Fake windows update serves a fake Windows Media Player with a side of cryptominer
This week, the SonicWall Capture Labs Threat Research Team came across another cryptominer that pretends to be a media player and even loads a wav file to hide its real intent.
Infection Cycle:
This Trojan comes in an archive file that purports to be a Windows Update component. Within the archive file are the following files:
- mstcss.exe
- config.json
- song.wav
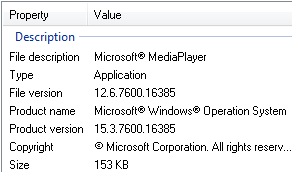
The executable file mstcss.exe uses the following file properties pretending to be Windows Media Player.
Upon execution it loads the wav file which plays an instrumental music.
Then it reads the config.json file which has the settings for mining cryptocurrency.
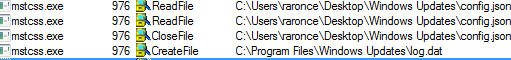

It creates a log file in the following directory:
- \Program Files\Windows Update\log.dat
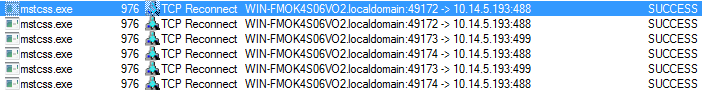
The Trojan then proceeds to connect to the mining server.
![]()
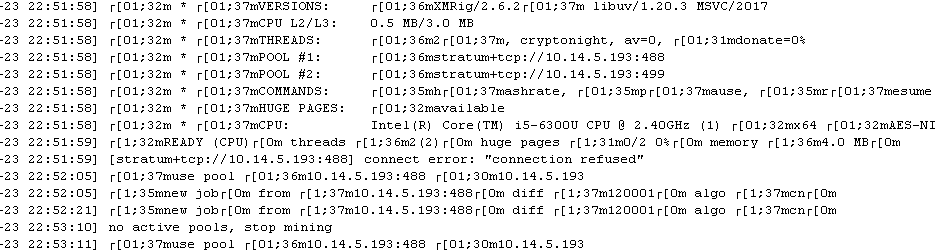
Activities are then logged in to the log.dat file and may look like this:
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: XMRig.MP (Trojan)
- GAV: Miner.XM (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.




