Tenda AC1200 Cross-Site Scripting
Tenda products include home networking, business networking, switch, broadband CPE, gateway, powerlines, mobile broadband and IP cameras. Tenda offers AC1200 routers as well. AC means that the router has support for the 802.11ac (or Wi-Fi 5) wireless networking standard, which offers fast WiFi network connections on the 5GHz frequency. The number that comes after AC represents the maximum theoretical bandwidth of the router with 1200 representing 1200 Mbps.
Cross-Site Scripting
Cross-Site Scripting (XSS) attacks are a type of injection attack that occurs when malicious scripts are injected into otherwise benign and trusted websites. An attacker then uses a web application to send malicious code, generally in the form of a browser side script, to the end user.
Reflected XSS attacks abuse the dynamic way websites interact with browsers. These attacks make it possible , for an attacker, to control the victim’s browser and their interaction with a given vulnerable website. Injection attacks display back content provided or controlled by a user, like an URL parameter or an input field. This opens the door to manipulation of the content.
Stored XSS occurs when the injected script is permanently stored on the target servers via a database, message forum, visitor log, comment field, etc. The victim then retrieves the malicious script from the server when it requests the stored information.
Tenda Cross-Site Scripting Vulnerability | CVE-2022-40846
Tenda is vulnerable to both Reflected and Stored XSS attacks.
The Tenda AC1200 router does not perform proper validation of user-supplied input and is vulnerable to cross-site scripting attacks via the homepage’s connected application hostname field. This vulnerability exists in the remote web management console.
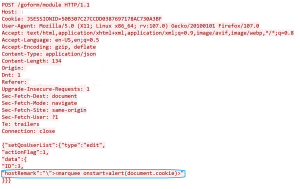
As seen above the XSS successfully triggers and returns information about session cookies.
Tenda is also vulnerable to stored XSS in the website filtering functionality (CVE-2022-40844). The URL management panel of the website filtering accepts and stores any input without proper validation. Anything injected within the URL body is stored and will be reflected back once its associated group name is clicked in the panel.
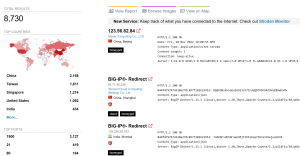
Quick check on Shodan reveals vulnerable devices:
SonicWall Capture Labs provides protection against this threat via following signatures:
- IPS 18814: Tenda AC1200 Cross-Site Scripting




