Using some photo editing apps on Android might infect you with Adware
SonicWall Threats Research Team found a few Photo editor applications which were distributed via Google Play Store. Upon analysis, these apps were found to be Adware. These apps are no longer available in the Google Play Store as these have been removed after we reported about these apps to the concerned team.
Reported malicious apps are shown below:
All the applications have similar functionality though the developer name is different. The number of downloads of these apps, indicate many users might be affected.
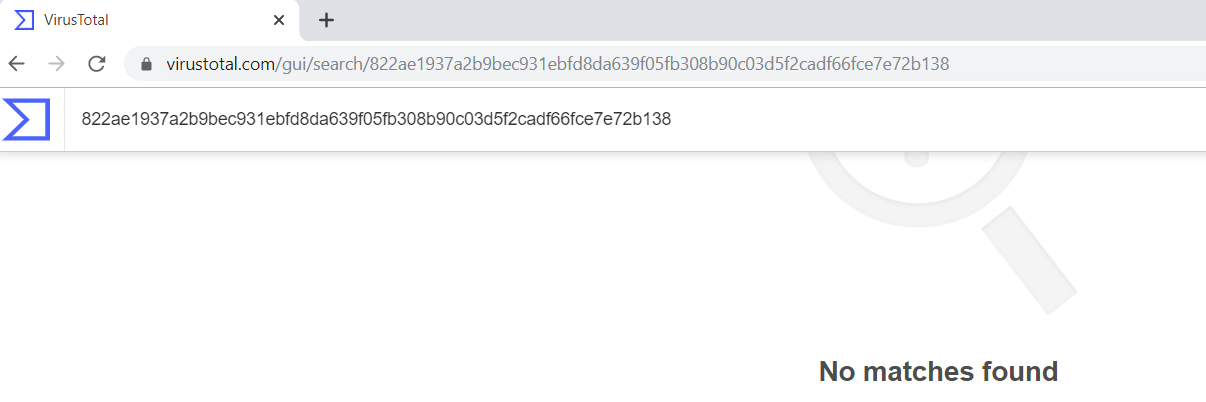
The malicious file is not available on popular threat intelligence portals like the VirusTotal which indicates the uniqueness of the samples:
INFECTION CYCLE:
Some of the permissions requested by these apps which could give access to user’s sensitive data are listed below:
- INTERNET
- READ SETTINGS
- ACCESS FINE LOCATION
- READ PHONE STATE
- READ EXTERNAL STORAGE
- WRITE EXTERNAL STORAGE
- WAKE LOCK
Upon installation, the app appears on the app drawer as shown below:
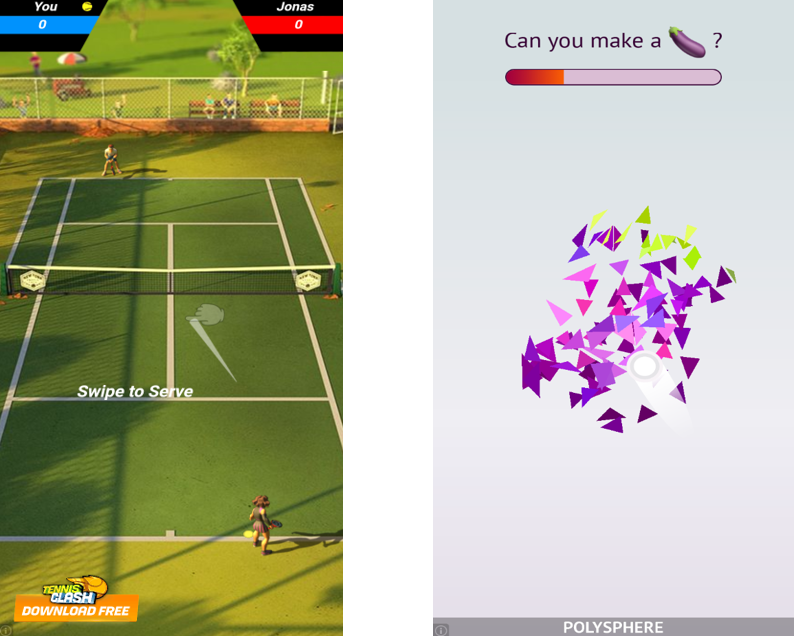
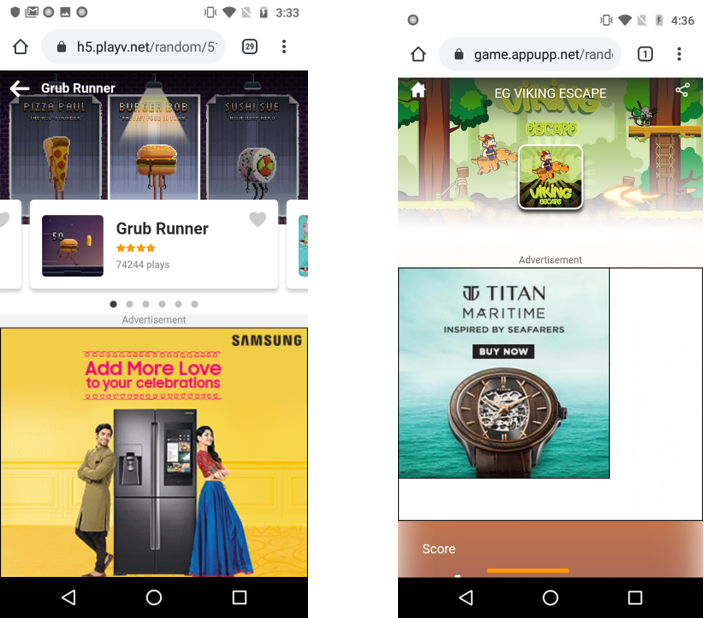
