Rekensom Ransomware actively spreading in the wild
SonicWall Capture Labs Threat Research Team recently found a new RekenSom Ransomware.
Injection Cycle.
At the onset of execution, a named mutex “Rekensom” is created to ensure only one instance of the sample is running.
To get the most CPU cycles, it sets thread priority to highest.
Adding an entry to the “RunOnce” in the Registry or startup folder will cause the program referenced to be executed when a user logs in.
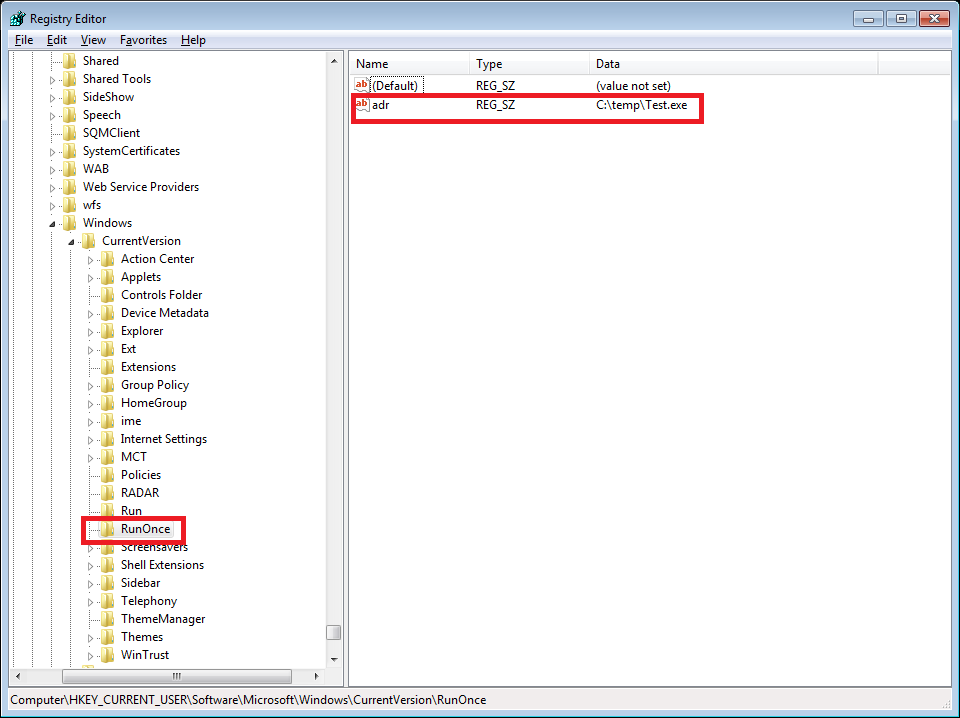
This particular variant targets logged-in user’s Desktop folder. Files with specific file extensions from the Desktop folder are chosen for encryption.

It uses symmetric encryption algorithm AES for encrypting the target files. Plaintext buffer is populated first with the file’s content followed by the name of the file which is being encrypted
Infected files are later renamed to “Encrypted{variable}.som”. The variable component only contains ‘-‘ character and the length could vary from 6 to 12 characters.
Because of this code flaw, only ‘6’ files could be recovered as other files would be overwritten.
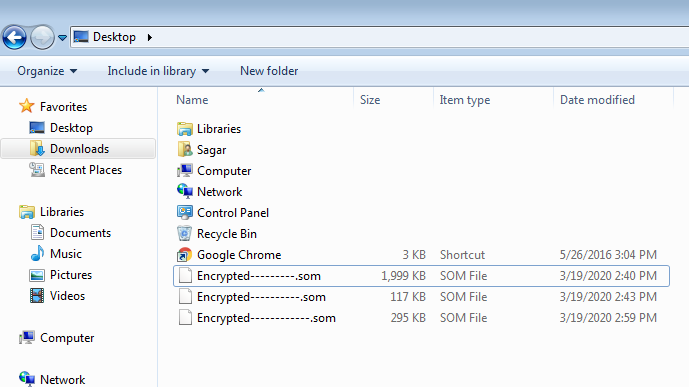
Waiting time of 500 ms has been added before the next file is targeted, this could help evade some behavioral detection technologies.
And once all the file are encrypted it displays the below note.

Some part of the code has been used from the OpenSource Ghack ransomware project, which is still available on GitHub.
SonicWall Capture Labs provides protection against this threat via the following signature:
GAV: MalAgent.H_16015 (Trojan)
This threat is also detected by SonicWALL Capture ATP.




