"TargetCompany" ransomware directed at Carone & Company Inc.
The Sonicwall CaptureLabs threat research team has observed reports of ransomware which, in the Antivirus community, goes by the name TargetCompany. The malware surfaced in June 2021. The current variant that we have obtained is aimed at infecting a construction management company called Carone & Company. Ransom payment and negotiation is initiated via a tOr site that is run by the attackers.
Infection Cycle:
Upon execution, files on the system are encrypted. Each encrypted file is given a “.carone” file extension.
The following commandline prompt appears during the file encryption process:
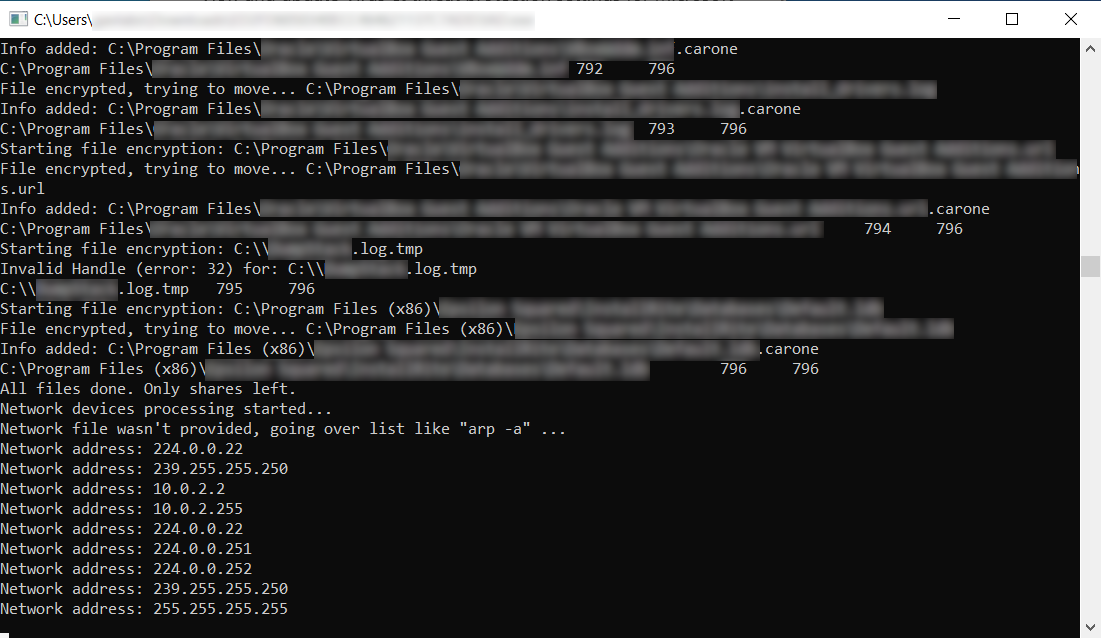
A file named “How to decrypt files.txt” is dropped into each directory containing encrypted files.
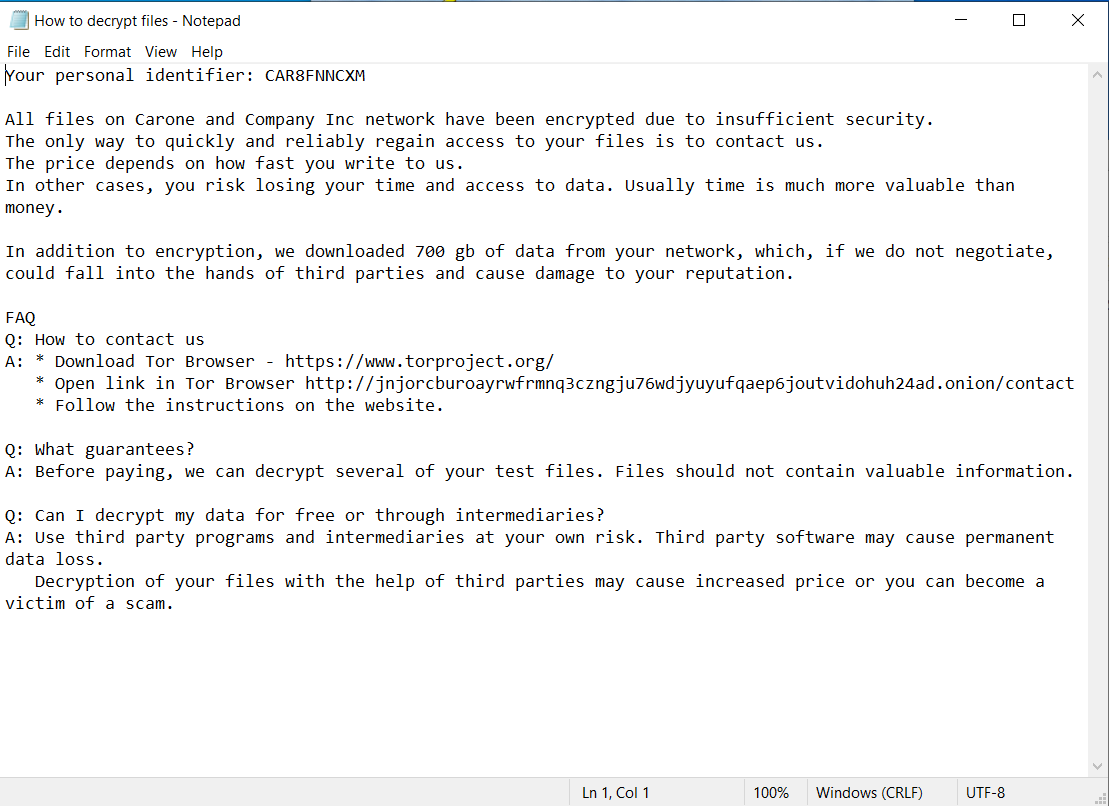
“How to decrypt files.txt” contains the following message:
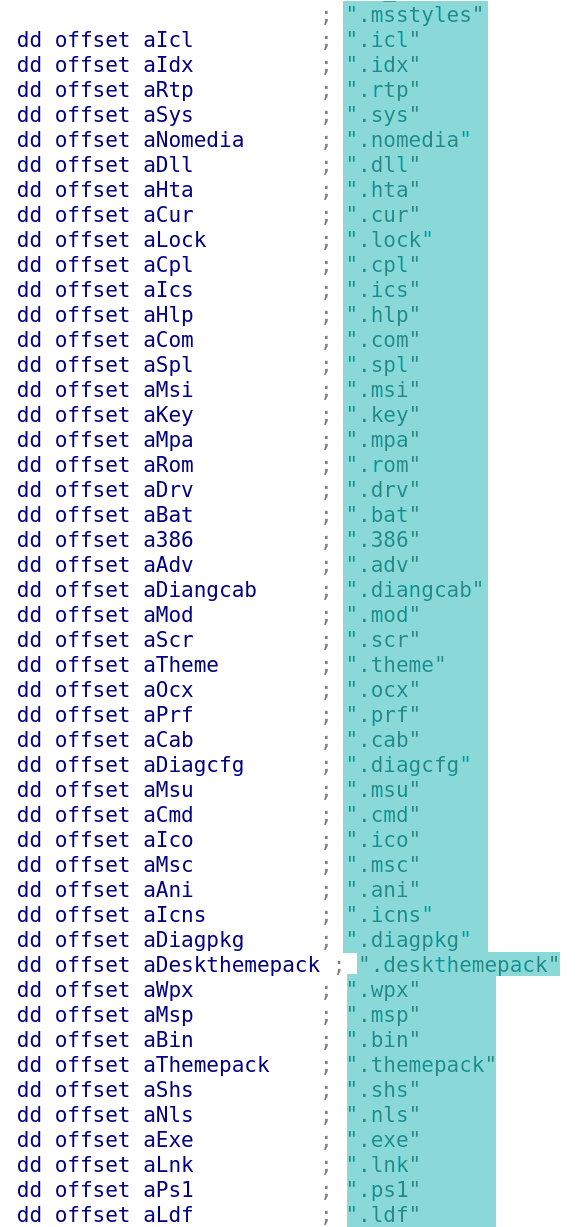
The malware executable is not packed. It is written in C and is easy to decompile. Decompilation reveals that the following file types are targeted for encryption:
