H2 Database JDBC URL Arbitrary Code Execution
Overview:
The H2 console application allows a user to access a SQL database using a browser interface.
H2 is an open source Java SQL database that includes the following technology; JDBC, (Java Database Connectivity) is a Java API that can access any kind of tabular data, especially data stored in a relational database. JDBC helps you to write Java applications that manage some of the activities below:
• Connect to a data source, like a database
• Send queries and update statements to the database
• Retrieve and process the results received from the database in answer to your query
A remote code execution vulnerability has been reported in H2 Database console. This vulnerability is due to improper input validation when handling a specific JDBC URL. A remote, unauthenticated attacker could exploit this vulnerability by sending a crafted request to the target server. Successfully exploiting this vulnerability could result, in the worst case, arbitrary code execution.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2022-23221.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 8.8 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/E:P/RL:O/RC:C).
Base score is 9.8 (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is none.
• Scope is unchanged.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 8.8 (E:P/RL:O/RC:C), based on the following metrics:
• The exploit code maturity level of this vulnerability is proof of concept.
• The remediation level of this vulnerability is official fix.
• The report confidence level of this vulnerability is confirmed.
Technical Overview:
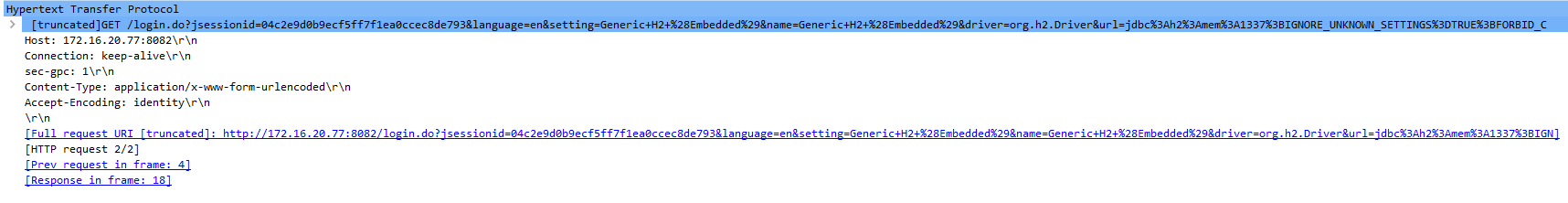
When accessing a JDBC database, the H2 console will ask the user for the location of the database. A user can access an existing database or create a new database if one does not exist and the connection option FORBID_CREATION is not set. The JDBC URL is stored in the variable databaseUrl and is passed into the function getConnection(). The variable databaseUrl is then trimmed of whitespace and is checked if the variable starts with the string “jdbc:h2:”. If so, the current user key, in the variable userKey, is compared to the default key, in the variable key. The variable userKey has a value of null for new users and the variable key has a default value of null for non-privileged connections. Since both keys are the same, the string “;FORBID_CREATION=TRUE” is appended to databaseUrl.
This information is passed into the function JdbcUtils.getConnection() which then calls the function ConnectionInfo(). This function will check the settings in the JDBC URL by calling the function readSettingsFromURL(). This function checks for settings inside of the JDBC URL. An exception will be thrown if any unknown settings exist and the setting IGNORE_UNKNOWN_SETTINGS setting is not set. After checking the JDBC URL, the connection information is eventually passed into the function openSession() through the ConnectionInfo variable, ci. ci is then parsed to find settings inside of the current URL. The settings are stored into the following boolean variables: ifExists, forbidCreation, and ignoreUnknownSetting.
A remote code execution vulnerability exists H2 Database. A remote, unauthenticated attacker could exploit this vulnerability by sending a Database name value with the IGNORE_UNKNOWN_SETTINGS setting set and a backslash at the end of the string. The backslash causes the added semicolon delimiter to be escaped and interpreted as part of the appended FORBID_CREATION option name, causing it to be ignored. Without the FORBID_CREATION option, a new database can created with full administrator privileges. An SQL TRIGGER query can be used to run either JavaScript or Ruby code. Successful exploitation could lead to remote code execution under the security context of the H2 process.
Triggering the Problem:
• The target must be running a vulnerable version of the software.
• The attacker must have network connectivity to the vulnerable server.
• The target must have network connectivity to the attacker controlled server.
Triggering Conditions:
The attacker sends three maliciously crafted requests to the target server. The vulnerability is triggered after the target server receives a malicious .sql file and executes the file’s code.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTP
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 2496 H2 Database JDBC URL RCE
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Applying the vendor-supplied patch to eliminate this vulnerability.
• Filtering traffic based on the signature above.
The vendor has released the following advisory regarding this vulnerability:
Vendor Advisory