Vacron Network Video Recorder Remote Command Execution
SonicWall Capture Labs threat research team observed attacks exploiting old vulnerability in Vacron NVR.
Network video recorders (NVRs) are IP-based appliances that are built for managing cameras, recording and viewing camera feeds at a site. NVRs are usually PC-grade or low-end server systems made using commercial off-the-shelf (COTS) hardware components. They typically contain an embedded operating system or a client operating system that hosts video management software, which provides users a mechanism to view, record and manage camera feeds. Vacron sells NVRs as well as other products.
Vacron NVR Remote Command Execution Vulnerability
The goal of command injection attack is the execution of arbitrary commands on the host operating system via a vulnerable application. Command injection attacks are possible when an application passes unsafe user-supplied data (forms, cookies, HTTP headers etc.) to a system shell. In this attack, the attacker-supplied operating system commands are usually executed with the privileges of the vulnerable application.
The remote Vacron network video recorder is affected by a remote command execution vulnerability due to improper sanitization of user-supplied input passed via /board.cgi.
Following are some of the exploits found in the wild:

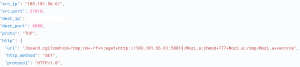


As one can see the vulnerable /board.cgi cannot properly sanitize the input. This allows the attacker to inject and execute the commands to change the directory and download malicious script from the attacker-controlled server.
SonicWall Capture Labs provides protection against this threat via following signatures:
-
-
- IPS 13033:Vacron NVR Remote Command Execution
- GAV: Linux.Mirai.N_2
-
IoCs
-
- 222.138.188.211
- 103.181.56.61
- 125.44.20.51
- 175.107.0.212
- 3a43d007ed5ff84d4b71f96a49c88fe0061a2a9651935a82d4acbf55982fc370
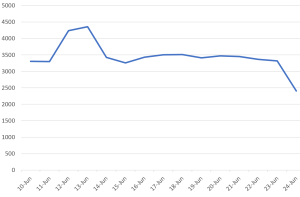
Threat Graph