Upon launching the application, an alluring screen is presented to the user to appear a genuine photo editing application. Later, it starts showing full screen Ads with no close button as shown below:
NETWORK COMMUNICATION:
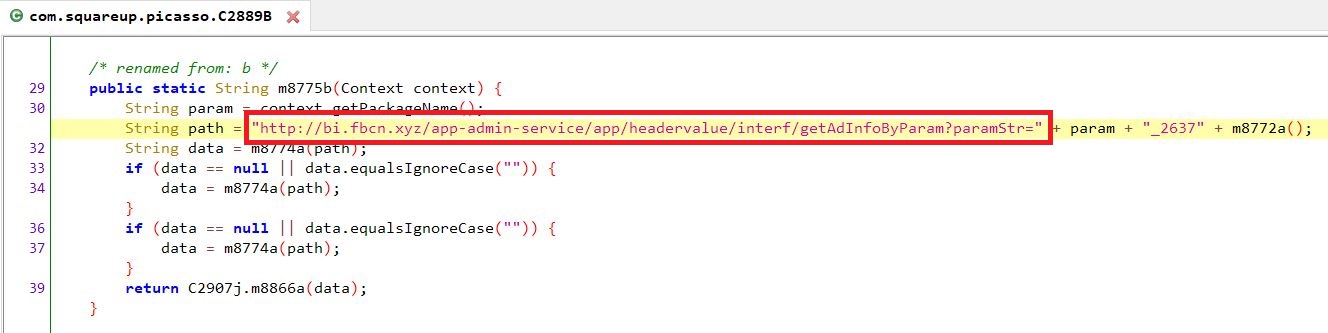
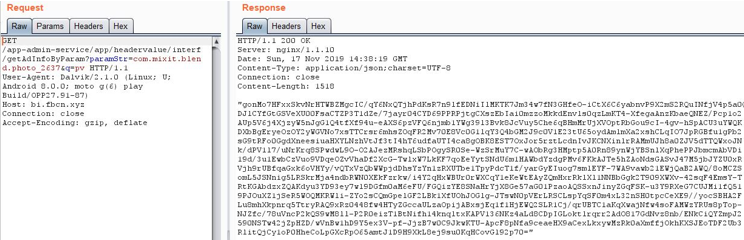
While Ads are displayed to the user, the app requests for a resource from malicious web server. The response data contains list of Ad serving URLs in the encrypted form as shown below:
(Code Snippet)
(Request & Response)
UNVEILING RESPONSE DATA:
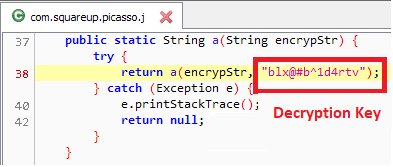
The key to decrypt the encrypted response data is present in the code itself. The decrypted data contains list of Ad serving URLs, parameters which are used to compute the Ad display time:
The ‘egt’ parameter with value 10 when multiplied with 1000 gives the Ad display time in milliseconds. The ‘al2’ and ‘cts’ parameters which contains list of URLs are loaded in the browser:
(code snippet for URL loading)
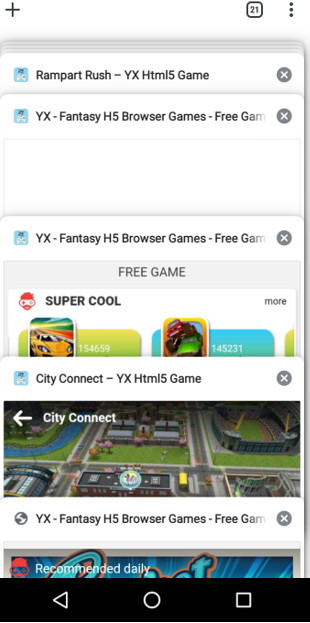
Ads keep popping up in new tabs whenever web browser is launched as shown in the following image:
