Jigsaw ransomware variant: Melka, easily reveals decryption key
The SonicWall Capture Labs Threat Research Team observed reports of another variant of the Jigsaw ransomware spreading in the wild. The malware is written in .NET and appears to be Czech in origin. Payment is to be made in bitcoin although it is unclear how much is required for file decryption.
Infection cycle:
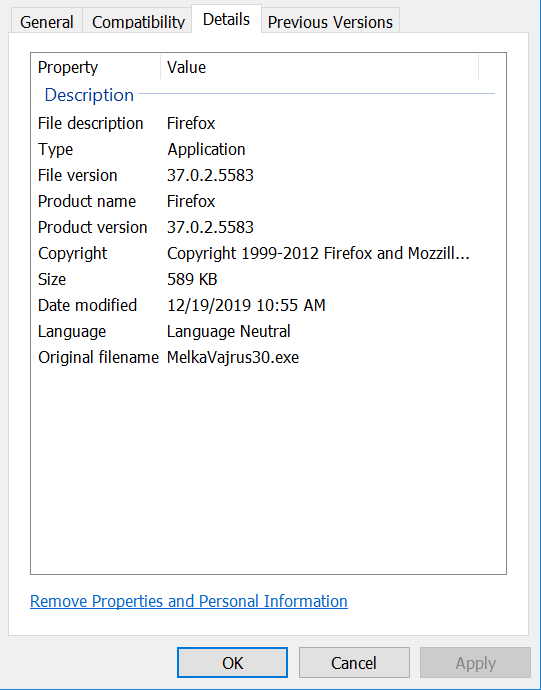
The malware executable file contains the following metadata:
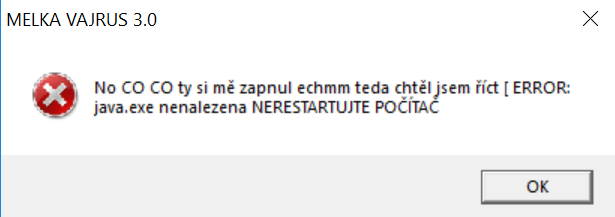
Upon execution the following messagebox is displayed:
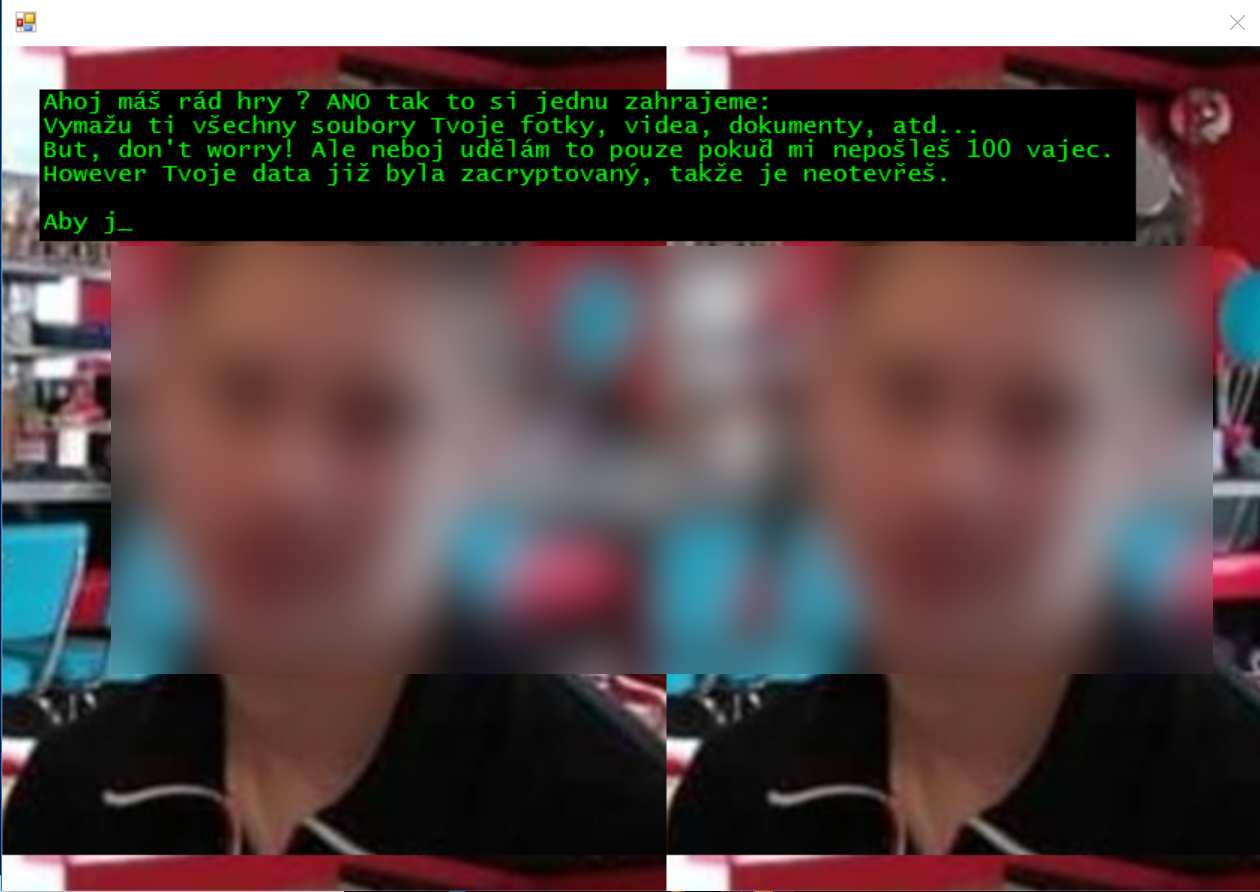
The malware encrypts files in the background and gives each file a .fun extension. After this the following dialog is displayed with text emerging character by character:
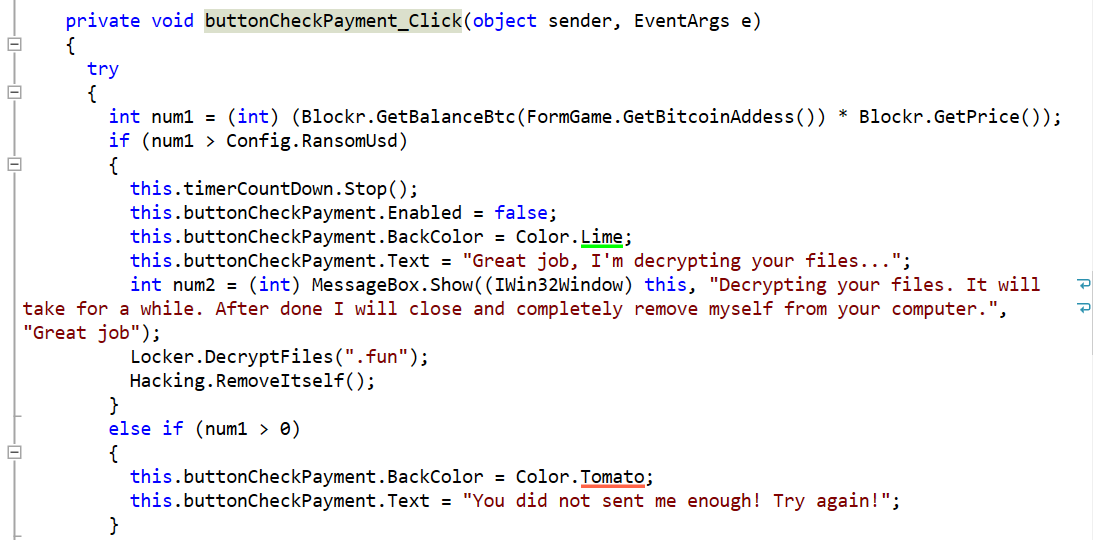
