Raspberry Robin Malware Is An Obfuscated Onion
This week, the SonicWall Capture Labs Threat Research Team analyzed a new sample of Raspberry Robin. First observed in May 2022 by Red Canary, Raspberry Robin is a worm that has evolved to be a delivery system for a host of threat actors and malware platforms (This currently includes EvilCorp, LockBit, BumbleBee, IcedID, and DEV-0950). It is unique in that the authors are using a custom obfuscation method that virtualizes the code and has 15+ layers to prevent detection and/or analysis, as well as deploying a custom Tor client for C2 communications.
Infection Chain
Raspberry Robin is known to spread via infected USB devices, utilizing the ‘AutoRun’ feature on plugin. The malware will run via a .LNK file on the USB drive that executes ‘MSIExec.exe’ to download a first-stage payload. Once the system is found to be a valid target, the second-stage payload drops and connects to a Tor address. Initial analysis of the dropper program shows that it begins as a small .zip file (950kb-1250kb) which unpacks another .zip file of roughly the same size. This second archive unpacks into a ~700MB setup file with a .cpl (Control Panel Item) extension, and a text file with instructions to run the installation (Figure 1). Successful execution creates persistence with a RunOnce Key in the registry (HKEY_CURRENT_USER/ and the next stage is downloaded.
Analysis
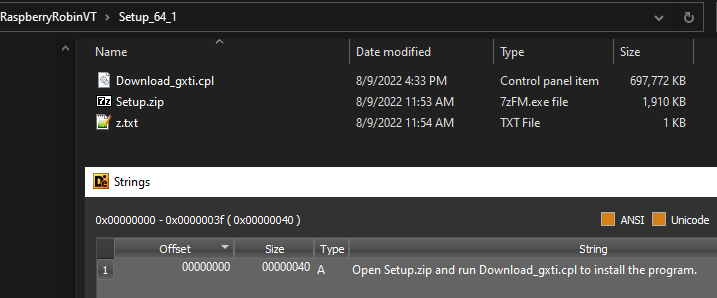
Figure 1: First stage that creates a .LNK file on any attached USB
The first item to note is the size of the dropper: a 700mb file once unpacked. Most of this is garbage data located within the final section (Figure 2). The massively inflated size is an attempt to bypass scanning by some AV/EDR products, as well as prevent it from being uploaded to public sandboxes.
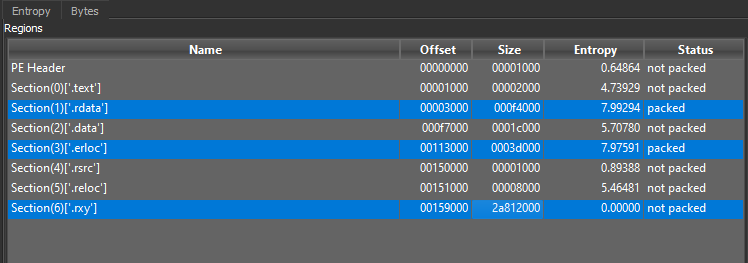 Figure 2: Note the bottom section ‘.rxy’ has a massive size; it is nothing but the character ‘[‘ repeated
Figure 2: Note the bottom section ‘.rxy’ has a massive size; it is nothing but the character ‘[‘ repeated
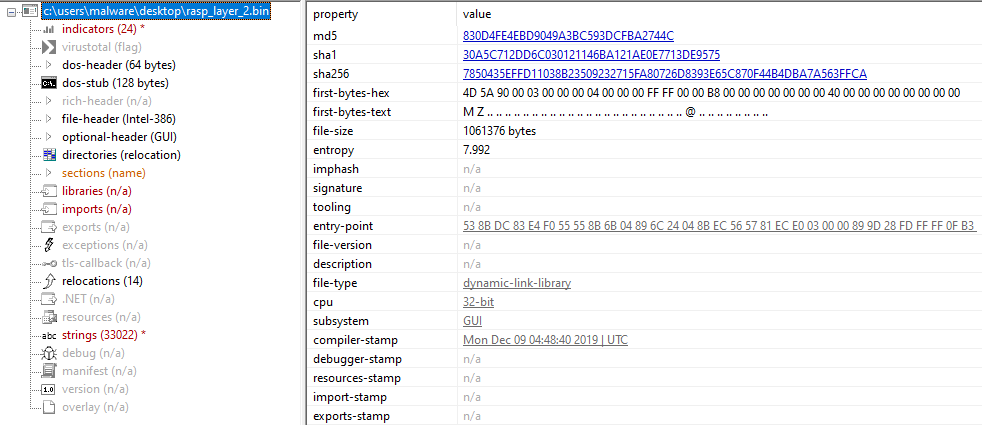
Figure 3: PeStudio results of the secondary layer showing no libraries, imports, exports
Both the dropper and the payload are built with multiple layers of anti-analysis techniques; each is more akin to a virtually-protected machine than an obfuscated file. There are no strings or imports, and thus no API calls to use for context (or use breakpoints with) in a debugger.