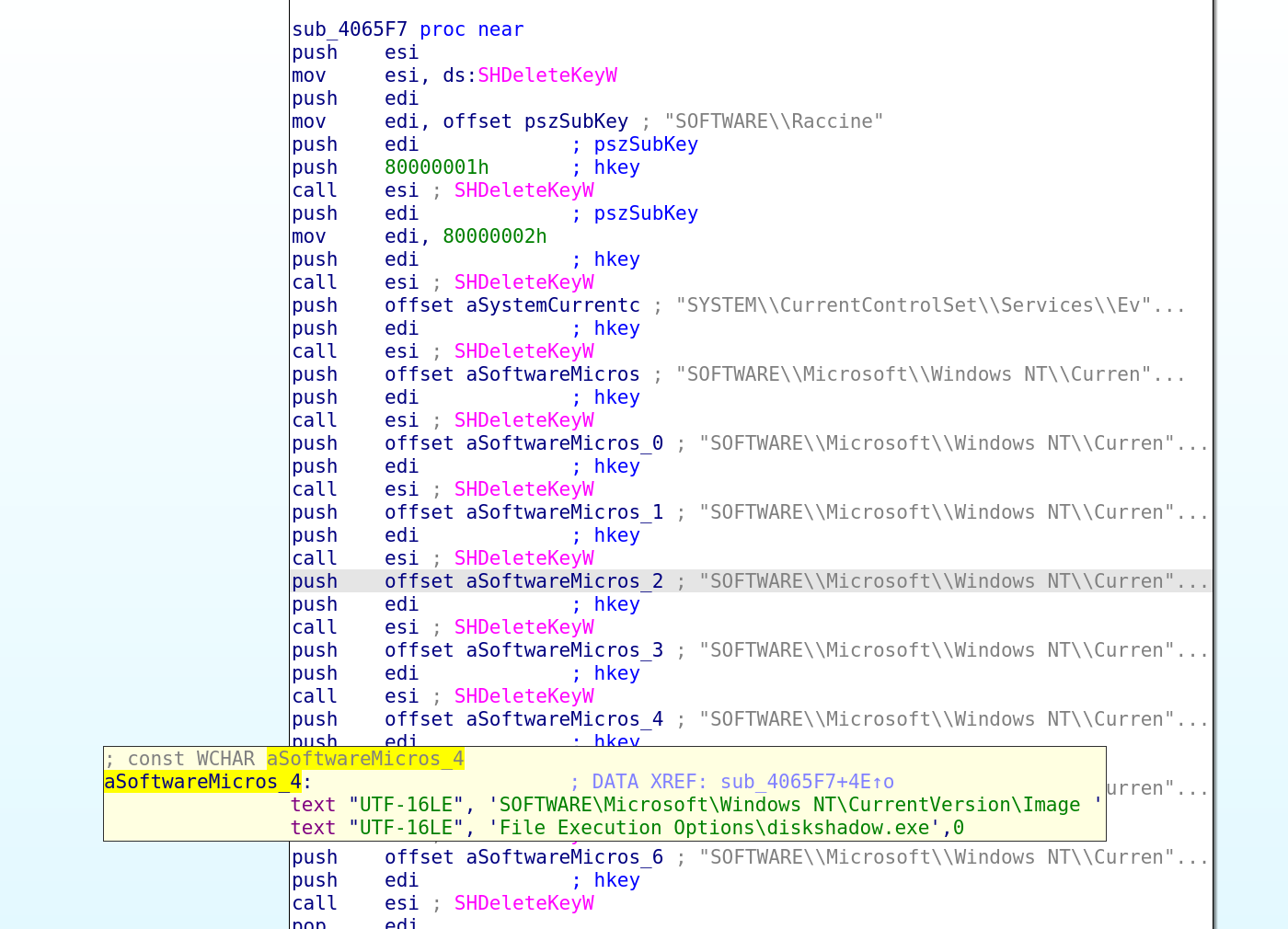
The following registry entries are deleted if they are present:
After encryption of files in the local file system, files on any attached storage shares are targeted:
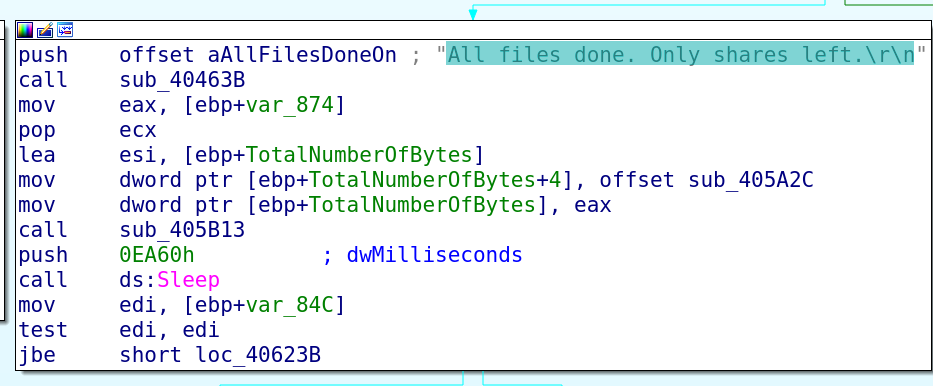
The tOr link from the ransom message leads to the following page:
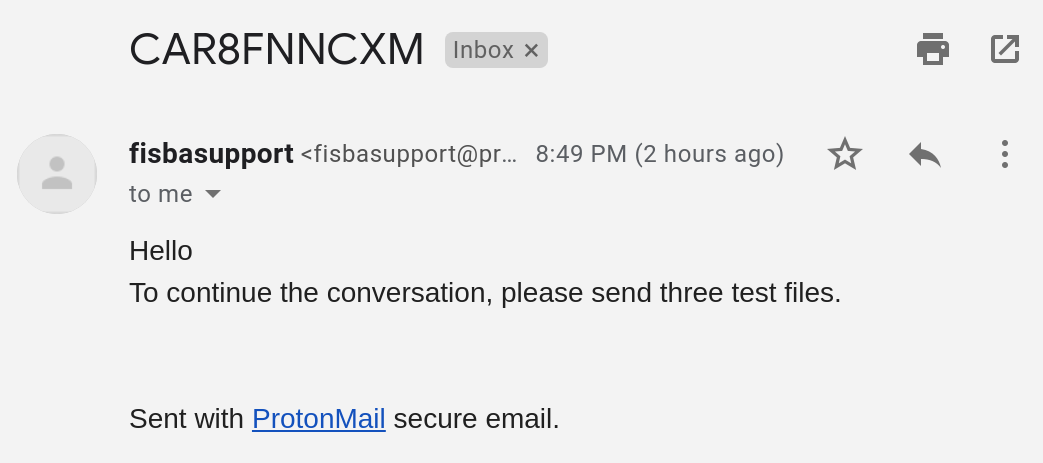
After filling out the form with the ID and email address, we were contacted via email:
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: TargetCompany.RSM (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.




