Dustman malware overwrites logical drives data with "************** Down With Saudi Kingdom, Down With Bin Salman **************"
SonicWall Capture Labs Threats Research team has analyzed Dustman malware whose code has similarity with “ZeroCleare” malware and it is suspected to be developed by Iranian hackers. The malware is a 64-bit console executable which contains three encrypted binary files in resource:
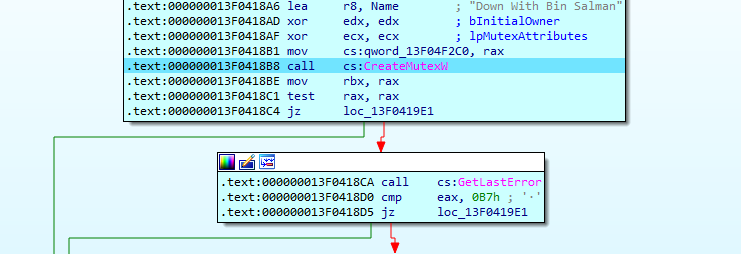
On execution, the malware creates a mutex “Down With Bin Salman” and if the mutex is already exist or Operating System (OS) Major Version is less than 6, then the malware skips service creation code and jumps directly to the code which gets the valid drives strings in the system:
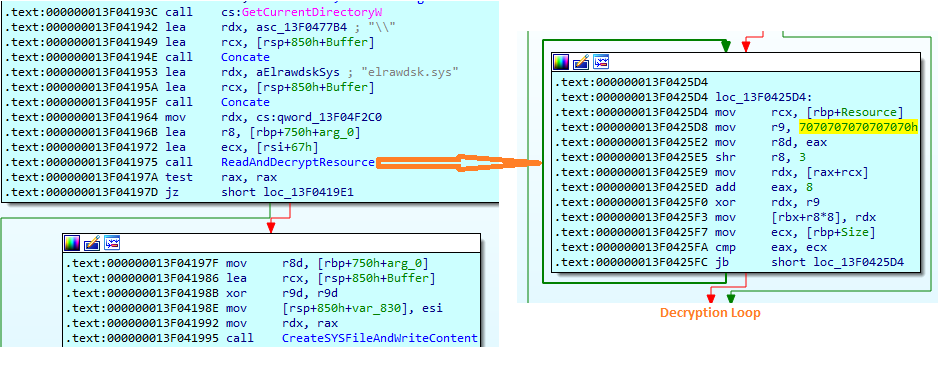
The malware checks, if VirtualBox installed by checking the presence of registry entry “Software\Oracle\VirtualBox” which does not affect the malware execution. The malware now read resource data for resource id “103” in “RCDATA”. The malware decrypts the resource content by performing xor operation with “7070707070707070h” and writes decypted content into “Current Working Directory (CWD)\elrawdsk.sys”:
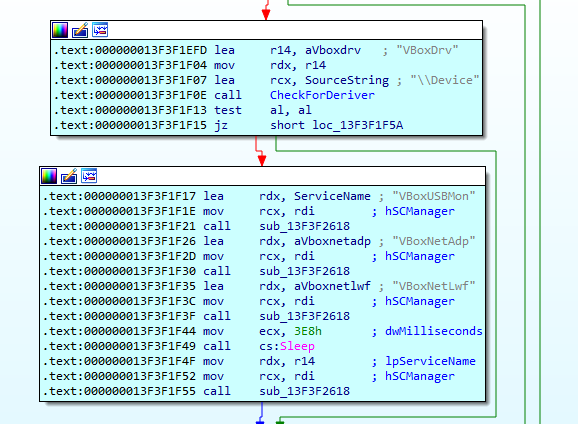
The malware checks for device “VBoxDrv”, if already present the malware then sends service stop request for services “VBoxUSBMon”, “VBoxNetAdp” and “VBoxNetLwf”:
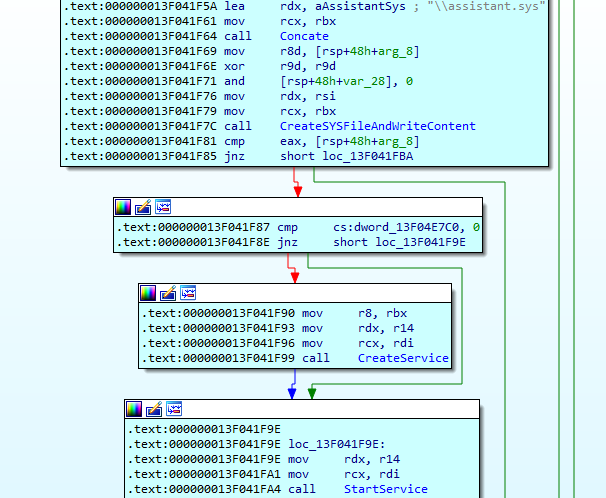
The malware uses modified GitHub available “Turla Driver Loader” for bypassing Windows x64 driver signature enforcement to load malicious unsigned driver. The malware reads resource data for resource id “1” in “RCDATA” and decrypts the resource data to get the modified “Turla Driver Loader” using previously mentioned decryption logic and copy it, to “CWD\assistant.sys”: The malware register “CWD\assistant.sys” as “VBoxDrv” service and starts the service. This modified “Turla Driver Loader” is responsible for loading malicious unsigned driver “CWD\elrawdsk.sys”.
