
Fig: Fiddler capture of malicious Google Script Macro
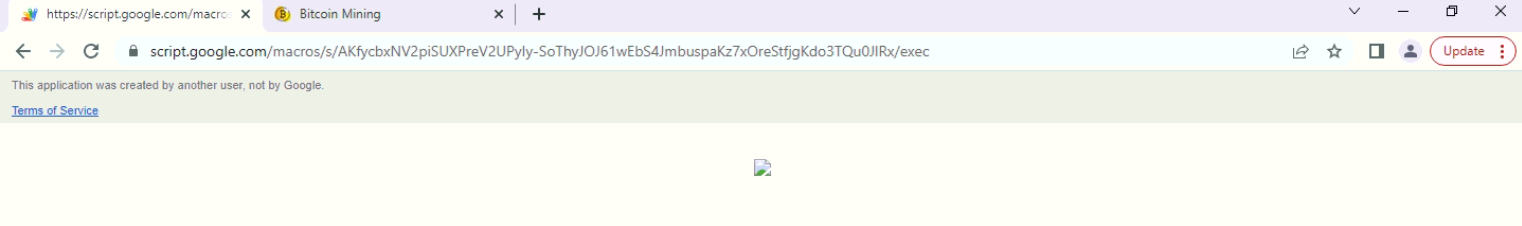
When the URL in the PDF file opens it shows Google’s message that this application was created by another user not by Google when clicked on the webpage it redirects to office[.]proprogramvipt[.]top
Fig: Google script malicious URL
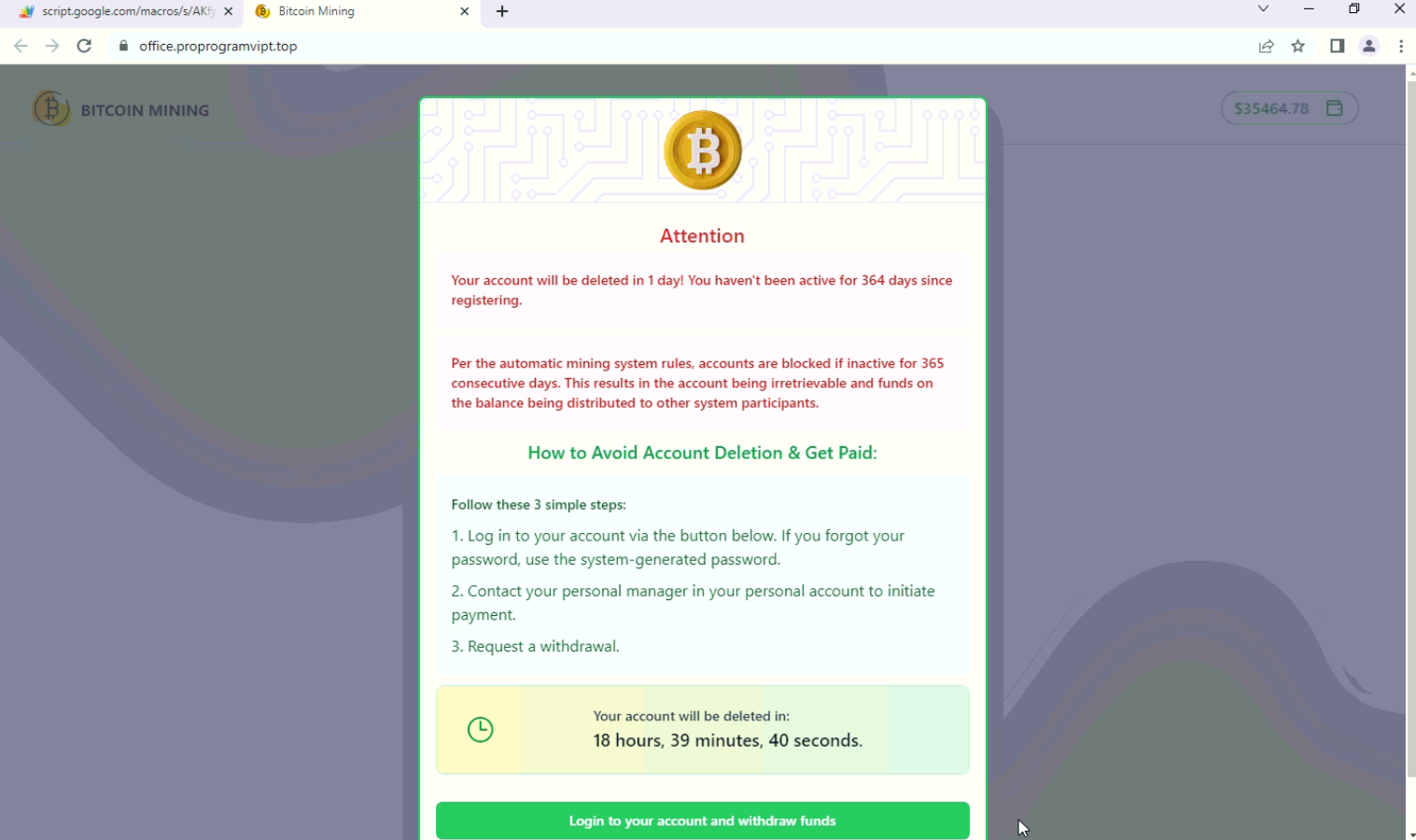
After redirection, On this deceptive webpage, user is confronted with a warning message indicating that their account is at risk of deletion due to inactivity. To add a sense of urgency, a countdown timer is displayed, suggesting that the account will be deleted imminently.