After the full message is displayed, a 1 hour countdown is started. The ransom demand translates to a payment of 100 eggs. We’re not sure what this means:
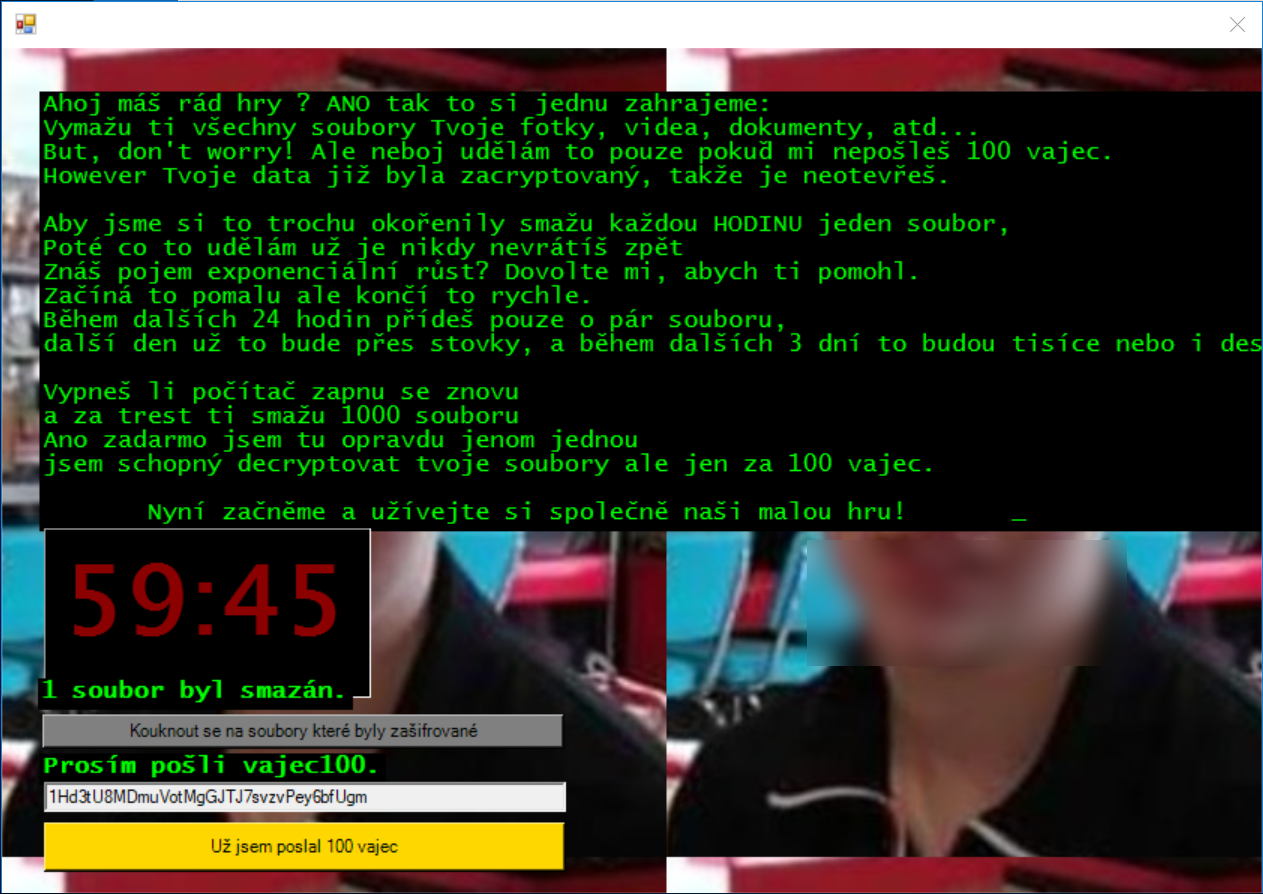
The dialog also provides a list of files that were encrypted:
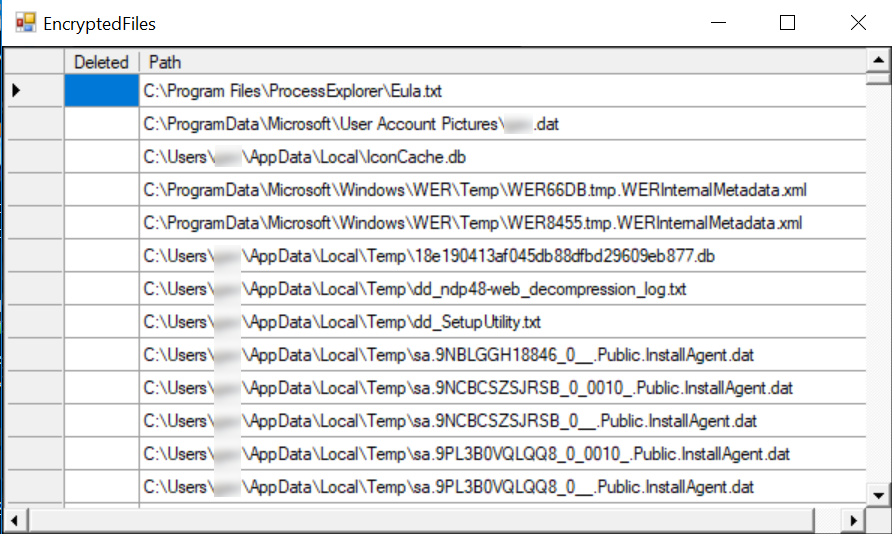
The following files are added to the system:
- %APPDATA%\System32Work\Address.txt (contains bitcoin address: 1Hd3tU8MDmuVotMgGJTJ7svzvPey6bfUgm)
- %APPDATA%\Frfx\firefox.exe (copy of original malware file [Detected as: GAV: Melka.RSM (Trojan)])
- %APPDATA%\System32Work\dr (contains “21“)
- %APPDATA%\System32Work\EncryptedFileList.txt (a list of files that were encrypted)
The following registry key is added:
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run firefox.exe “%APPDATA%\Frfx\firefox.exe”