The app hides its icon from the device which makes it difficult for the user to identify the app responsible for the activity:
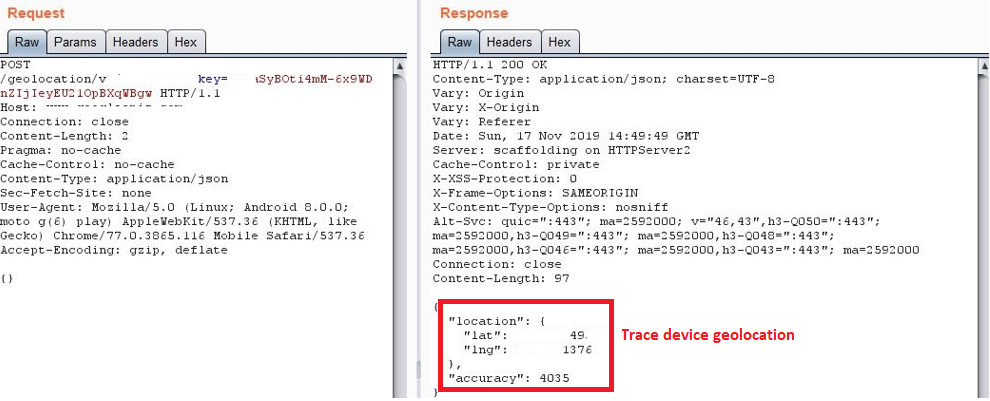
The user’s device location is traced to display geo-location specific Ads:
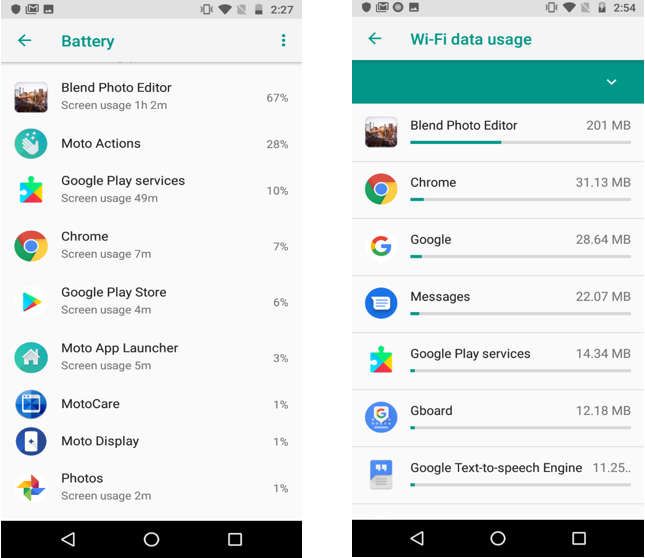
Like any other Adware application, it not only annoys the user by showing Ads at regular intervals, but also drains the battery, consume bandwidth and other resources:
(code Battery and Bandwidth consumption by the app)
Currently these apps are no longer present on the Play Store. However if these apps were installed before they were removed from the Play Store we advise users to uninstall them from their devices.
SonicWall Capture Labs provides protection against this threat with the following signature:
- AndroidOS.HiddenAds.D (Adware)
Indicators Of Compromise (IOC’s) :
- 822ae1937a2b9bec931ebfd8da639f05fb308b90c03d5f2cadf66fce7e72b138
- bbe60005d5104d917f4ce56b1cd145537e84509e9bb7807b7597bddd3a4308a8
- 4d15fee618798efba7b6cda5575236e761fcde5a58168877b7e7e02bfb9f6439
- 7f8faa0fff45fa40668cd935c1da632d2707756e7563f0648842dfb4dc76505f
- 0d6ea8a13bbb87482fee12fc88db958a8b103c952dc05896afc8a552625dcec2