Fake Aarogya Setu Android apps harbor spyware capabilities
A number of countries have taken the initiative of developing Covid-19 tracking apps over the last few months. Aarogya Setu is the Indian COVID-19 tracking mobile application. This app crossed five million downloads within the first three days from its launch making it widely popular in India. This popularity makes it a target for malware creators.
SonicWall Capture Labs threats research team observed fake Aarogya Setu apps containing spyware components in the wild. Here are few highlights from our findings:
CASE I
- Md5: e5e44ac40123023eebd5caf9662f05d1, bfa19e91bb4b25d34ac10ad7b9fc5df2
- App Name: Aarogya Setu
- Package Name: cmf0.c3b5bm90zq.patch
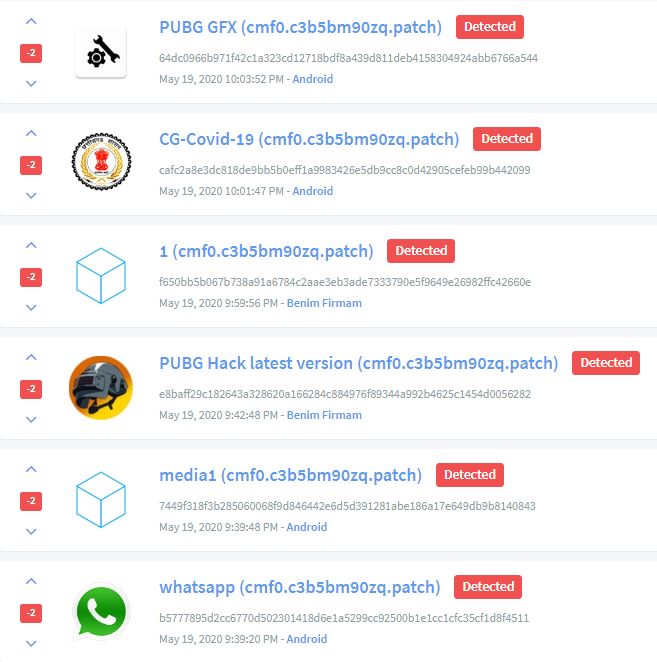
There are a number of fake apps that have the package name – cmf0.c3b5bm90zq.patch:
The malware author uses the same code for a majority of these apps and spreads them by re-branding the icon and application name. In this case this app masquerades the legitimate Aarogya Setu app, however the copy is not perfect. The icon appears stretched and can be identified when kept side-by-side with the legitimate app:
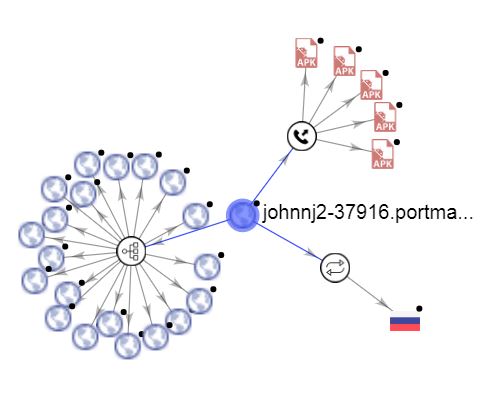
Upon execution we do not see any activity on the screen, after some time the app icon disappears from the app drawer. The contains reference to a domain – johnnj2-37916.portmap.io – in the patch_preferences.xml file. During our analysis the malware did not try to communicate with this domain, however this domain is connected to malicious apps:
CASE II
- Md5: bbe84ba545d652d9e06635a6e89d48b5
- App Name: Aarogya Setu – AddOn
- Package Name: yps.eton.application
Similar to Case I, there are a number of fake apps with the package name yps.eton.application:
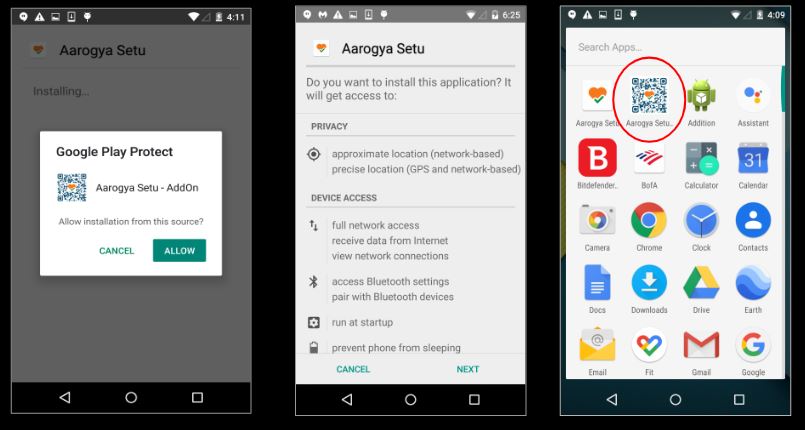
This app masquerades itself as an Aarogya Setu Add-on app, even though there is no such official app. Upon installation and execution, this app requests for Device-Admin privileges and requests the victim to allow installation from this source. It installs the legitimate Aarogya Setu app from its resources folder (MD5: 4181352b37cd4ee809fa83390d3cc228 ) and thereby tries to appear less suspicious to the user.
CASE III
- Md5: df5698d5aef850b217cbbfa9789bd347
- App Name: Aarogya Setu
- Package Name: com.android.tester
The malware writers have accurately copied the legitimate Aarogya Setu icon in this case. Installing the malicious and legitimate Aarogya Setu app and identifying the malicious app by looking at the icons is difficult:
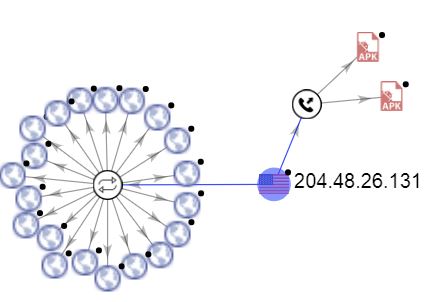
We did not see network activity during our analysis session but there was a record of a domain – 204.48.26.131:29491 – within an xml file belonging to the app. This domain is connected with another malicious Android app:
Common Goals
All the three apps mentioned above contain spyware capabilities. Each app contains code that has similarity with the Android spyware SpyNote. We have blogged about SpyNote malware masquerading legitimate apps in the past. A recap of the capabilities of this spyware:
- Make phone calls
- Record audio
- Send SMS
- Take photos from the camera
- Record videos from the camera
- Record keystrokes (keylogger)
- Check if the device is rooted
- Start the spyware each time the device reboots
Deception
A common trend observed in some of these malicious apps is that the legitimate Aarogya Setu app is piggybacked in the resources folder as google.apk (MD5 – 4181352b37cd4ee809fa83390d3cc228).
Some of these malicious apps install the legitimate app in the background, this technique is used to fool the user into believing that the user installed the legitimate app. But in reality the malicious app executes its nefarious functions in the background.
If the user deletes Aarogya Setu app from the device by long pressing the icon > uninstall method, only the legitimate app is removed and the malicious app would still be present on the device. The only way to remove the malicious app is to remove it from settings > apps > uninstall. This trick has the potential to fool a number of users who are not vigilant.
SonicWall Capture Labs provides protection against this threat with the following signatures:
- AndroidOS.SpyNote.GN
- AndroidOS.SpyNote.SP
- AndroidOS.SpyNote.SC