The malware is written in .NET. A quick decompilation of the malware reveals various routines involved in the encryption and decryption process:
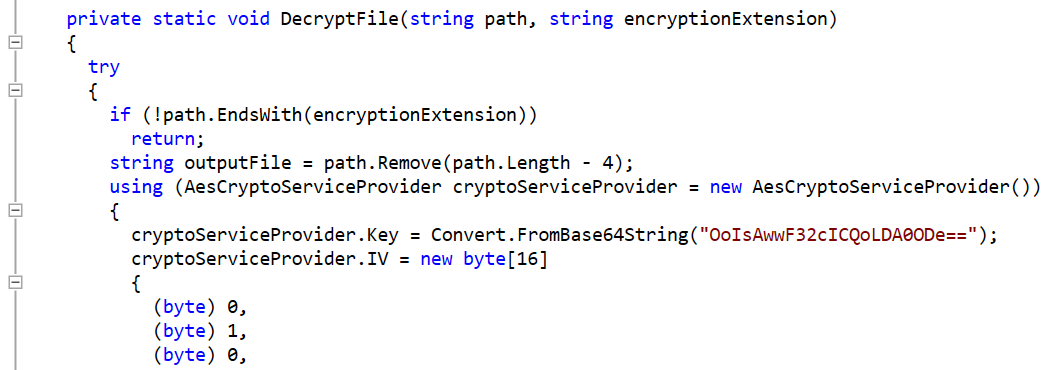
The decryption routine is also easy to find and the decryption key (“OoIsAwwF32cICQoLDA0ODe==”) easily revealed:
Further analysis also reveals a list of file extensions that are used to identify files to encrypt:
.jpg .jpeg .raw .tif .gif .png .bmp .3dm .max .accdb .db .dbf .mdb .pdb .sql.dwg .dxf .c .cpp .cs .h .php .asp .rb .java .jar .class .py .js .aaf .aep.aepx .plb .prel .prproj .aet .ppj .psd .indd .indl .indt .indb .inx .idml.pmd .xqx .xqx .ai .eps .ps .svg .swf .fla .as3 .as .txt .doc .dot .docx .docm.dotx .dotm .docb .rtf .wpd .wps .msg .pdf .xls .xlt .xlm .xlsx .xlsm .xltx.xltm .xlsb .xla .xlam .xll .xlw .ppt .pot .pps .pptx .pptm .potx .potm .ppam.ppsx .ppsm .sldx .sldm .wav .mp3 .aif .iff .m3u .m4u .mid .mpa .wma .ra .avi.mov .mp4 .3gp .mpeg .3g2 .asf .asx .flv .mpg .wmv .vob .m3u8 .mkv .dat .csv.efx .sdf .vcf .xml .ses .rar .zip .7zip@
The following strings are also present in the executable file thus identifying it as a Jigsaw ransomware variant:
C:\Users\Admin\Desktop\Melka_vajrus30\JigsawRansomware\JigsawRansomware\obj\Release\MelkaVajrus30.pdb
TxtTest.txt
I am a txt test.
NotTxtTest.nottxt
I am NOT a txt test.
EncryptedFileList.txt
SonicWall Capture Labs provides protection against this threat via the following signatures:
- GAV: Melka.RSM (Trojan)
- GAV: Jigsaw.RSM_26 (Trojan)
This threat is also detected by SonicWALL Capture ATP w/RTDMI and the Capture Client endpoint solutions.




