Fake Covid-19 vaccine-related information found spreading malware
As Covid-19 vaccinations happen across the country, cybercriminals are riding the wave again using social engineering tactics purporting to be vaccine-related information to spread malware and steal user information. The Sonicwall Capture Labs Research team has analyzed a malicious PDF befittingly named “Adenovirus vector.pdf” which pertains to one of the viral vectors used in some late-stage COVID-19 vaccine trials according to the CDC website.
Infection Cycle:
The files comes as a PDF possibly via spam as an email attachment using the following filename:
- Adenovirus vector.pdf
Once executed, the victim is presented with a fake “I’m not a Robot” Captcha which when clicked will redirect to a malicious website.
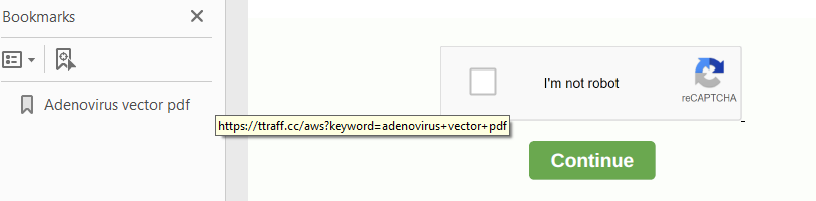
One redirect leads to seemingly unending redirects to a slew of ad websites.
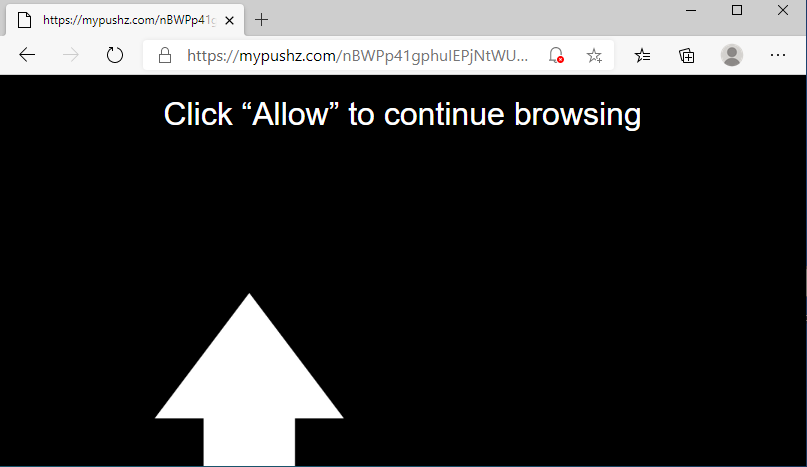
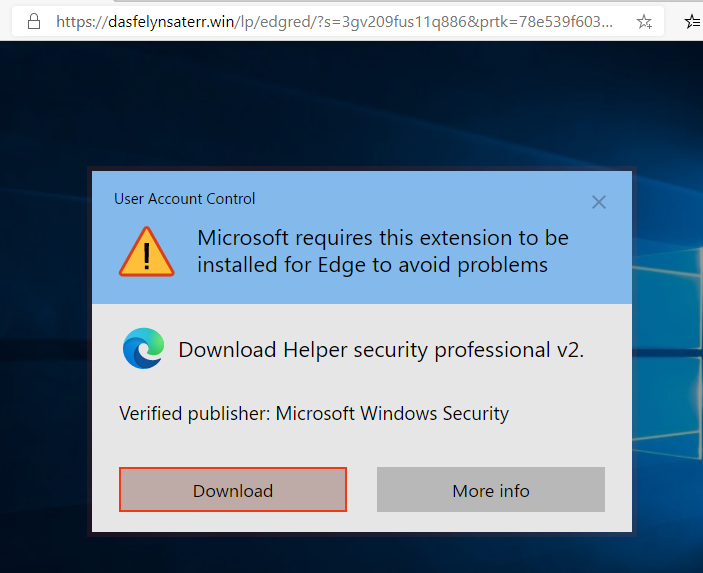
To then asking the victim to download a malicious software called “Security Helper” extension.
And scare the user to thinking that his system is infected by displaying fake scan results which purports to be from some well-known Antivirus vendors like McAfee and Norton with links on how to “fix” the problem and purchase protection which leads to another dubious website.
