Modular Emotet Variant
Overview:
SonicWall Capture Labs Threat Research Team recently found a new sample and activity for Emotet. Emotet is an advanced, self-propagating modular malware. Historically, Emotet was a advanced banking malware with botnet capabilities and indicators. Emotet has a variety of install sequences for many different content delivery mechanisms. Mostly Emotet is spread through phishing spam emails containing attachments. The command and control, payloads, and delivery solutions change over time. Emotet first emerged in June of 2014.
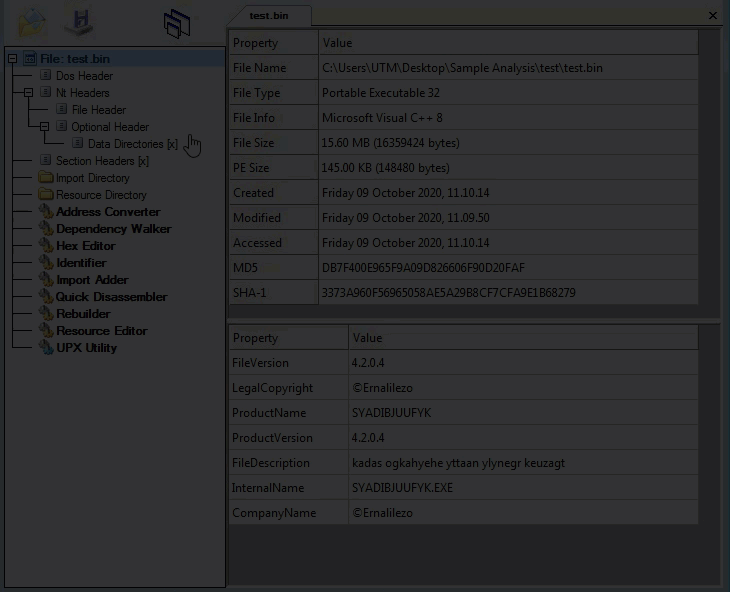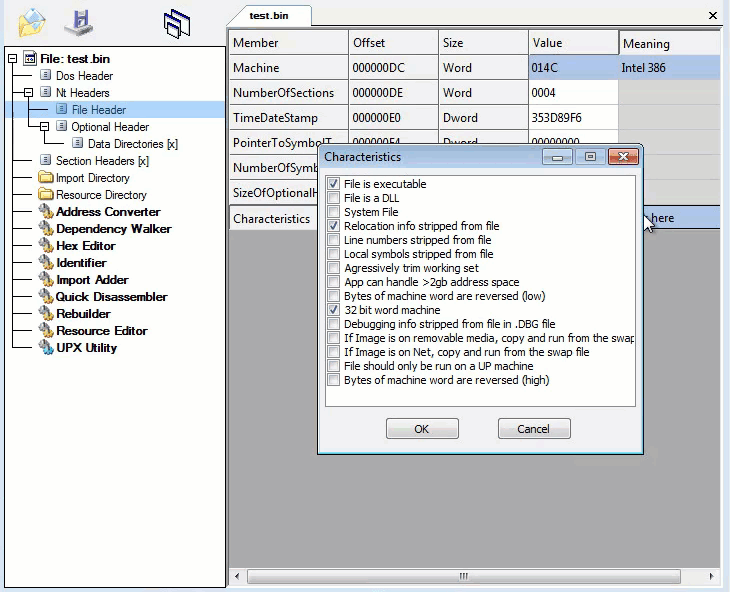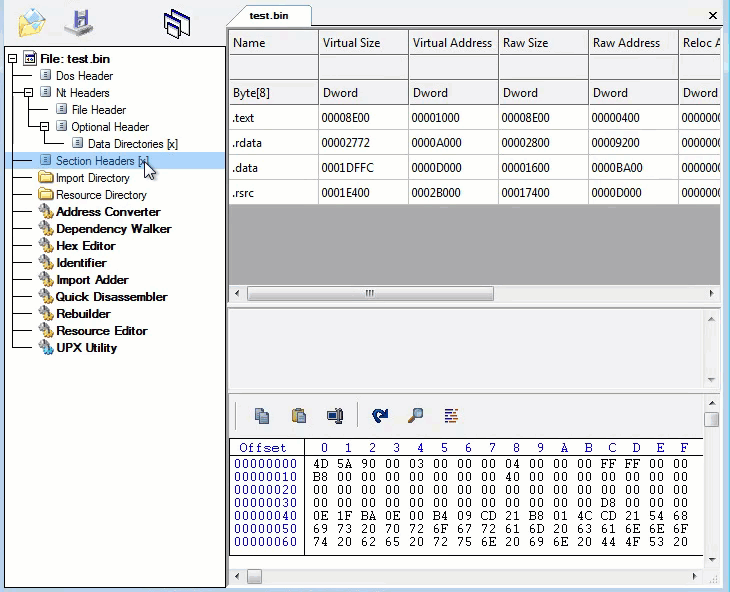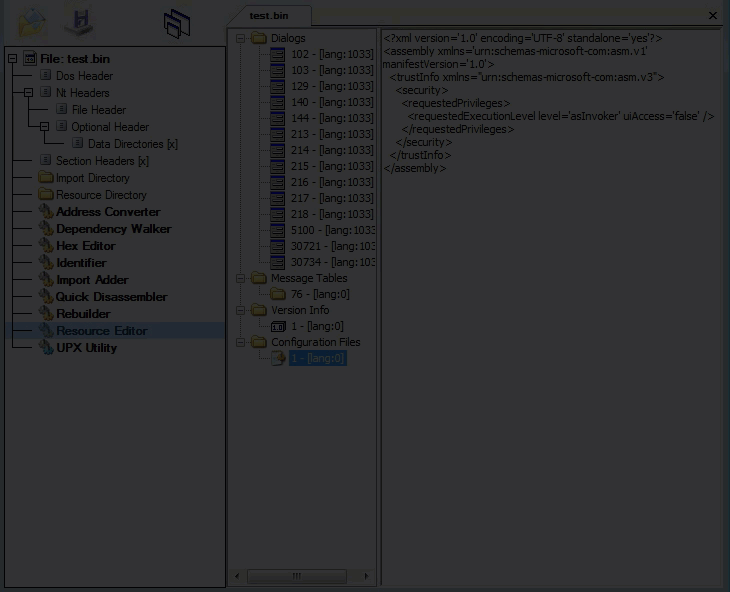
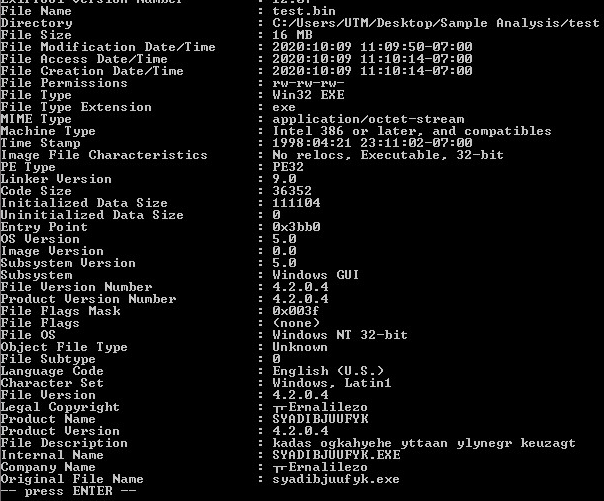
