Dridex Malware evading detection using delaying techniques
SonicWall Capture Labs Threats Research Team has spotted Dridex malware attacks in the wild. This malware is delivered through phishing emails.
Dridex is an info stealer which tries to steal credentials such as ComputerName, RunningProcess and System Information and send this information to C&C server. Dridex malware is famous for using different technique for encoding and obfuscating data. In this case it uses below technique for delaying the actual execution of the payload.
Infection Cycle
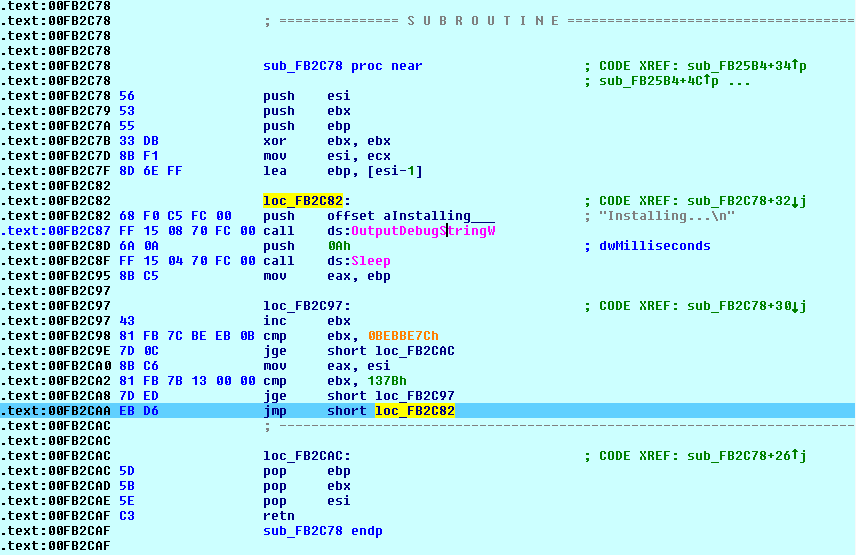
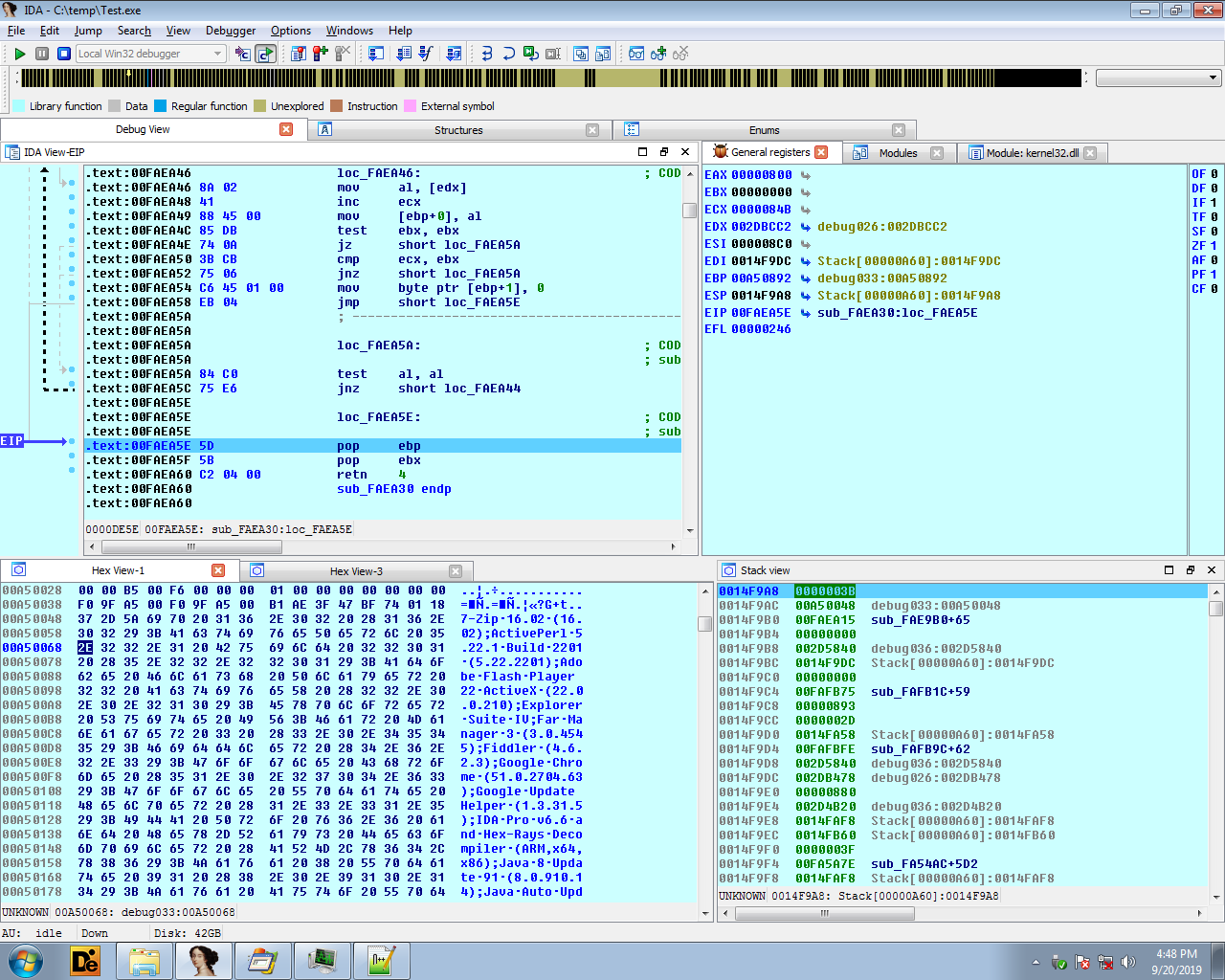
After few instructions from the EntryPoint it calls a function sub_FB2C78 containing the loop which calls OutputDebugStringW by passing “Installing…\n” as string and then calls Sleep API for 10 millisecond. The loop is iterated 199999100 * 4987 times.
During the course of execution this function is called four times and it also calls NtDelayExecution API,
so as to defeat the sample automation as well as sandbox which rely on specific timeout for analyzing the malware activity.
Using FindFirstFileExW and FindNextFileW APIs it searches %system32% directory for *.dll. When it finds the required DLL it uses NTDLL_LdrLoadDll native APIs to load it.
For system profiling it calls the below APIs
- Process Token Access
- OpenProcessToken
- GetTokenInformation
- AllocateAndInitializeSid
- EqualSid
- FreeSid
- RtlQueryElevationFlags
- GetSystemInfo
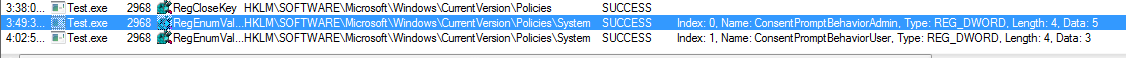
It uses Registry related APIs such as SHRegDuplicateHKey, RegEnumKeyW, RegEnumValueA. Also, it checks values of the key below:
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\
“ConsentPromptBehaviorAdmin”
“ConsentPromptBehaviorUser”
These values are used for checking the Administrative privileges.