In order to prevent the account deletion and purportedly withdraw the funds (which, in reality, are non-existent), user is instructed to sign in.
Fig: Warning for account deletion
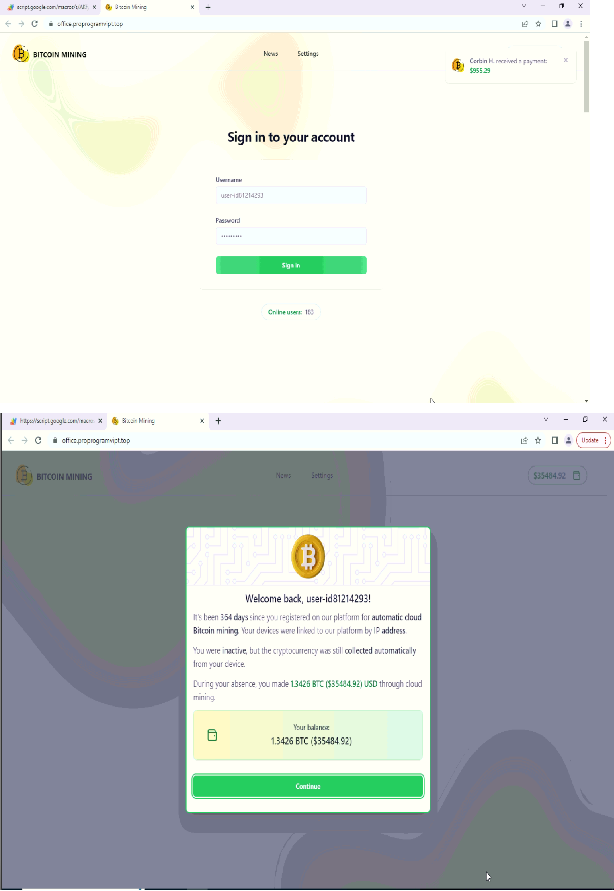
Upon signing in, user is presented with a prepopulated sign-in page that appears legitimate. The page is carefully designed to create an enticing welcome-back message, which includes displaying the user’s Bitcoin balance in both BTC and USD values. This serves as bait to lure user into continuing further with the process.
Fig: Sign-in & welcome message
To create an illusion of authenticity, various elements that mimic legitimate features commonly found on cryptocurrency platforms are presented. These elements include:
