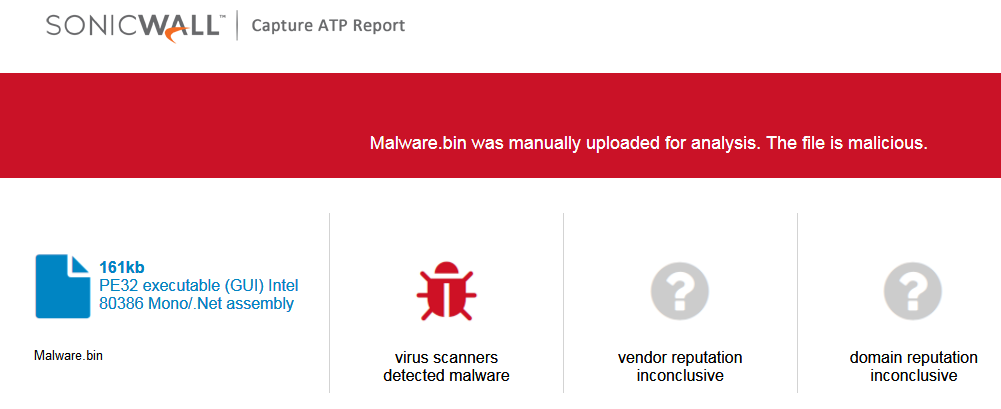
PROJECT23 Ransomware actively spreading in the wild.
The SonicWall Capture Labs threat research team observed reports of a new variant family of PROJECT23 ransomware [PROJECT23.RSM] actively spreading in the wild.

The PROJECT23 ransomware encrypts the victim’s files with a strong encryption algorithm until the victim pays a fee to get them back.
Infection Cycle:
The ransomware adds the following files to the system:
- Malware.exe
- % App.path%\ VLCKFNVA-README.TXT
- Instruction for recovery
- %App.path%\ [Name]. <Random>
- % App.path%\ VLCKFNVA-README.TXT
Once the computer is compromised, the ransomware runs the following commands:
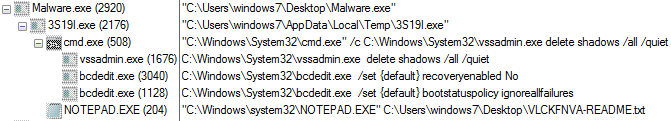
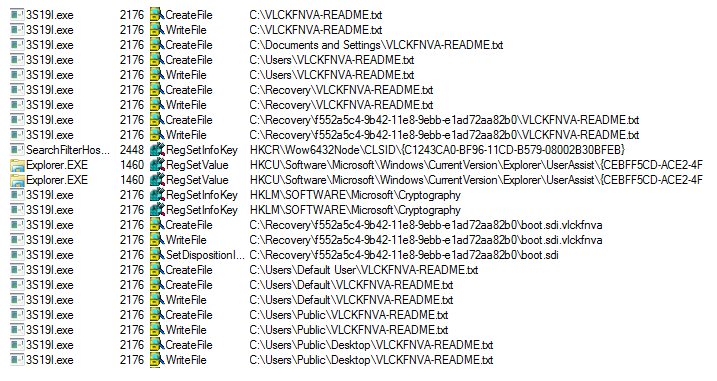
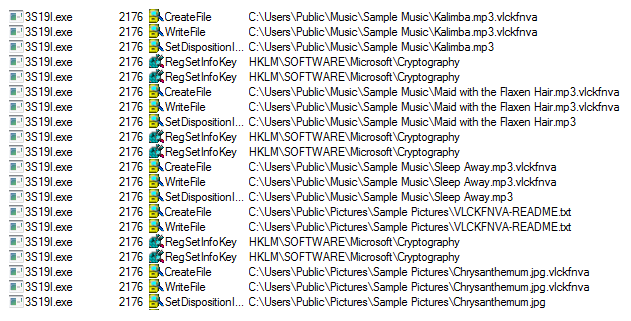
The ransomware encrypts all the files and appends the [Random] extension onto each encrypted file’s filename.
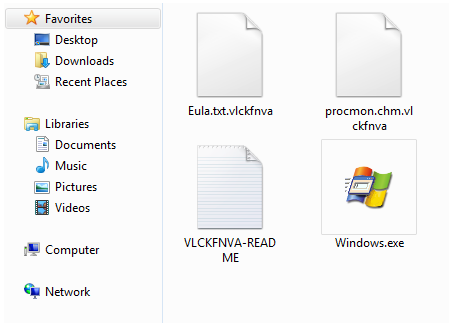
After encrypting all personal documents, the ransomware shows the following text file containing a message reporting that the computer has been encrypted and to contact its developer for unlock instructions.

SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: PROJECT23.RSM (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.