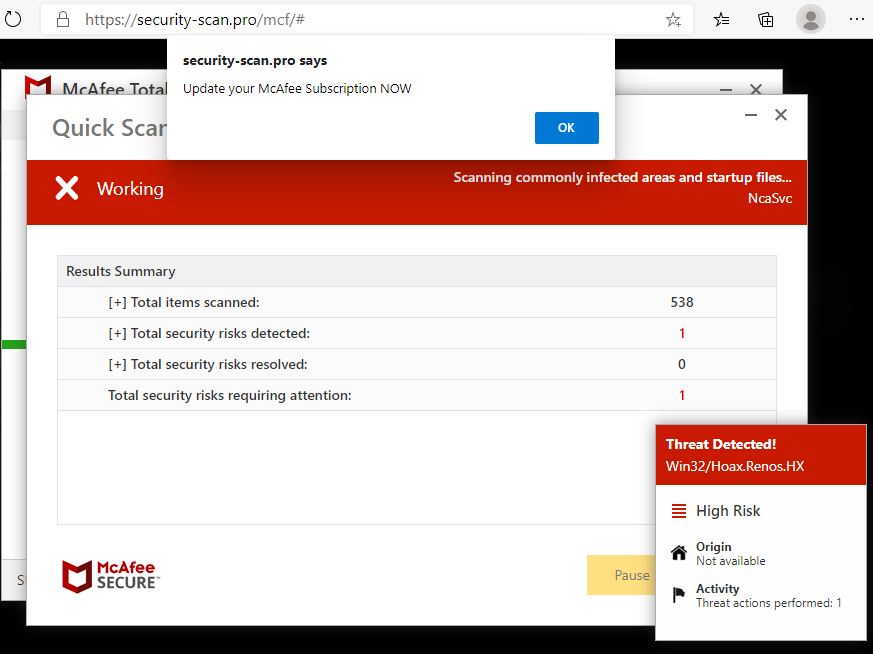
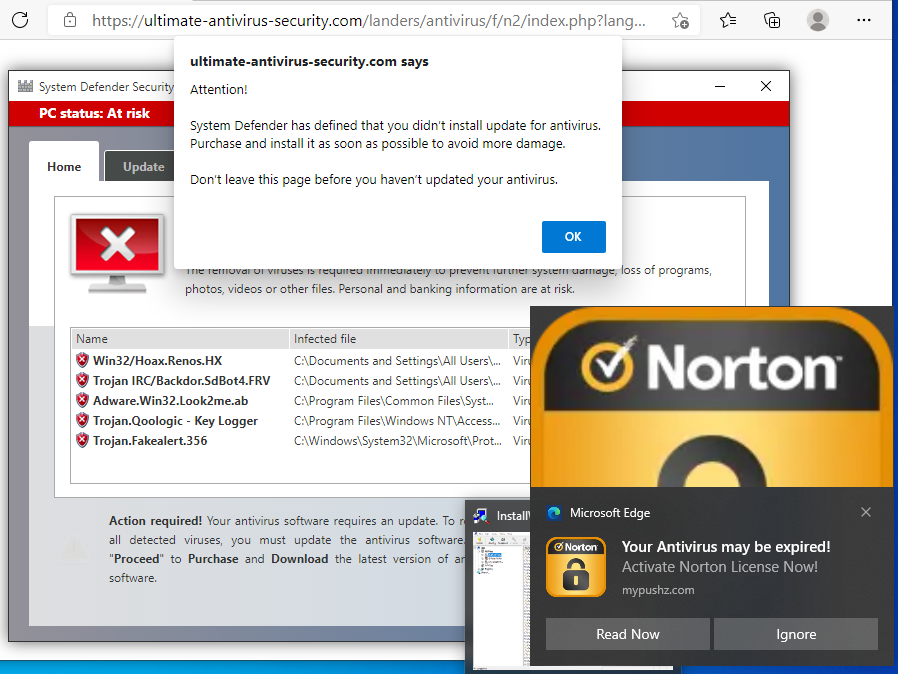
These fake security pop ups will not stop because malicious websites were added in the browser’s “allow” list which allows it to send these notifications.
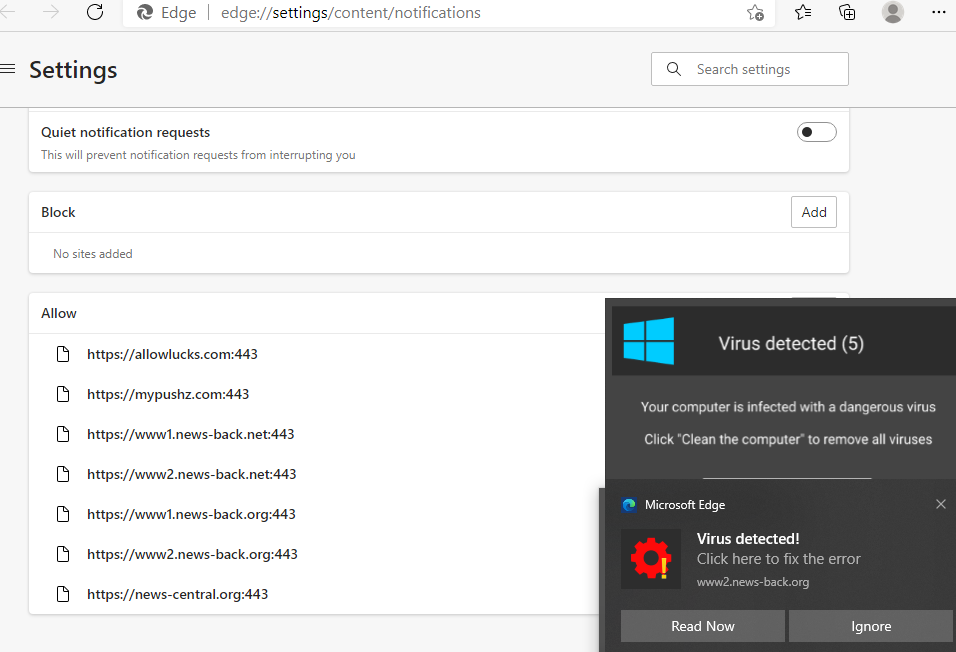
It comes as no surprise that cybercriminals take advantage of current events such as the pandemic and the vaccine rollout to spread malware. Therefore we urge our users to only get vaccine-related information and services from trusted websites or sources and to exercise caution when downloading software from unfamiliar websites.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Malagent.N_107 (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.