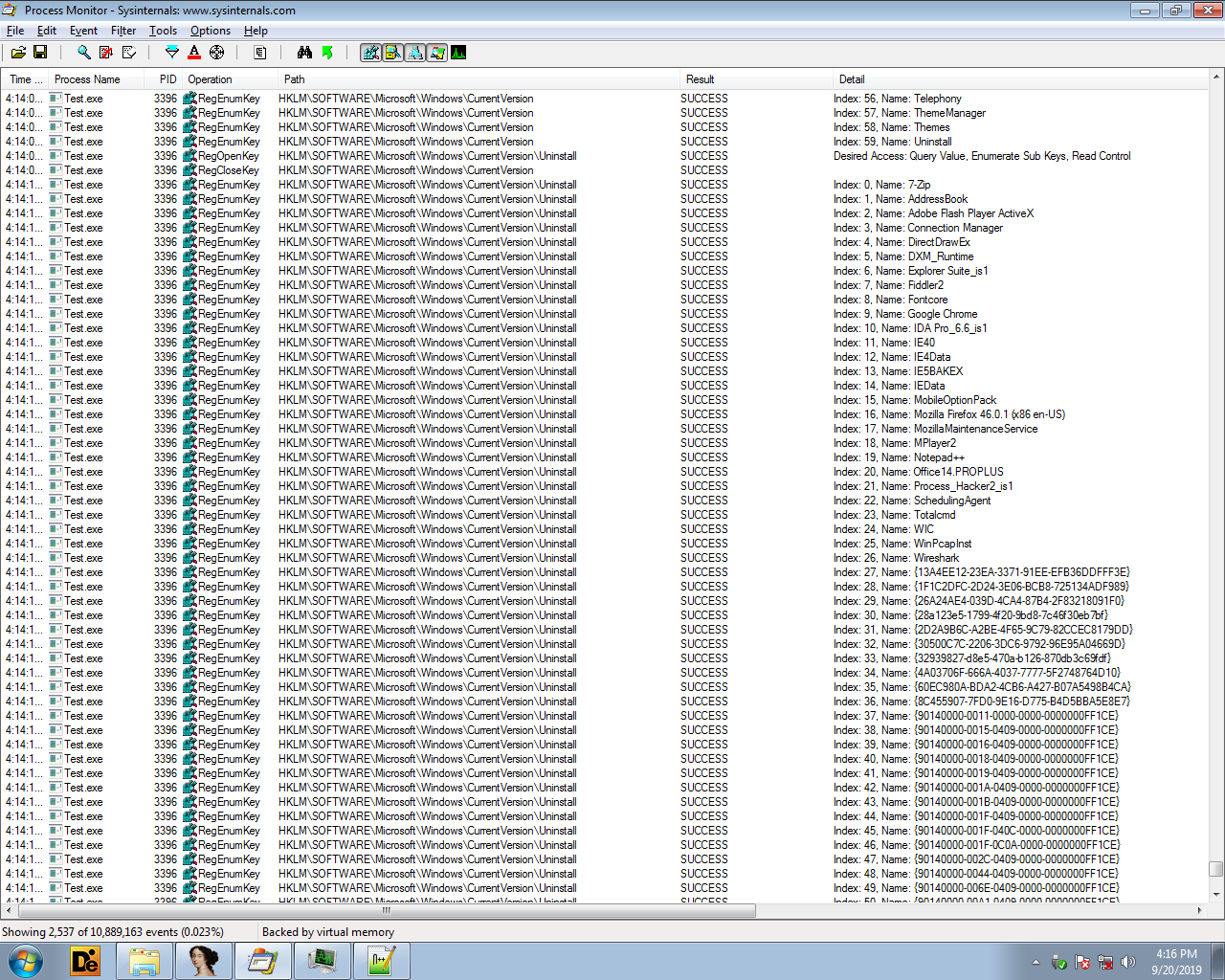
It enumerates the below registry key to get the list of software installed on the system:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall
The malware calls several API functions to collect information such as Windows version information, system and CPU information.
It also collects the names of the running processes and encrypts all the information before sending it to the remote server.
