New version of Cryakl Ransomware demands $10k for file decryption
The Sonicwall CaptureLabs Threats Research team have observed a newly released version of Cryakl ransomware. First seen in early 2014 spreading via email, Cryakl works like most ransomware by encrypting files and demanding a ransom for file retrieval. However, the malware requires the victim to contact its operators via email in order to find out the ransom amount to be paid. Using this method, there is also the opportunity to upload test files for decryption verification and, in some cases even negotiate the price for file restoration.
Infection Cycle:
Upon execution, the malware copies itself to %AppData%\Local\Temp\svclaa and attempts to execute itself again. It causes presentation of the following User Account Control prompt:
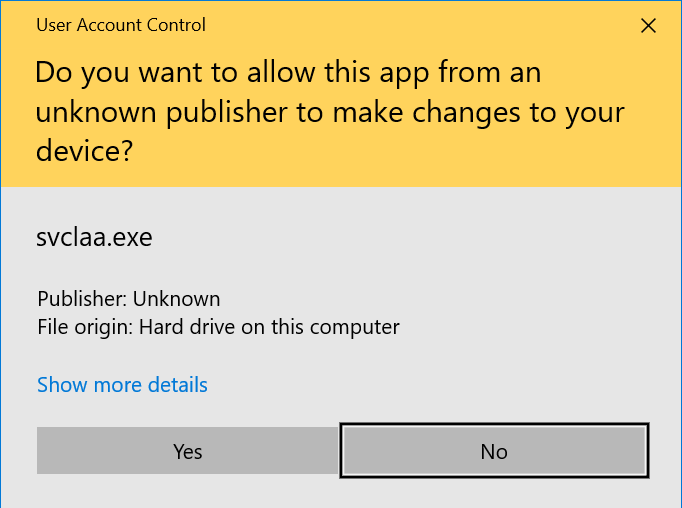
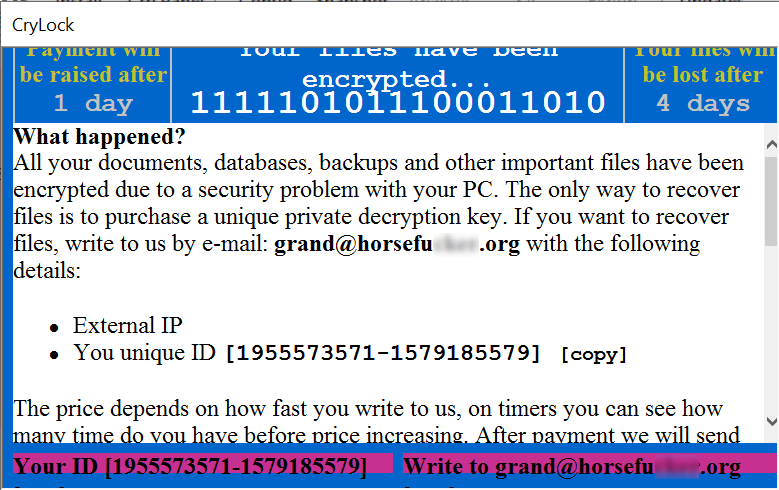
The malware proceeds to encrypt files on the system. Once this is complete, the following dialog is shown:
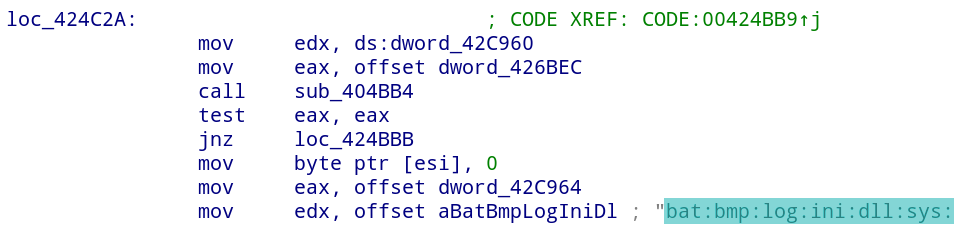
Encryption of files with the following extensions are ignored: bat, bmp, log, ini, dll, sys