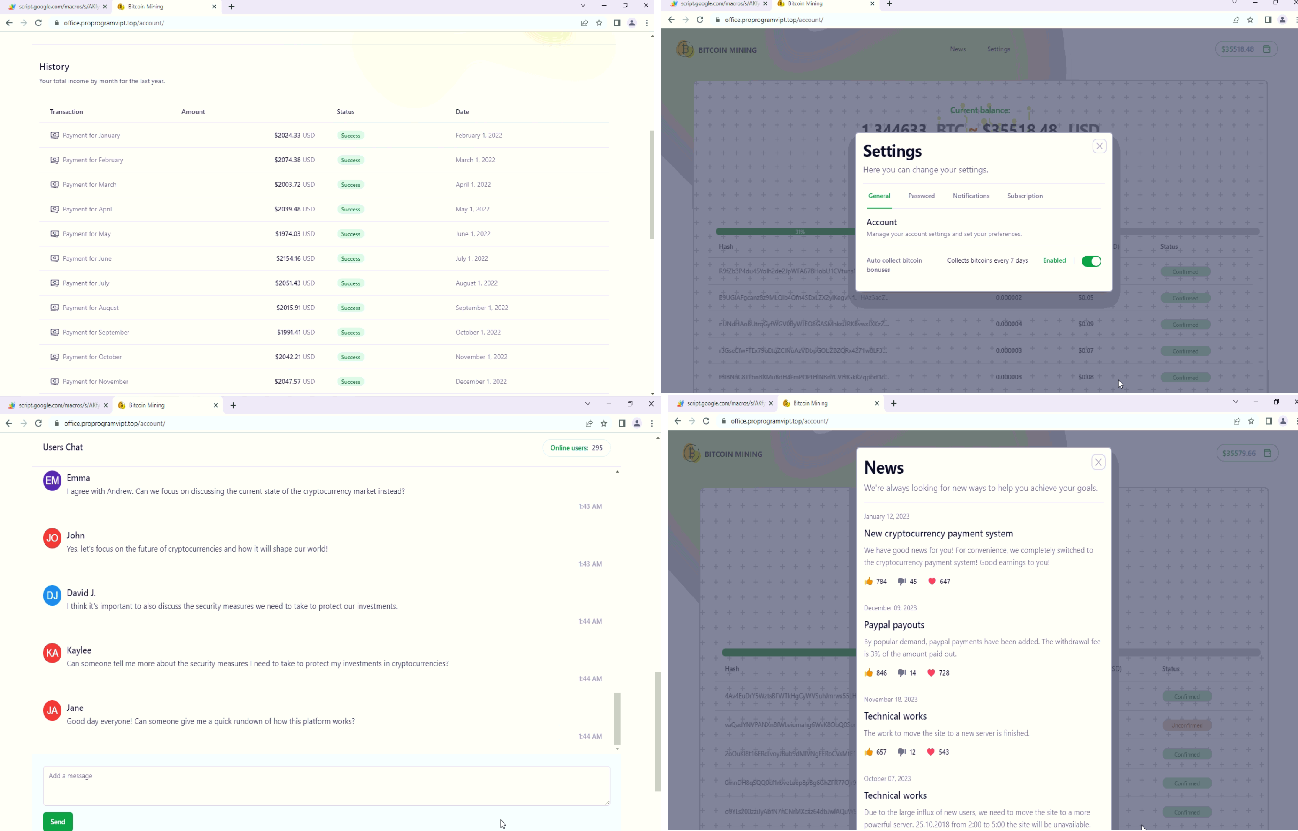
History: A fabricated transaction history is displayed, showcasing previous transactions to make the platform appear genuine.
User Chat: Fictitious comments and messages from fake users are shown, attempting to simulate user activity and engagement on the platform.
Settings: Users are provided with an option to collect bitcoins, along with the ability to change their password. This is aimed at giving the impression of user control and customization.
News: Fake news articles are presented, falsely claiming updates such as a switch to a new cryptocurrency system, the addition