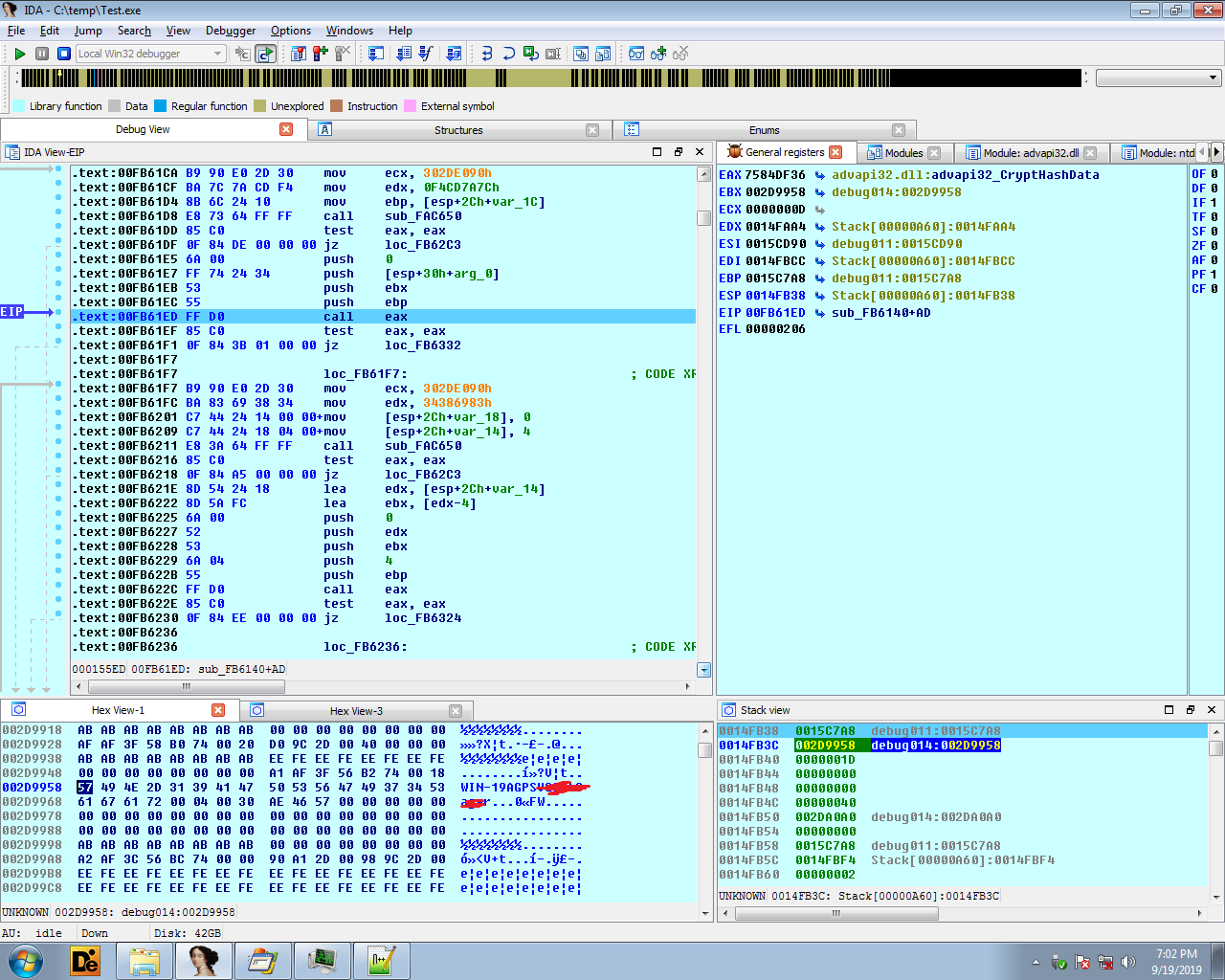
It uses GetComputerName and GetEnvironmentVariableW APIs to find the ComputerName and UserName respectively. Which is then concatenated and uses CryptAcquireContextW(), CryptCreateHash(), CryptHashData() and CryptGetHashParam() API calls to generate the MD5 of it.Which is then used to create the Mutex.