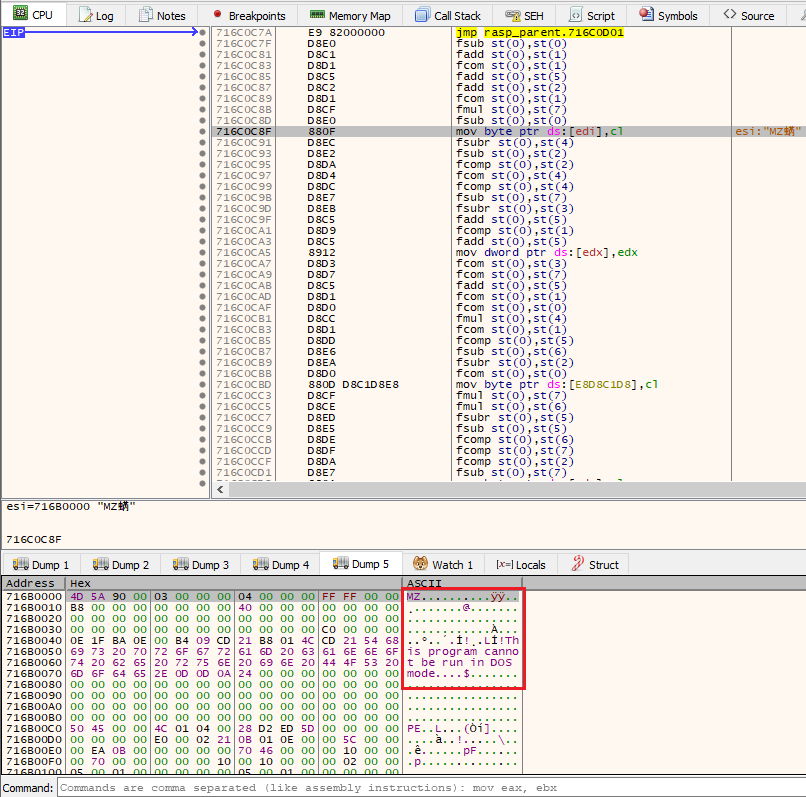 Figure 4: Obfuscation through instruction
Figure 4: Obfuscation through instruction
Every instruction is a series of mathematical actions (add, sub, mul, etc) to change flags, memory offsets, and dynamically call imports. Though no packer is listed with any static analysis tool, this behavior closely resembles how VMProtect works to virtualize runtime and prevent or hinder analysis. Attempting to run the malware in multiple virtual environments failed to produce malicious activity, but several tools were immediately shutdown when loading the sample for analysis. The DLL file will also unload itself when attempting to use a debugger.
This sample is known to drop a fake payload to distract an analyst or AV/EDR tool, located in ‘C:\User\AppData\Local\Temp’. The real payload will use a custom Tor client and reach out to a random hard-coded address for additional payloads or C2 activities. While targets have mostly been government and telecom agencies, there is no reason why other industries couldn’t be affected in the future. Given the sophistication of Raspberry Robin, care should be taken with USB drives and Windows policies on auto-running content.
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV:RaspberryRobin.A (Dropper)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.