of PayPal payouts, or technical server-related updates. These news pieces aim to instill a sense of credibility and innovation.
All of these elements are carefully designed to create an atmosphere of legitimacy and trust, further deceiving users into believing that the fraudulent platform is genuine and reliable.
Fig: News, Settings, Chat & History
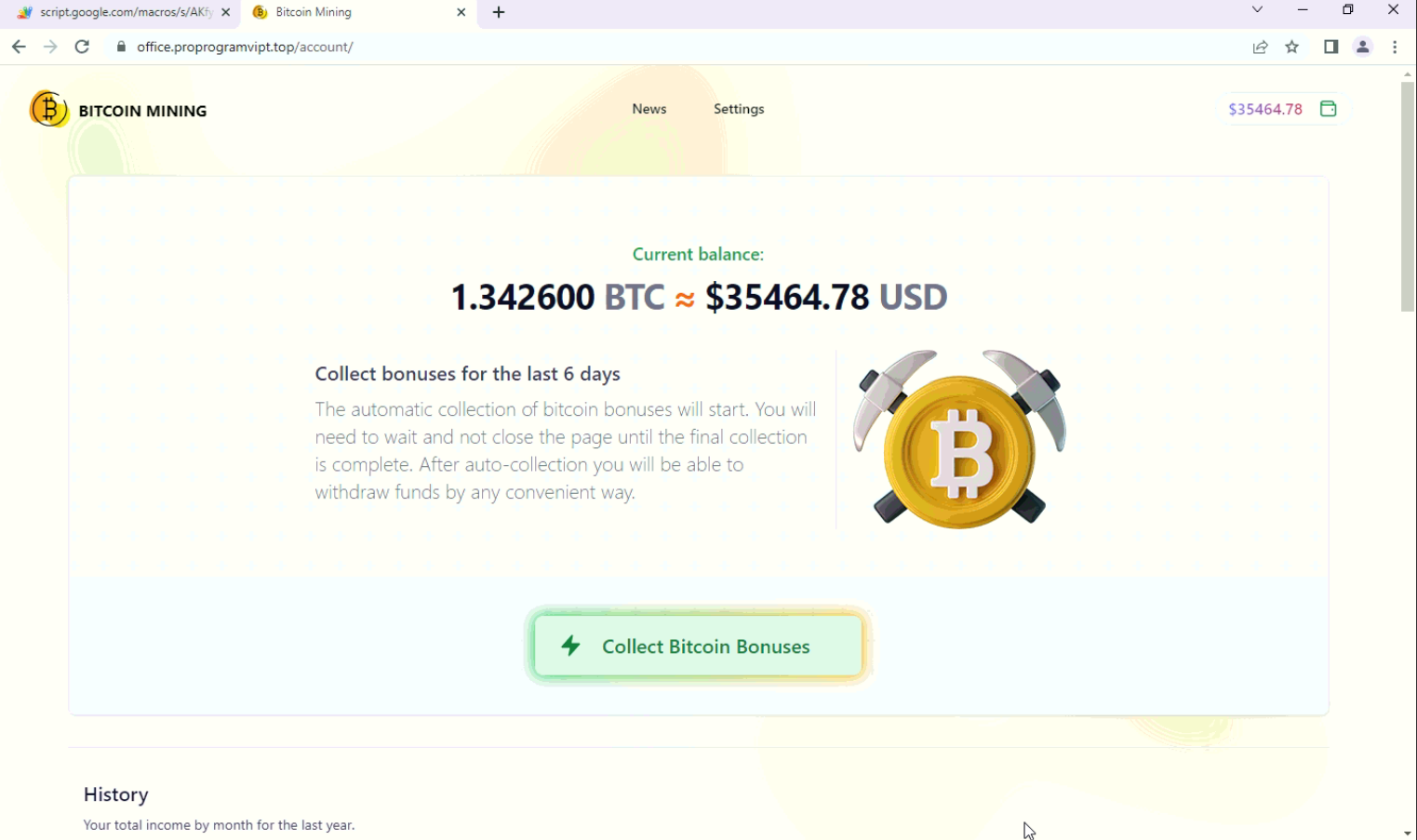
It shows the current balance in BTC & USD with a button to collect bitcoin bonuses.
Fig: Collect BTC Bonuses
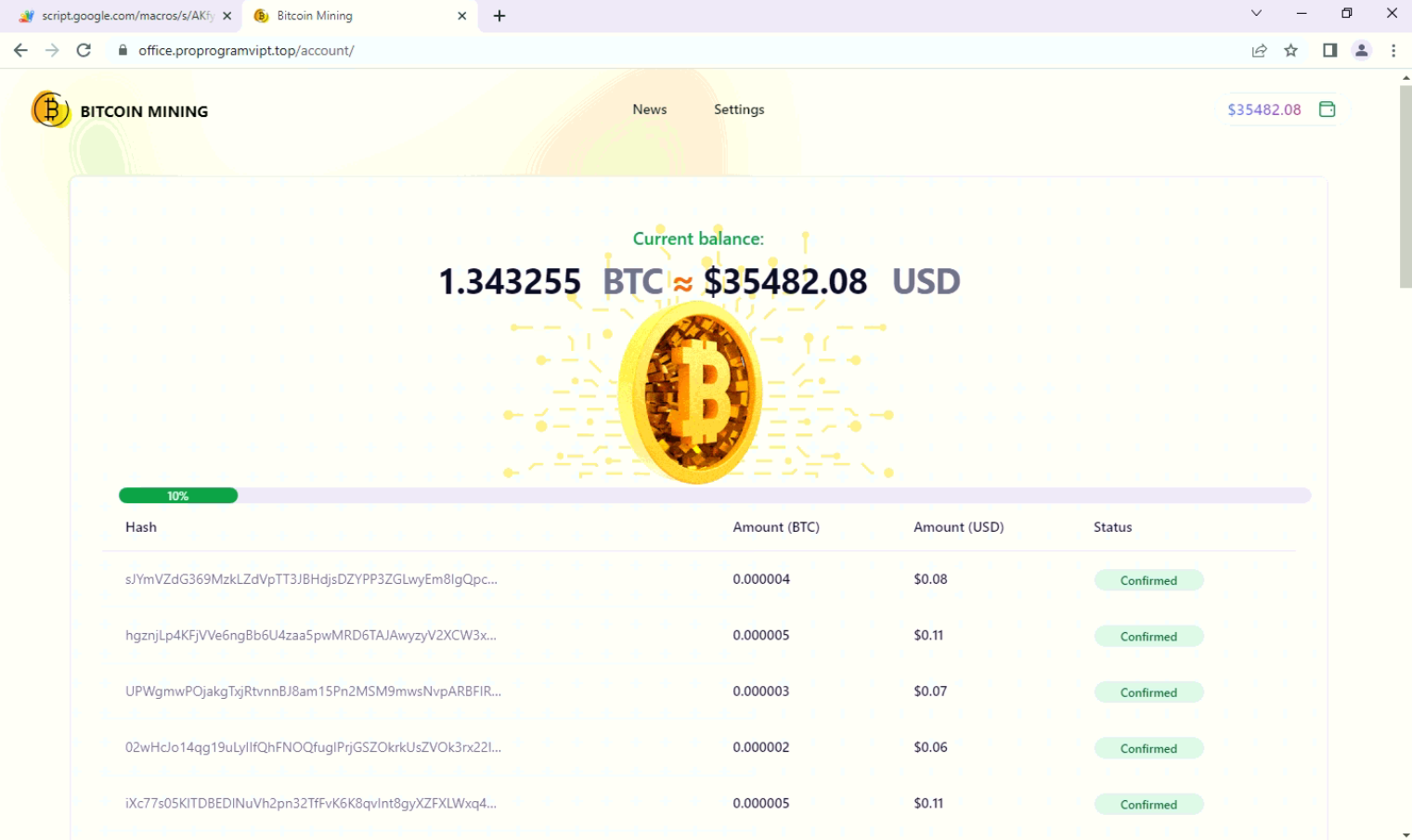
After clicking the “Collect Bitcoin Bonuses” button it shows a progress bar as if mining is going on the system with fake transaction hashes.
