Anubis infostealer wants your cryptocurrency wallet
This week the Sonicwall Capture Labs research team analyzed an infostealing Trojan that is a mash up of another infostealer Trojan and a ransomware. This Trojan, is called Anubis but borrowed most of its code from another Trojan named Loki which is popularly sold in the underground market.
Infection Cycle
This Trojan uses the following icon:
![]()
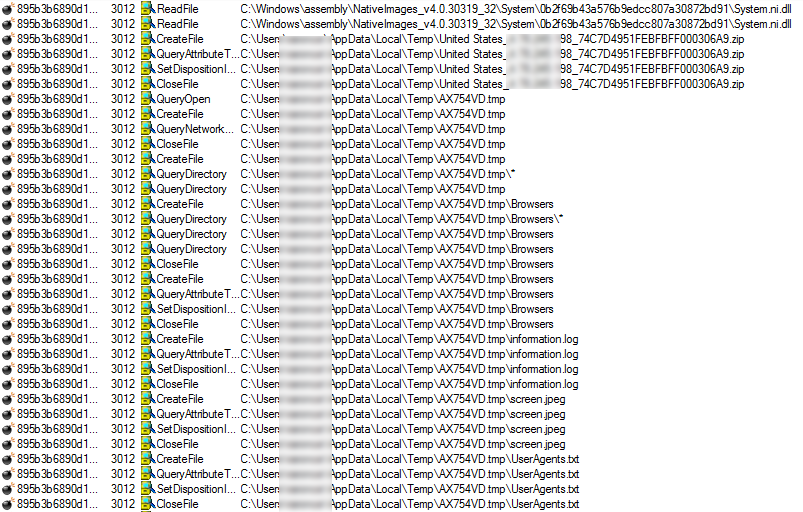
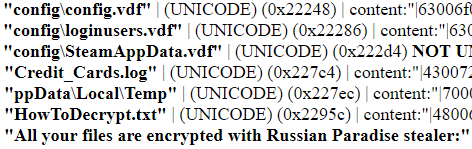
Upon execution, it proceeds with perusing through the system and start stealing data, taking screenshots, etc. It then creates a random folder within the %temp% directory where it stores log files of stolen data.
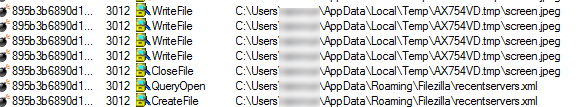
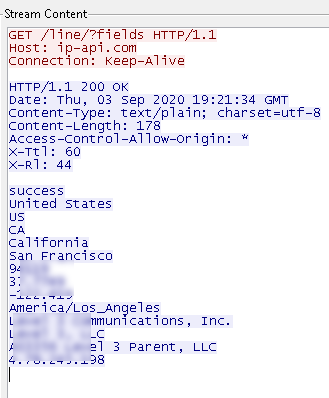
This stolen data is then sent to a remote server.
During static analysis, it was noted that it had references to “Loki” within its strings as evidence of it borrowing code from this other infostealer Trojan. After all, Loki is a commodity malware commonly sold in underground sites.
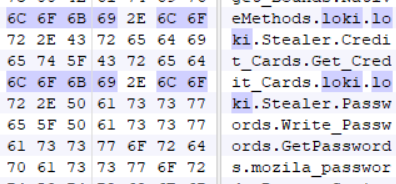
This Trojan functions much like Loki and comes after the victim’s system information, browser data, credentials, credit card details and cryptocurrency wallets.

Coincidentally, during analysis we noticed references to ransomware functionality within its strings although this was not evident during runtime.
Apart from being sold underground, Lokibot has been known to be distributed via spam emails and Anubis, will highly be likely to be similarly distributed.
Always be vigilant and cautious when installing software programs particularly if you are not certain of the source.
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: Anubis.ST (Trojan)
- GAV: VHDLocker.RSM (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.