Sample, Static Information:
Checking for valid values within the PE File:
Command-line Static Information:
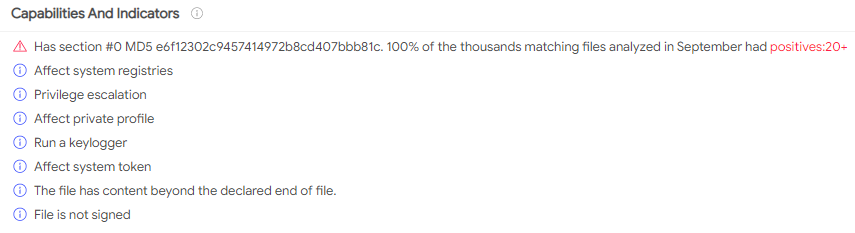
Capabilities, Privilege Escalation and Keylogging stand out here:
Dynamic Information:
WinMain:
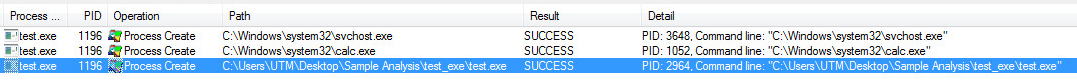
Processes Created, Svchost, Calc, MSpaint, and itself twice:
Pipes are used to transfer data:
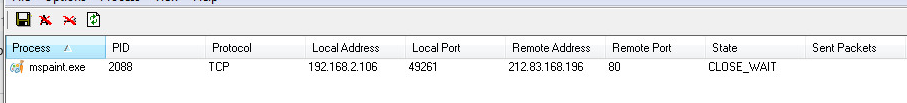
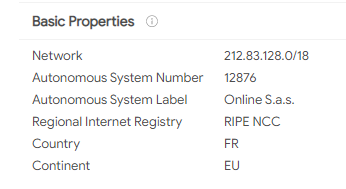
Network Artifacts:
Graph:
Supported Systems:
- Windows 10
- Windows 8.1
- Windows 8.0
- Windows 7
- Windows Vista
SonicWall, (GAV) Gateway Anti-Virus, provides protection against this threat:
- GAV: Emotet.N (Trojan)
Appendix:
Sample SHA256 Hash: 5c5267ba9105ed1ebd26d50db8886030a601ffcda46fdbedf85b9a0bdc46e431