Fig: Fake mining
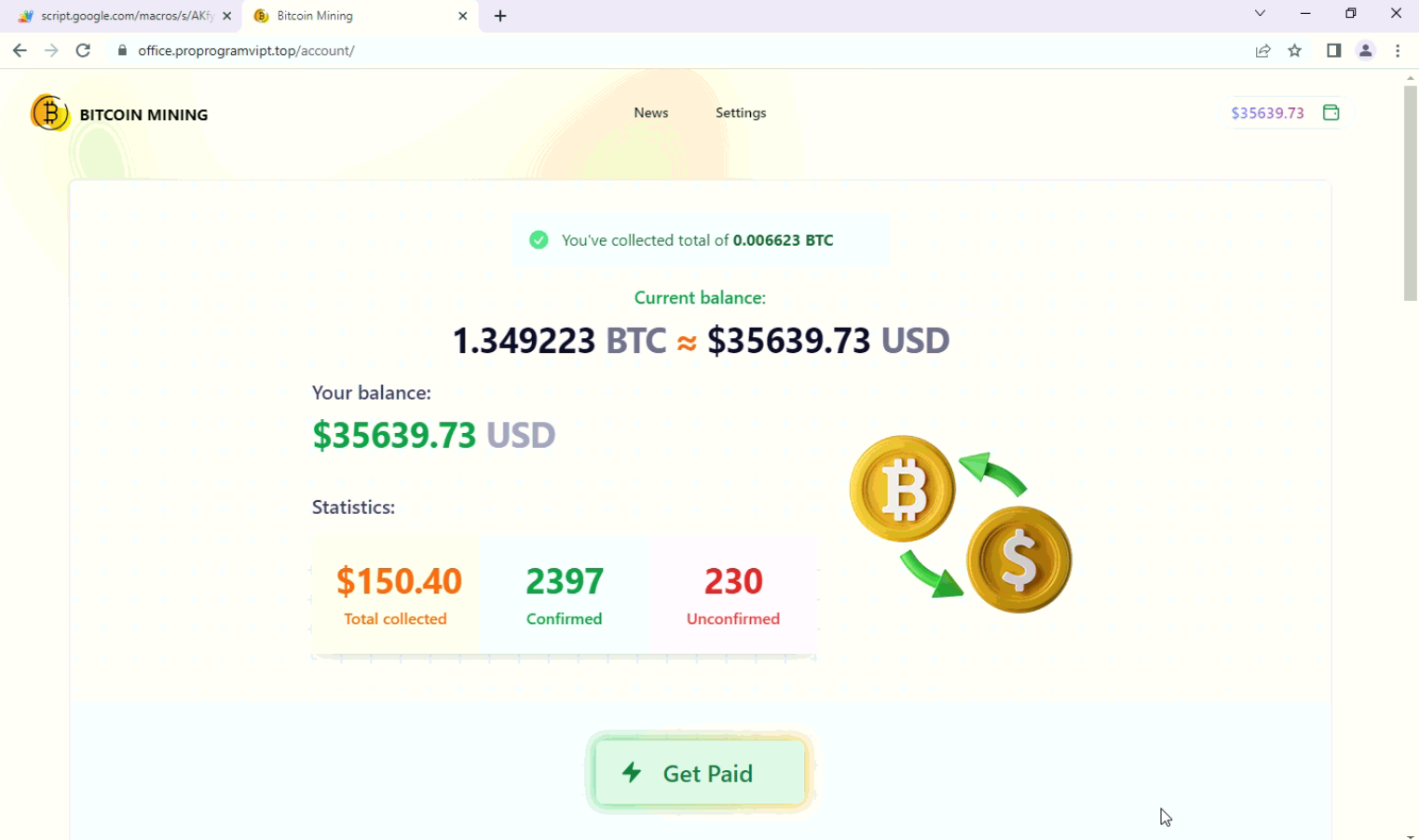
Once the progress bar reaches 100% it shows collected BTC and a get paid button.