The malware drops the following files onto the system:
- %AppData%\Local\Temp\svclaa.exe (copy of original) [Detected by: GAV: Cryakl.RSM (Trojan)]
- how_to_decrypt.hta (to every directory containing encrypted files)
The malware writes the following keys to the registry:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run 1955573571 “%AppData%\Local\Temp\svclaa.exe”
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run 1955573571hta “%AppData%\Local\Temp\how_to_decrypt.hta”
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run 882149 “882149”
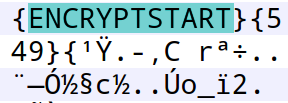
Encrypted files are given the following infection markers:

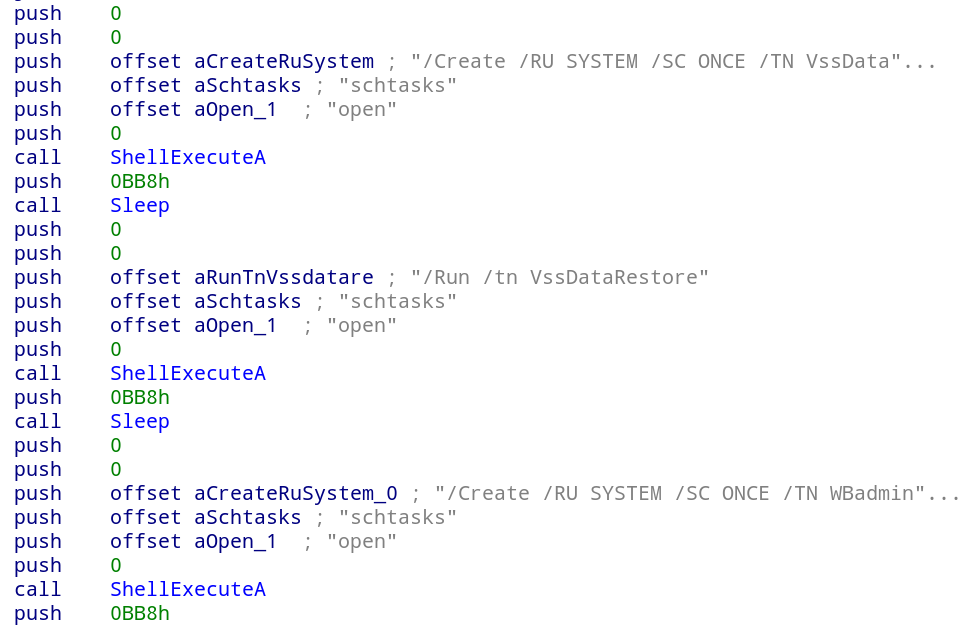
The following commands are executed in order to delete system backups and shadow copies:
/Create /RU SYSTEM /SC ONCE /TN VssDataRestore /F /RL HIGHEST /TR "vssadmin delete shadows /all /quiet" /st 00:00
/Run /tn VssDataRestore
/Create /RU SYSTEM /SC ONCE /TN WBadminSystemRestore /F /RL HIGHEST /TR "wbadmin DELETE SYSTEMSTATEBACKUP -keepVersions:0" /st 00:00