Network Activity
The server list is hardcoded in the unpacked executable file:
-
- 104.247.221.104:443
- 198.199.106.229:5900
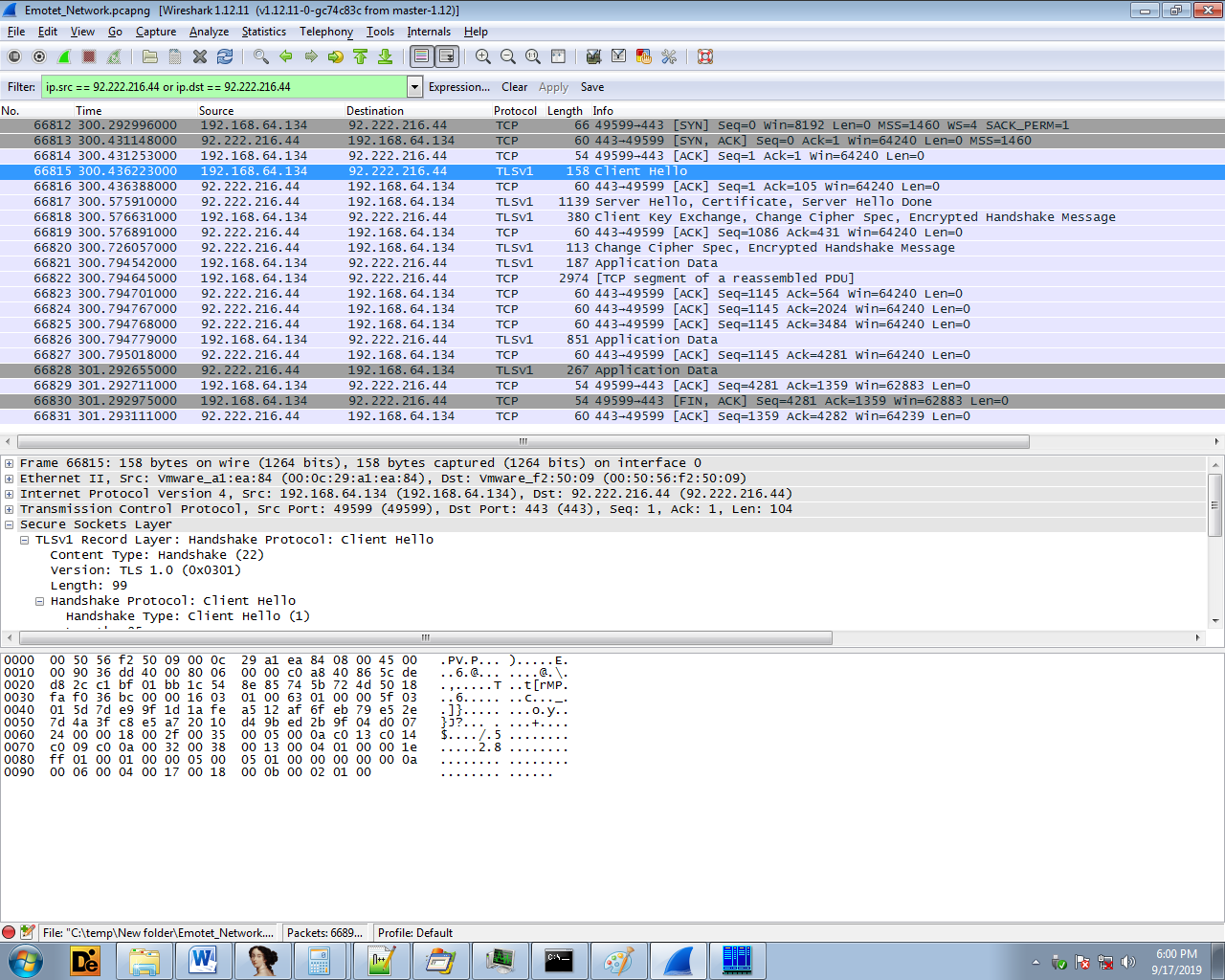
- 92.222.216.44:443
Using InternetOpenA, InternetConnectA, it tries to connect to one of the server on the mentioned port in the list with NULL field in the Username and Password field.
It uses HttpOpenRequestW API with lpszVerb ‘POST’ and lpszObjectName with ‘/’ for creating HTTP request handle.
While writing the blog the sample tried to establish secure connection with only one of the IPs mentioned above:
Sonicwall Capture Labs provides protection against this threat with the following signature:
- MalAgent.GR (Trojan)
Indicators of Compromise:
- d013d1ba2fd45429ed679504f5ce6c9a