Fig: BTC collection
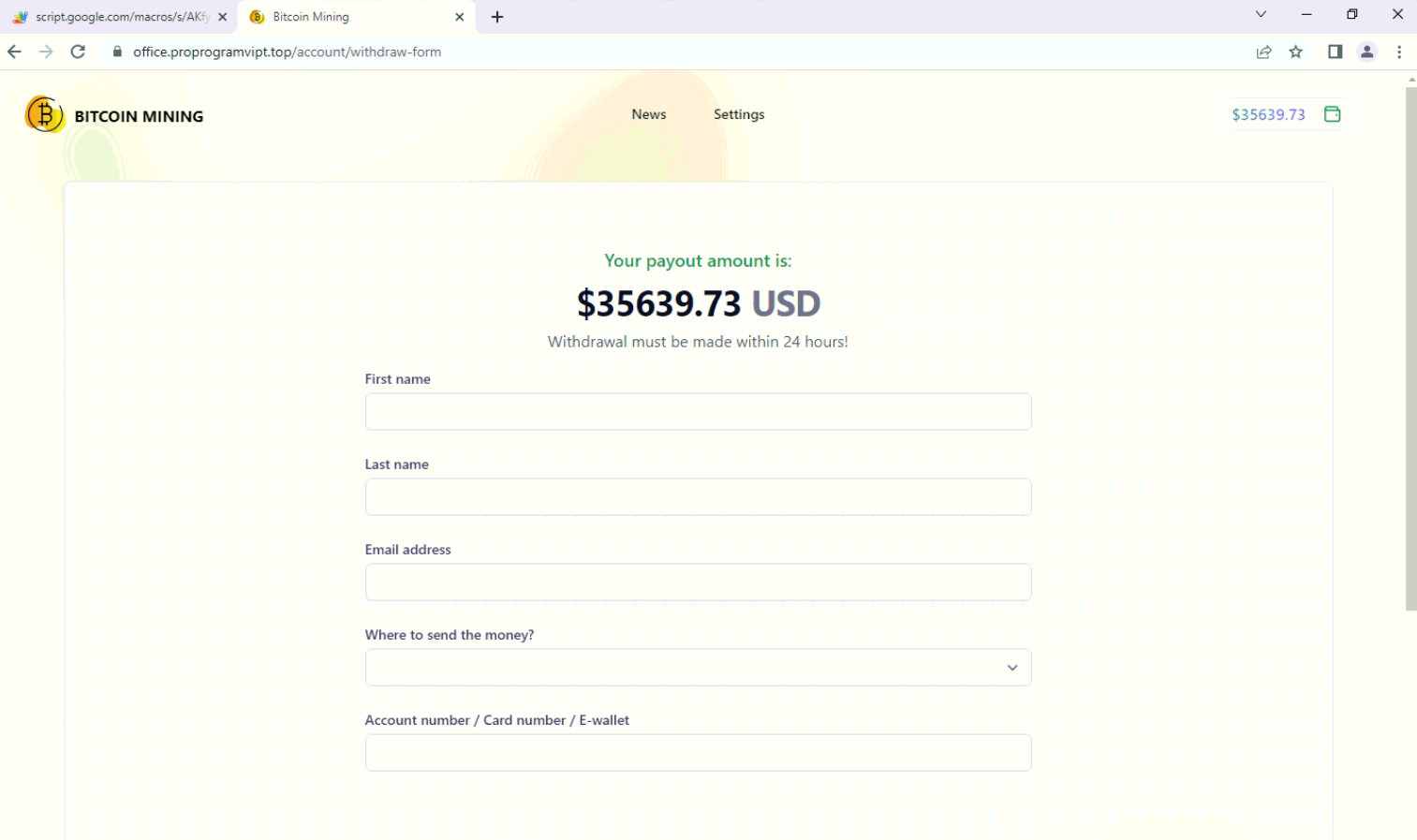
After clicking get paid it asks for the user’s personal details along with account/card details.