/Run /tn WBadminSystemRestore
/Create /RU SYSTEM /SC ONCE /TN WBadminBackupRestore /F /RL HIGHEST /TR "wbadmin DELETE BACKUP -keepVersions:0" /st 00:00
/Run /tn WBadminBackupRestore
/Create /RU SYSTEM /SC ONCE /TN WMICRestore /F /RL HIGHEST /TR "wmic SHADOWCOPY DELETE" /st 00:00
/Run /tn WMICRestore
/Create /RU SYSTEM /SC ONCE /TN BCRecover /F /RL HIGHEST /TR "bcdedit /set {default} recoveryenabled No" /st 00:00
/Run /tn BCRecover
/Create /RU SYSTEM /SC ONCE /TN BCBoot /F /RL HIGHEST /TR "bcdedit /set {default} bootstatuspolicy ignoreallfailures" /st 00:00
/Run /tn BCBoot
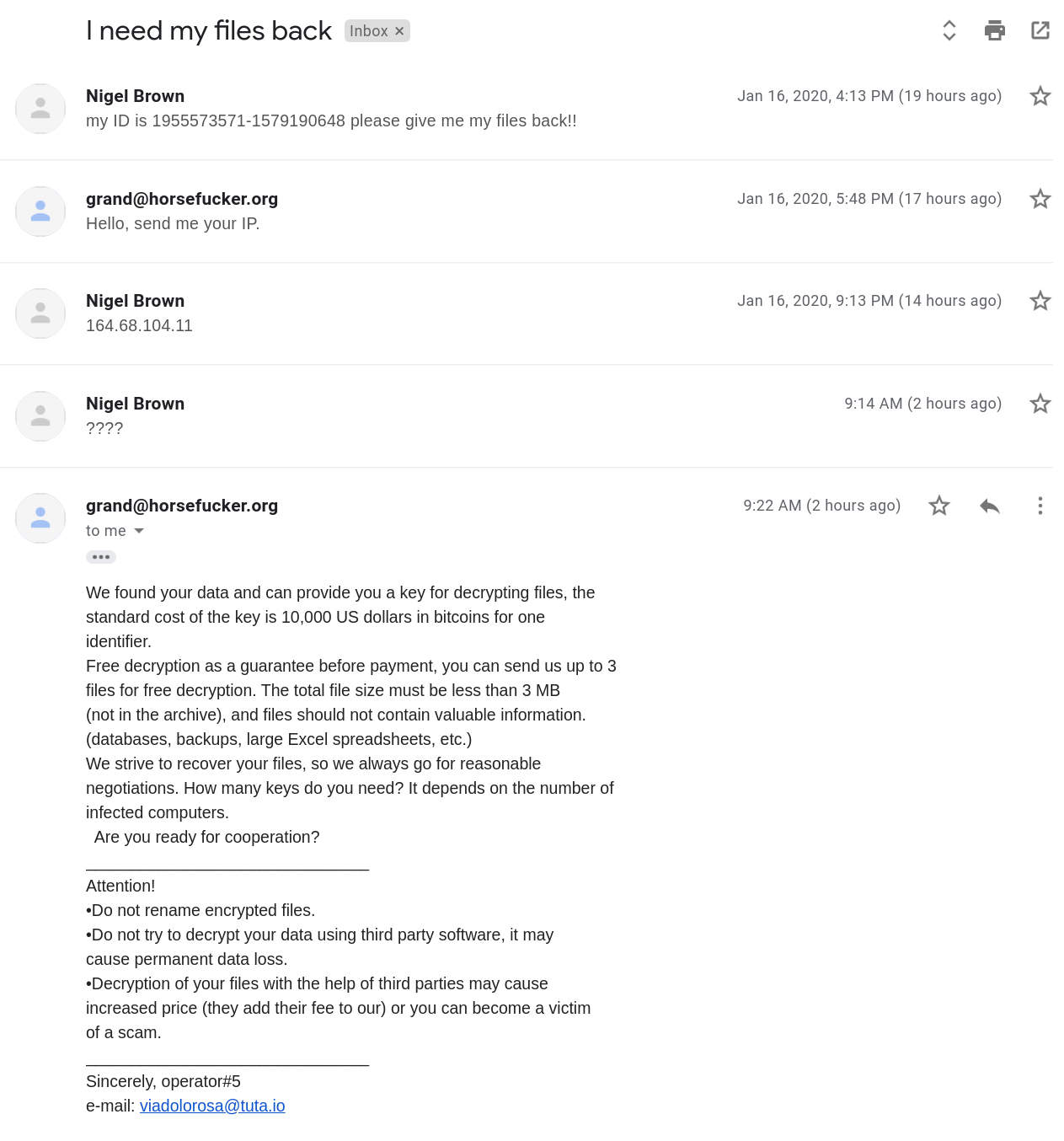
There is no ransom payment method mentioned in the message dialog shown when the malware is run. Instead, the victim is directed to communicate via email in order to find out how to restore encrypted files. We had the following conversation via email with the operator who revealed that the cost for file restoration is $10,000 USD in bitcoin:
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: Cryakl.RSM (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.