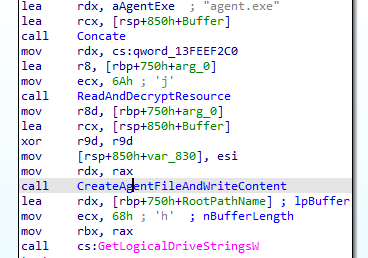
The malware now reads resource data for resource id “106” in “RCDATA” and decrypts the resource data using previously mentioned decryption logic and writes the decrypted data to “CWD\agent.exe”:
The malware gets the valid logical drives strings in the system and if drive types is either “DRIVE_REMOVABLE” or “DRIVE_FIXED” then the malware executes “CWD\agent.exe” passing each drive string as argument which is responsible for overwriting the drives data:
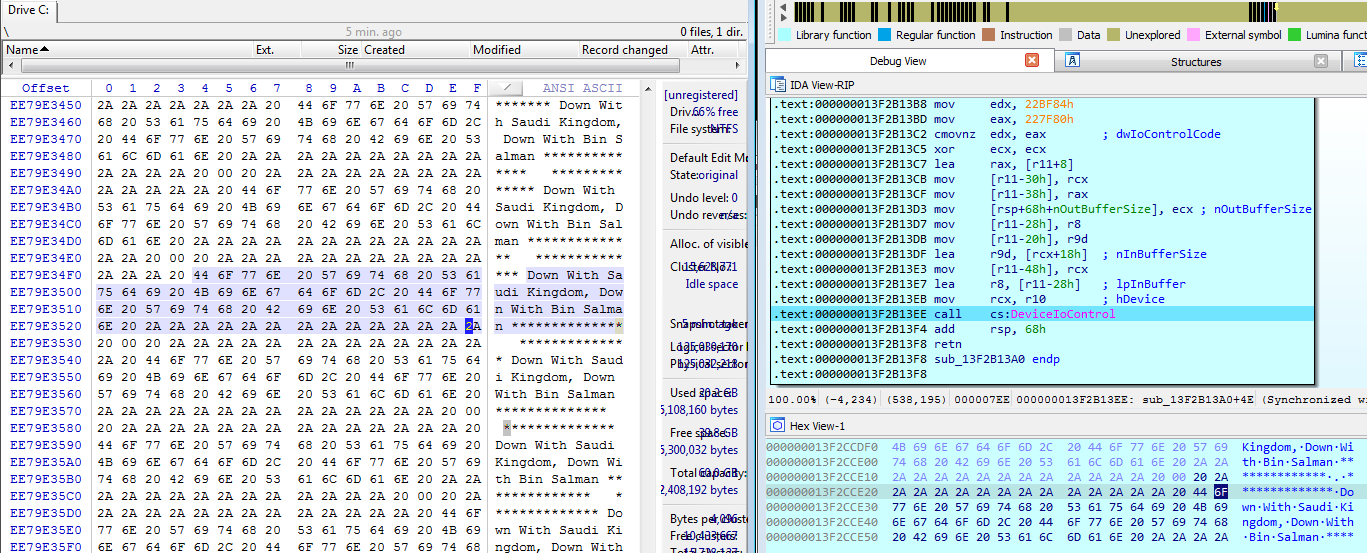
The “agent.exe” sends the buffer which contains message “************** Down With Saudi Kingdom, Down With Bin Salman **************” to its component driver (CWD\elrawdsk.sys) which overwrites logical drive data with the buffer data:
SonicWall Capture Labs provides protection against these threats with the following signatures:
- Dustman.A
- Dustman.A_2
- Dustman.SYS
- Dustman.SYS_2