Fig: User’s details
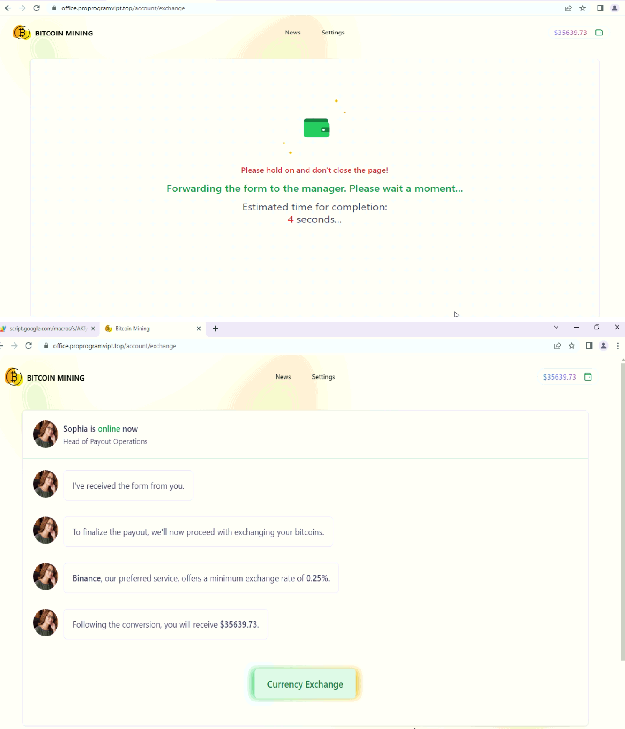
After getting all the details shows forwarding the details to the manager and they have their own chatbot which says details are verified without any validation even if random input is given.
Fig: Chatbot
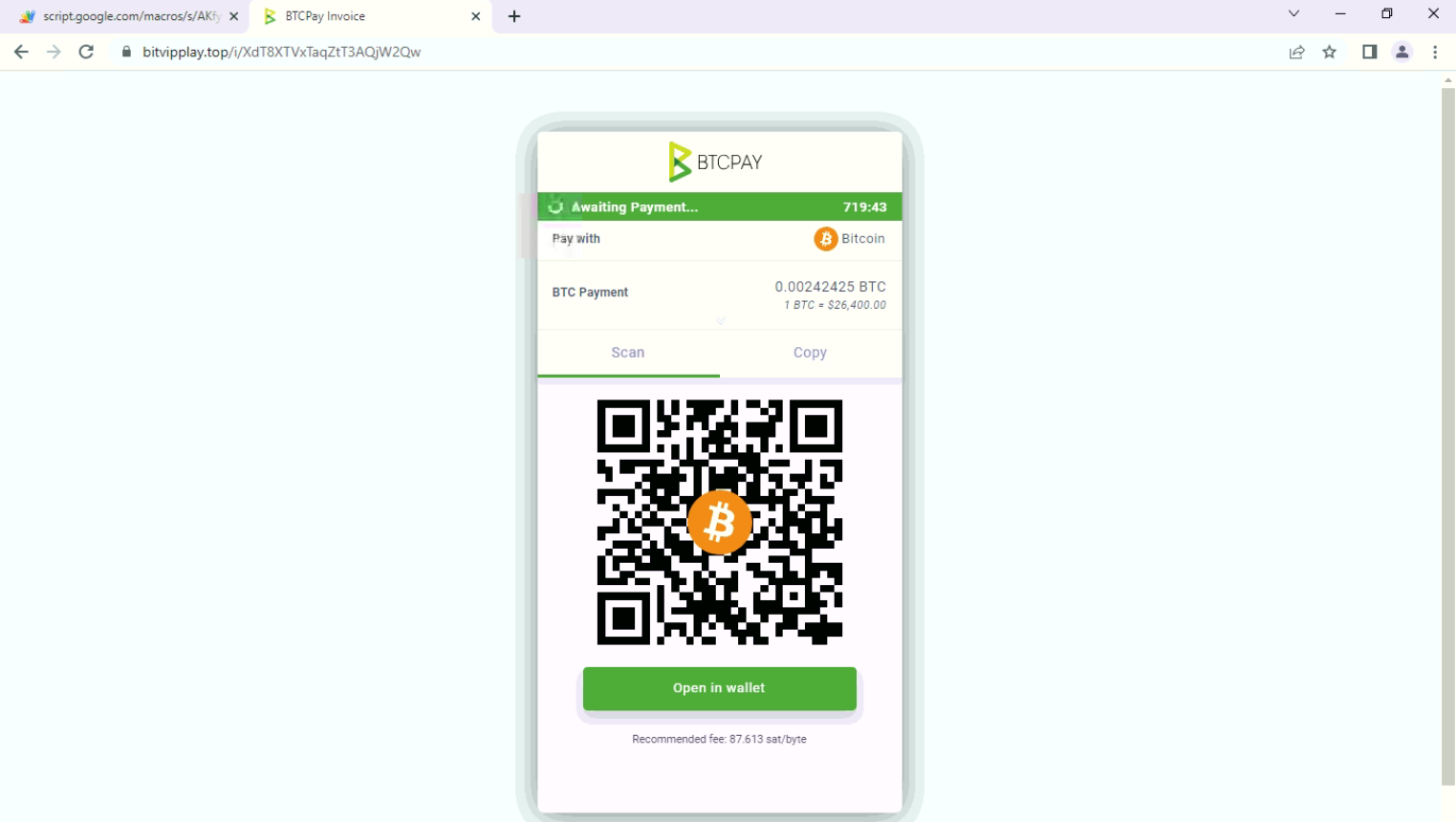
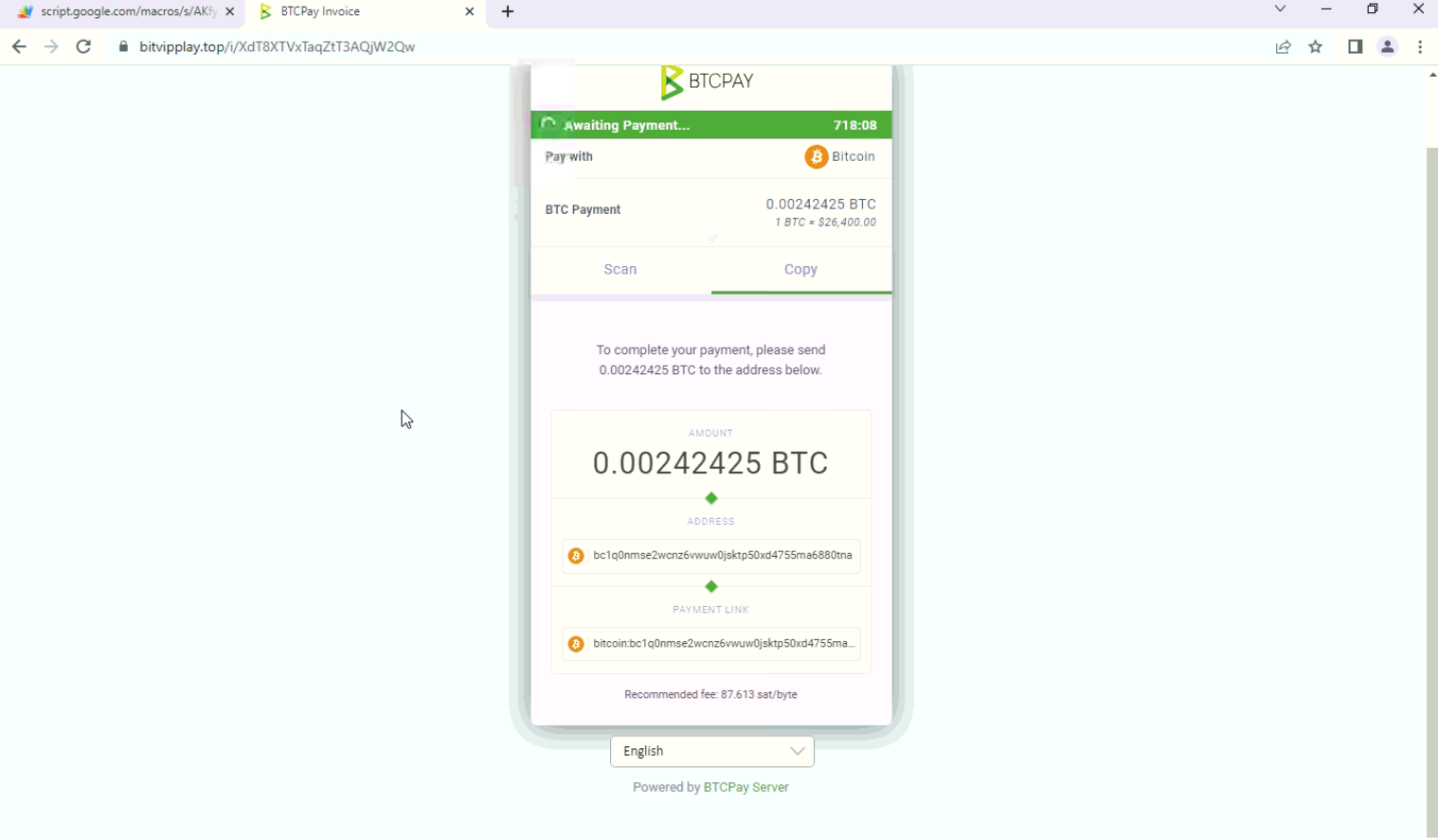
Then for currency exchange, it redirects to BTC pay & the user has to pay in bitcoin.
Fig: BTCPay
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: CryptoFraud.A (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.
Indicators of Compromise (IOC):
671ea7c95223fc15b2dbe03bc55acc44d81f0f69c1a3686c9f8db174df3e2710